.vesrato File Virus (STOP Ransomware) – Remove and Restore Data
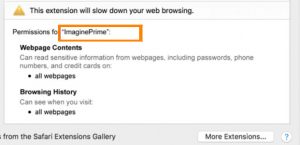
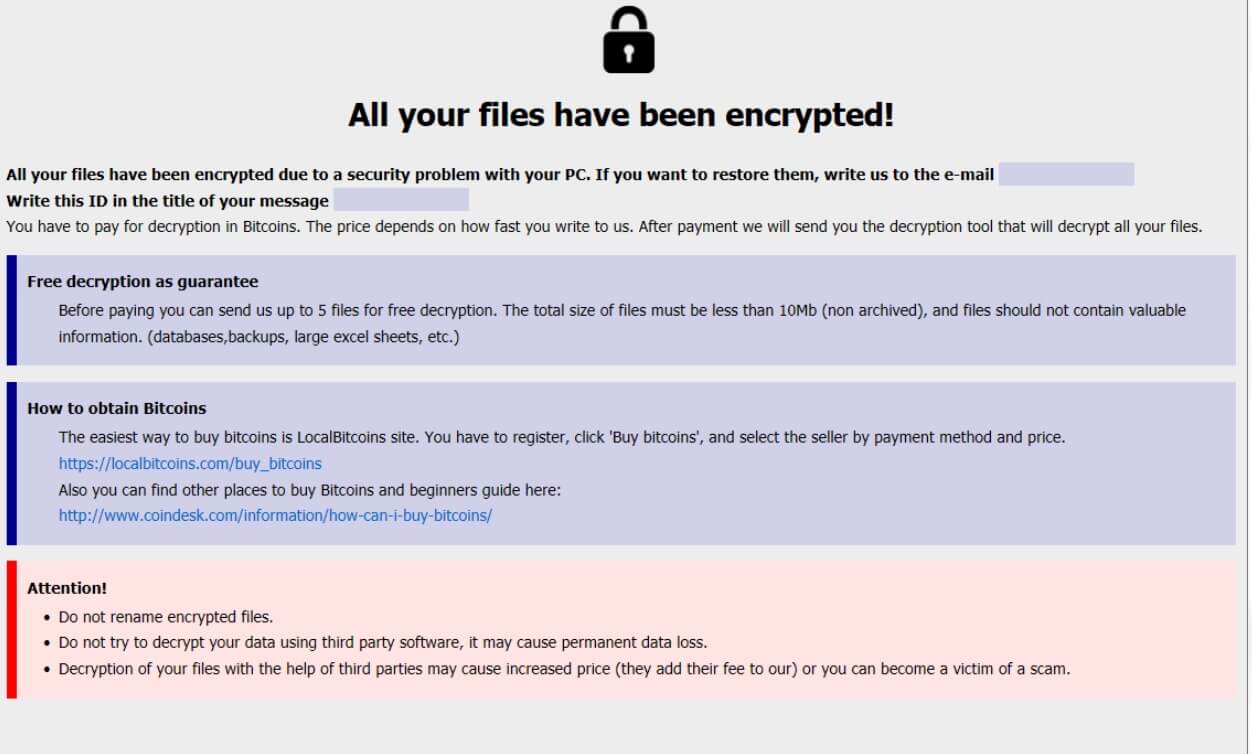
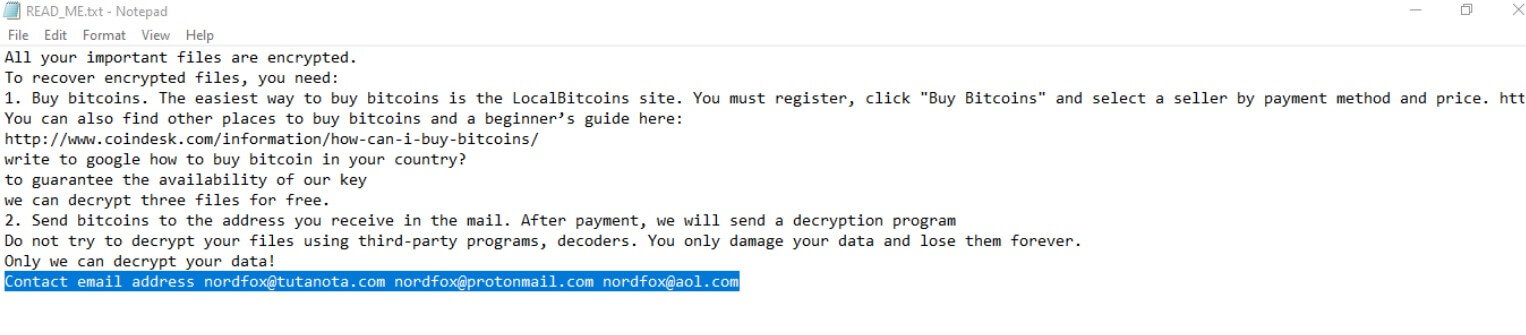
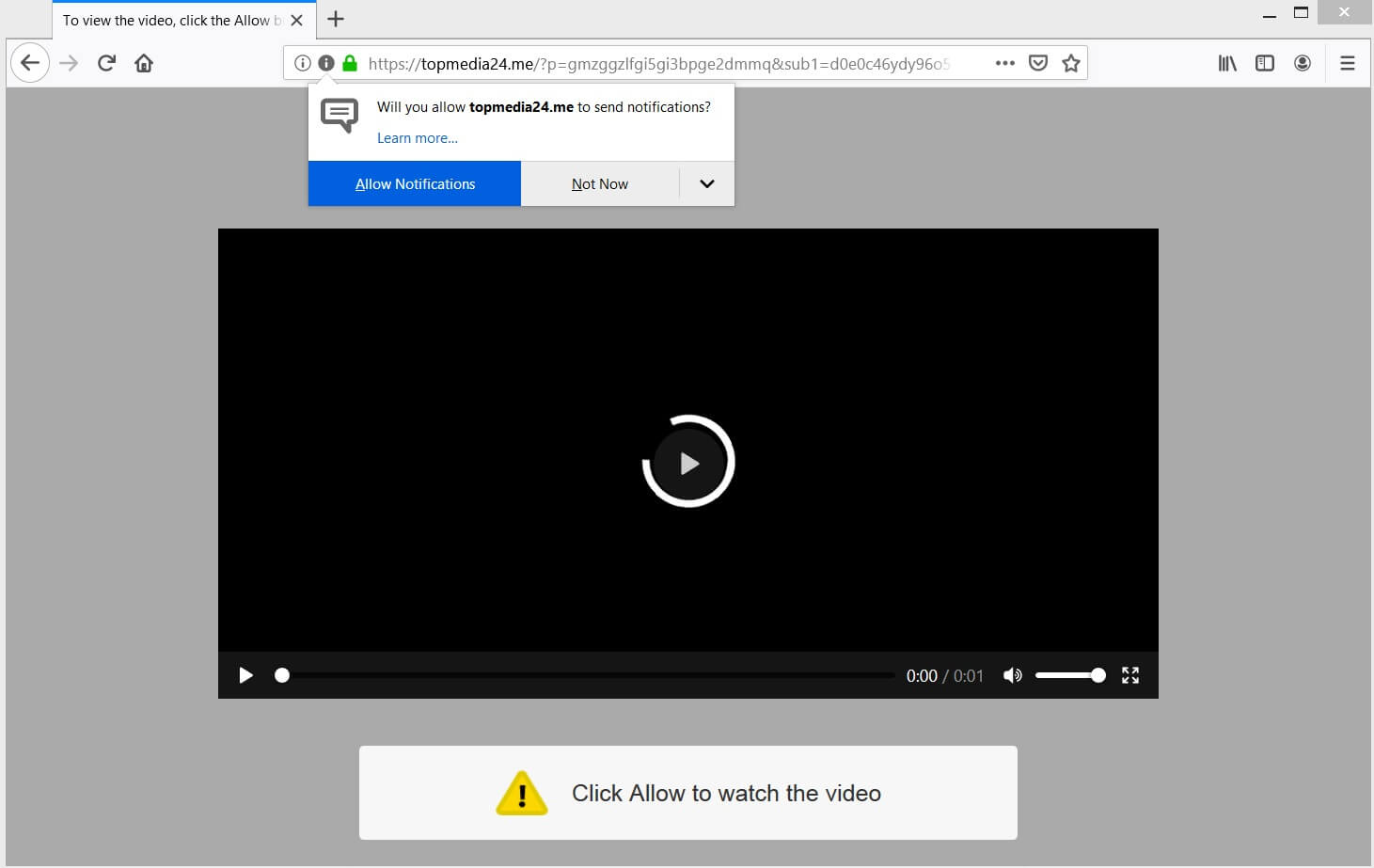
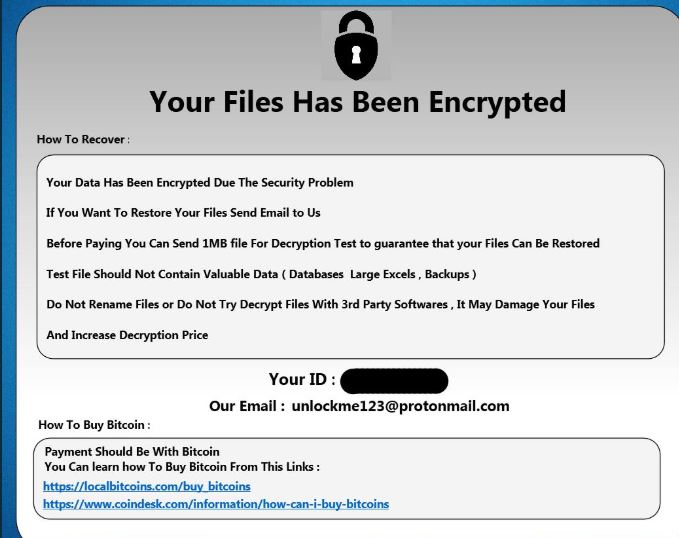
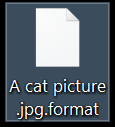
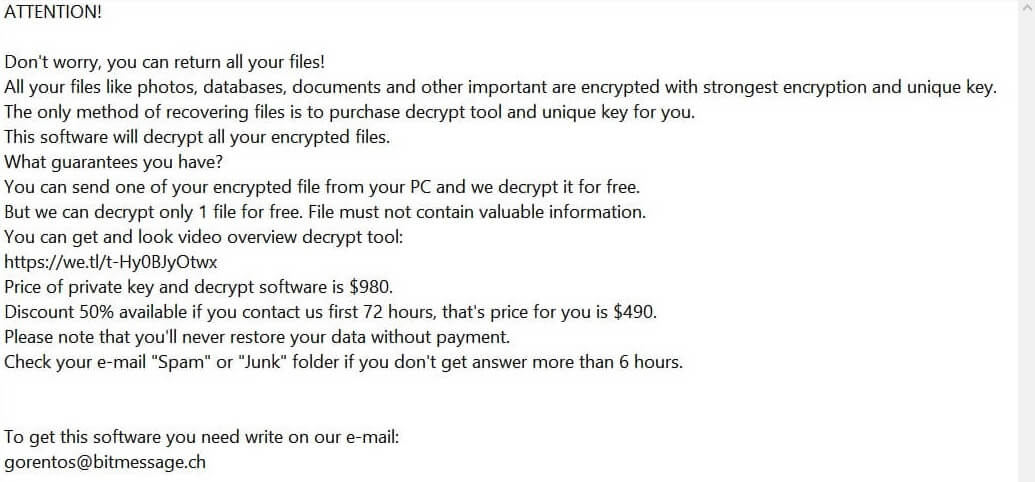
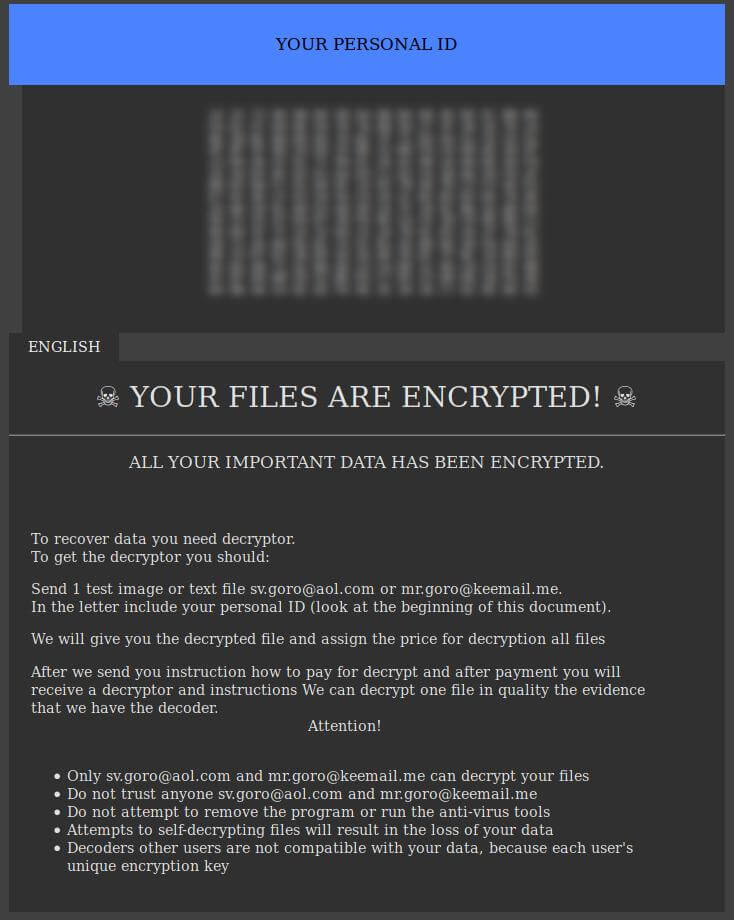
What is .Vesrato file virus? The virus is also known as Vesrato ransomware which encrypts files and demands a ransom for their alleged restoration. .Vesrato file virus or otherwise known as STOP is ransomware. It encrypts files by appending the…