Have you ever stumbled upon a message on Instagram prompting you to click on a link, claiming to unveil who viewed your profile or shared a post that seems a little too intriguing? Beware, as this might be the doorway to the Instagram Virus scam, a sophisticated plan designed to hijack personal information and compromise account security.
This article peels back the layers of deceptive strategies ranging from phishing attempts to malicious software, guiding you through the signs of compromise and offering invaluable advice on safeguarding your account against these digital predators. With cyber threats becoming more advanced, learning how to fortify your online presence on social platforms like Instagram is no longer optional—it’s essential.
Dive into our comprehensive guide to understand how these scams operate, their impact, and the proactive measures you can take to ensure your digital well-being.
Instagram Virus Details
| Type | Infostealer, Malware, Trojan, Scam, Phishing, Browser Redirect |
| Removal Time | Approximately 15 minutes for a full-system scan. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
What is the Instagram Virus Scam?
The Instagram Virus scam encompasses a variety of misleading and malicious activities aimed at compromising users’ accounts on the platform. It leverages methods like phishing, malware, and deceitful interactions to trick users into giving their personal information, clicking on harmful links, or unintentionally spreading the scam further.
This digital threat feeds on users’ curiosity, trust, and desire for social validation, employing sophisticated tactics to achieve its malicious objectives.
The Mechanics of the Instagram Virus Scam
Understanding how the Instagram Virus scam operates is crucial for recognizing and avoiding potential threats. This scam often unfolds through various deceptive tactics designed to manipulate users into compromising their security.
Phishing Attempts and Malicious DMs
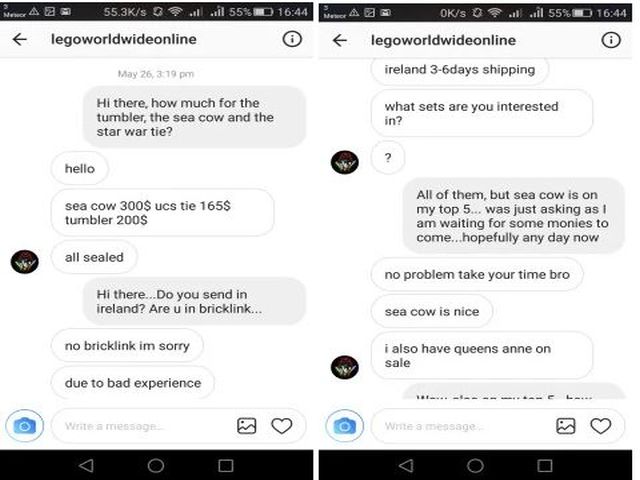
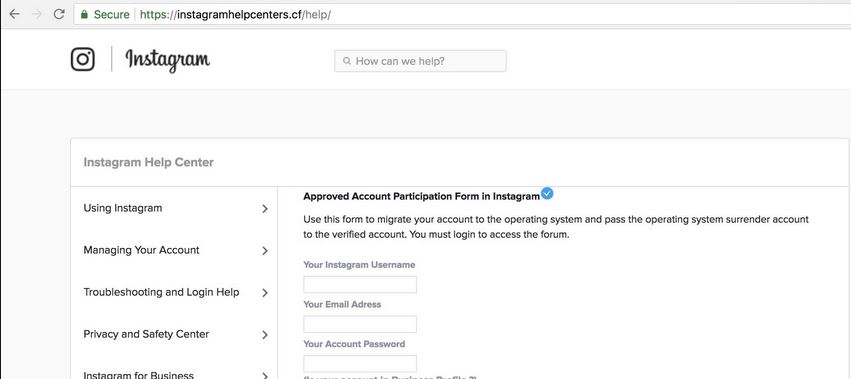
Phishing is a common technique used in these scams, where attackers send direct messages or emails that appear legitimate but contain malicious links. When a user clicks on these links, they are directed to fake login pages that capture their credentials. The language in these messages often creates a sense of urgency or curiosity, such as claiming you’ve appeared in a “shocking video” or offering exclusive content if you click the link.
Third-Party App Risks
Some scams promote third-party apps promising additional Instagram features, like seeing who viewed your profile. These apps may require login details or access to your Instagram account, posing a significant security risk. They can use this access to gather personal information, send spam from your account, or further propagate the scam.
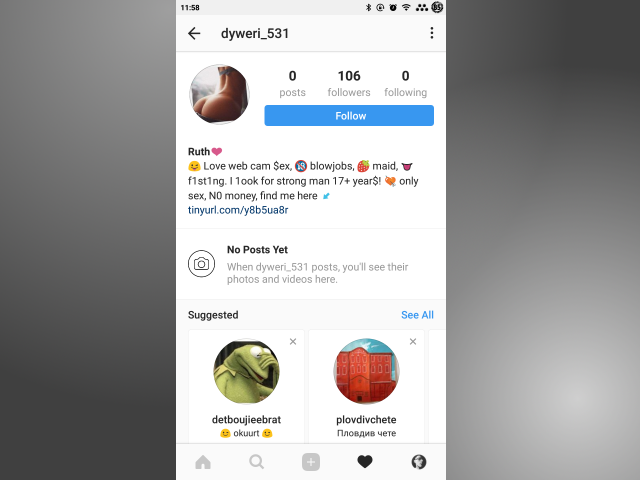
Profile Impersonation and Fake Followers
Scammers may create fake profiles impersonating real users or celebrities to spread their scams.
They lure users with offers or engage in interactions that eventually lead to scamming attempts. Additionally, scams involving fake followers or likes prey on the desire for popularity, tricking users into engaging with harmful links or fraudulent services.
Key Indicators of the Instagram Virus Scam
Spotting signs of the Instagram Virus scam early can prevent potential harm. Here are some key indicators that suggest your account may be targeted or compromised:
Unexpected Activity on Your Account
If you notice posts, messages, or follows that you don’t remember making, your account may have been compromised. This unexpected activity often indicates that someone else has gained access to your account.
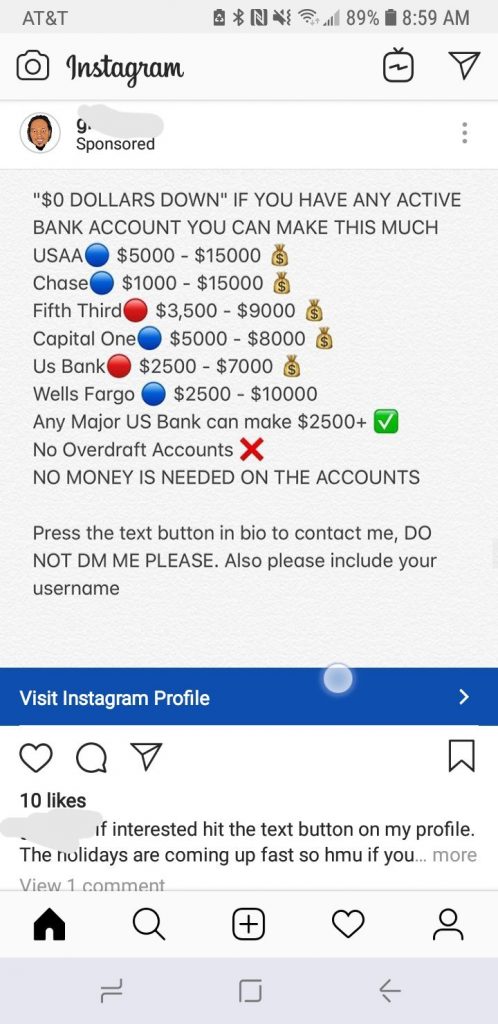
Messages You Didn’t Send
Finding direct messages in your sent box that you did not send is a clear sign of account compromise. These messages may contain spam, links to phishing sites, or other harmful content aimed at spreading the scam to your contacts.
Sudden Spike in Followers or Likes
An unusual increase in followers or likes, especially from accounts that seem fake or irrelevant, could indicate that your account is involved in a scam operation. Scammers sometimes boost engagement as a tactic to make their operations appear more legitimate or appealing.
On noticing any of these signs, it is advisable to change your password immediately, revoke access to suspicious third-party apps, and enable two-factor authentication for added security. For comprehensive protection, consider installing security software like SpyHunter, which can safeguard your device against malware and other threats potentially encountered on Instagram and other social platforms.
How Does the Instagram Virus Scam Affect You?
Understanding the full impact of the Instagram virus scam is essential for users who treasure their online presence and privacy. This section breaks down the various ways these scams can harm you, emphasizing the importance of vigilance and proactive security measures.
Risks to Personal Information and Privacy
At the forefront of concerns associated with the Instagram virus scam is the risk it poses to your personal information and privacy. Hackers use sophisticated phishing scams designed to trick you into divulging sensitive details.
These details can include login credentials, which they can use to gain unauthorized access to your accounts. Moreover, some scams go as far as asking for personal identification details, leading to identity theft and financial fraud. Losing control over your personal information on such a vastly interconnected platform can have immediate and long-lasting effects on your life.
Compromised Account Security
The integrity of your social media account is paramount. Yet, the Instagram virus scam directly threatens this by exploiting loopholes and deceiving users into compromising their own account security. Once hackers gain access to your account, they can manipulate, delete, or otherwise tamper with your content.
This unauthorized access not only jeopardizes your personal and private information shared through the platform but also opens up a gateway for the spread of the scam, making your followers vulnerable to similar threats. Implementing robust security measures, like strong passwords and two-factor authentication, can significantly mitigate these risks.
Additionally, engaging with a trusted security solution, such as SpyHunter, can offer an added layer of protection against potential threats by identifying and removing malicious software before it can cause harm.
Impact on Digital Reputation
Your digital reputation, once tarnished, can be difficult to restore. This is particularly true in the event of falling victim to the Instagram virus scam. Hackers can use your account to disseminate spam or malicious content, damaging your reputation among followers and peers.
The situation can become even more complicated if your account is used to scam others, as it places you in an unfavorable light, potentially leading to a loss of trust that can have ripple effects beyond just your online presence. Keeping a vigilant eye on account activity and educating yourself on the latest security practices play a crucial role in safeguarding your digital reputation from such scams.
Steps to Take If You Suspect an Instagram Virus Scam
Identifying and reacting promptly to an Instagram virus scam is crucial for safeguarding your account against hackers and malicious software. The moment you suspect your account has been compromised, certain immediate measures can significantly mitigate the risks and protect your digital presence. Follow these essential steps to secure your account and report the scam effectively.
Immediate Actions to Secure Your Account
Change Your Password Immediately
If you suspect a security breach, the first actionable step is to change your Instagram password without delay. Opt for a strong password that features a mix of letters, numbers, and symbols to enhance security. If you use the same or a similar password on other platforms, it’s wise to change those as well to prevent cross-platform vulnerabilities.
Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your account by requiring a second form of verification beyond your password, typically a code sent to your mobile device.
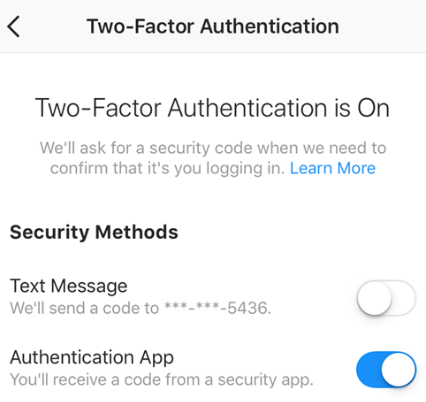
Enabling 2FA on Instagram can significantly deter unauthorized access, ensuring that even if your password is compromised, the additional verification step can still protect your account.
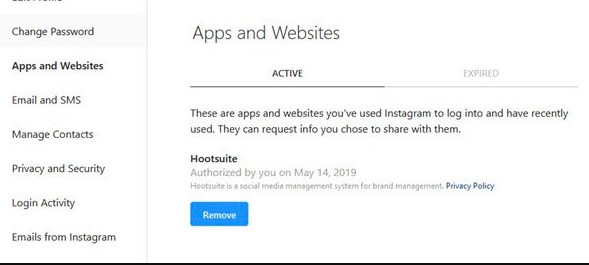
Revoke Access to Suspicious Third-Party Apps
Review the third-party apps that have access to your Instagram account. If you notice any apps that you don’t recognize or no longer use, revoke their access immediately. Unauthorized or malicious apps can be a gateway for hackers to compromise your account and steal personal information.
How to Report the Scam to Instagram
If your account has been targeted or compromised by a phishing scam or any form of malicious activity, reporting it to Instagram is essential. Use the ‘Report a Problem’ feature within the app to detail the issue. Include any relevant information and screenshots of suspicious activity to help the Instagram security team understand and address the issue more efficiently.
Following your report, stay vigilant for any follow-up instructions or recommendations from Instagram to ensure your account’s security is fully restored.
Protecting your account from an Instagram virus scam requires a proactive approach to security. Regularly update your password, enable two-factor authentication, and stay cautious of suspicious links or requests.
In situations where your security may be compromised, taking immediate action and alerting the platform can help prevent further damage.
For those seeking additional protection against such threats, consider using security software like SpyHunter to help safeguard your devices and personal information from malicious attacks.
Remember, in the digital age, staying informed about potential threats and knowing how to react can make all the difference in protecting your online presence and personal data.
Preventative Measures to Avoid Falling for the Instagram Virus Scam
As Instagram continues to be a leading social media platform, the risk of encountering the Instagram virus scam also increases. Protecting yourself necessitates a proactive approach, combining education on social engineering tactics and implementing best practices for account security.
Educate Yourself About Social Engineering Tactics
Understanding the psychology behind scams is your first line of defense against the Instagram virus. Social engineering tactics exploit human psychology rather than technical hacking techniques to gain access to people’s personal information or accounts.
The Role of Awareness in Preventing Scams
Being aware of the common tricks scammers use can help you stay one step ahead. Scammers often create a sense of urgency or appeal to your emotions to trick you into acting against your better judgment. By staying informed about these tactics, you can better protect yourself from falling victim to them.
Recognizing Phishing Attempts and Malicious Links
Phishing attempts and malicious links are common tools used by scammers. These can appear as messages from friends, family, or even Instagram itself. Learning to recognize these attempts is crucial:
- Be cautious of messages that ask you to click on a link or provide personal information.
- Look out for spelling and grammar mistakes, which are often present in scam messages.
- Verify the authenticity of the message by contacting the sender directly through another communication method.
Best Practices for Instagram Account Security
Securing your Instagram account involves more than just being aware of scams. Implementing strong security practices can significantly reduce your risk of falling victim to the Instagram virus.
Creating Strong and Unique Passwords
A strong password is your first defense against unauthorized access to your account. Ensure that your password is complex, including a mix of letters, numbers, and special characters. It’s also essential to use unique passwords for different accounts to prevent a domino effect if one gets compromised.
Regularly Monitoring Account Activity
Regularly checking your account activity can help you spot any unusual behavior early on. Instagram provides tools to see where your account has been accessed from and on what devices. If you notice anything suspicious, change your password immediately and review your security settings.
In addition to these steps, consider using security software to add an extra layer of protection. SpyHunter offers robust defenses against malware and phishing attempts, ensuring your digital safety on Instagram and beyond. By staying informed and implementing these security measures, you can enjoy a safer Instagram experience free from the worries of the Instagram virus scam.
Why Regular Scanning and Security Software Like SpyHunter are Essential
In an age where digital threats evolve rapidly, the importance of maintaining robust online security cannot be overstated. Regular scanning and the use of comprehensive security software like SpyHunter are pivotal practices for safeguarding your social media profiles, including Instagram, against diverse malware and scams. These tools are not just about protection; they’re about ensuring a seamless and safe online experience.
The Benefits of Using SpyHunter for Social Media Security
SpyHunter is designed with the user’s digital safety at its core, providing a multitude of benefits specifically tailored to enhance social media security.
Real-time Protection Against Malware and Scams
Real-time protection serves as a constant guard, monitoring your social media activities to block malicious threats before they can do harm. This proactive security measure is critical for defending against the immediate danger presented by phishing scams and malware distribution on platforms like Instagram.
Automatic Detection and Removal of Threats
With advanced algorithms, SpyHunter excels in identifying and eliminating threats. From sophisticated phishing attempts to malware designed to compromise your social media accounts, SpyHunter’s automatic detection and removal capabilities simplify the process of maintaining your digital hygiene. This not only saves time but also reduces the risk of manual error during the removal process.
Understanding the vital role that tools like SpyHunter play in securing your online presence is crucial. By implementing regular scans and employing real-time protection, you’re taking significant steps towards ensuring that your social media engagements remain safe and enjoyable, free from the worries of digital threats.
Conclusion: Staying Vigilent is Key
In an era where digital footprints are as common as physical ones, staying vigilant on platforms like Instagram is not just advisable, it’s essential.
With the increasing sophistication of cyber threats and the persistent vulnerabilities within social media platforms, users must take proactive steps to safeguard their digital presence. This goes beyond the basics of choosing strong passwords and extends to a comprehensive understanding of potential risks and the implementation of robust security measures.
Firstly, keeping your Instagram account secure means staying informed about the potential threats and understanding the best practices for digital safety.
This includes recognizing phishing attempts, securing your account with two-factor authentication, and being cautious about the third-party apps you grant access to your Instagram. However, even with these precautions, vulnerabilities can still be exploited as demonstrated by the research from Check Point, highlighting the need for continuous vigilance.
For those instances where the in-built security measures of platforms like Instagram fall short, dedicated security software becomes an indispensable ally.
SpyHunter, with its advanced security features, offers an added layer of protection against malware and potential hacks that prey on social media vulnerabilities. It’s designed to provide real-time monitoring and removal of threats, thereby enhancing a user’s defense against the sophisticated exploits that could compromise personal data.
Equally important is the role of personal accountability in digital security. Users should regularly review their privacy settings, be mindful of the information they share online, and recognize the signs of compromised security.
Today, the adage ‘better safe than sorry’ has never been more relevant. By taking proactive steps and utilizing tools like SpyHunter for an added security measure, users can enjoy the benefits of social media while minimizing the risks.
In summary, the path to digital safety on Instagram and similar platforms is twofold: personal vigilance and the support of advanced security solutions like SpyHunter. As we navigate the digital landscape, let’s strive for security practices that protect not just our personal information, but also the integrity of our digital community.
Preparation before removing Instagram Virus.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
- Scan for Malware
- Fix Registries
- Remove Virus Files
Step 1: Scan for Instagram Virus with SpyHunter Anti-Malware Tool



Step 2: Clean any registries, created by Instagram Virus on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Instagram Virus there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.Step 3: Find virus files created by Instagram Virus on your PC.
1.For Windows 8, 8.1 and 10.
For Newer Windows Operating Systems
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.

2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.

3: Navigate to the search box in the top-right of your PC's screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be "fileextension:exe". After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.For Windows XP, Vista, and 7.
For Older Windows Operating Systems
In older Windows OS's the conventional approach should be the effective one:
1: Click on the Start Menu icon (usually on your bottom-left) and then choose the Search preference.

2: After the search window appears, choose More Advanced Options from the search assistant box. Another way is by clicking on All Files and Folders.

3: After that type the name of the file you are looking for and click on the Search button. This might take some time after which results will appear. If you have found the malicious file, you may copy or open its location by right-clicking on it.
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software.
Instagram Virus FAQ
What Does Instagram Virus Trojan Do?
The Instagram Virus Trojan is a malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system. It can be used to steal sensitive data, gain control over a system, or launch other malicious activities.
Can Trojans Steal Passwords?
Yes, Trojans, like Instagram Virus, can steal passwords. These malicious programs are designed to gain access to a user's computer, spy on victims and steal sensitive information such as banking details and passwords.
Can Instagram Virus Trojan Hide Itself?
Yes, it can. A Trojan can use various techniques to mask itself, including rootkits, encryption, and obfuscation, to hide from security scanners and evade detection.
Can a Trojan be Removed by Factory Reset?
Yes, a Trojan can be removed by factory resetting your device. This is because it will restore the device to its original state, eliminating any malicious software that may have been installed. Bear in mind that there are more sophisticated Trojans that leave backdoors and reinfect even after a factory reset.
Can Instagram Virus Trojan Infect WiFi?
Yes, it is possible for a Trojan to infect WiFi networks. When a user connects to the infected network, the Trojan can spread to other connected devices and can access sensitive information on the network.
Can Trojans Be Deleted?
Yes, Trojans can be deleted. This is typically done by running a powerful anti-virus or anti-malware program that is designed to detect and remove malicious files. In some cases, manual deletion of the Trojan may also be necessary.
Can Trojans Steal Files?
Yes, Trojans can steal files if they are installed on a computer. This is done by allowing the malware author or user to gain access to the computer and then steal the files stored on it.
Which Anti-Malware Can Remove Trojans?
Anti-malware programs such as SpyHunter are capable of scanning for and removing Trojans from your computer. It is important to keep your anti-malware up to date and regularly scan your system for any malicious software.
Can Trojans Infect USB?
Yes, Trojans can infect USB devices. USB Trojans typically spread through malicious files downloaded from the internet or shared via email, allowing the hacker to gain access to a user's confidential data.
About the Instagram Virus Research
The content we publish on SensorsTechForum.com, this Instagram Virus how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific trojan problem.
How did we conduct the research on Instagram Virus?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of trojans (backdoor, downloader, infostealer, ransom, etc.)
Furthermore, the research behind the Instagram Virus threat is backed with VirusTotal.
To better understand the threat posed by trojans, please refer to the following articles which provide knowledgeable details.


