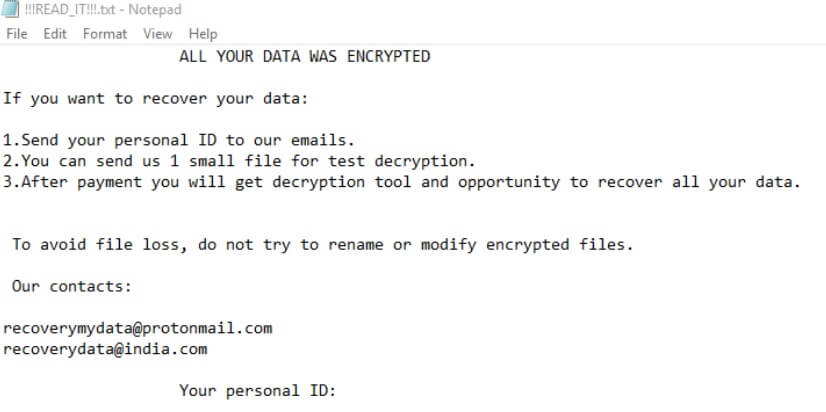
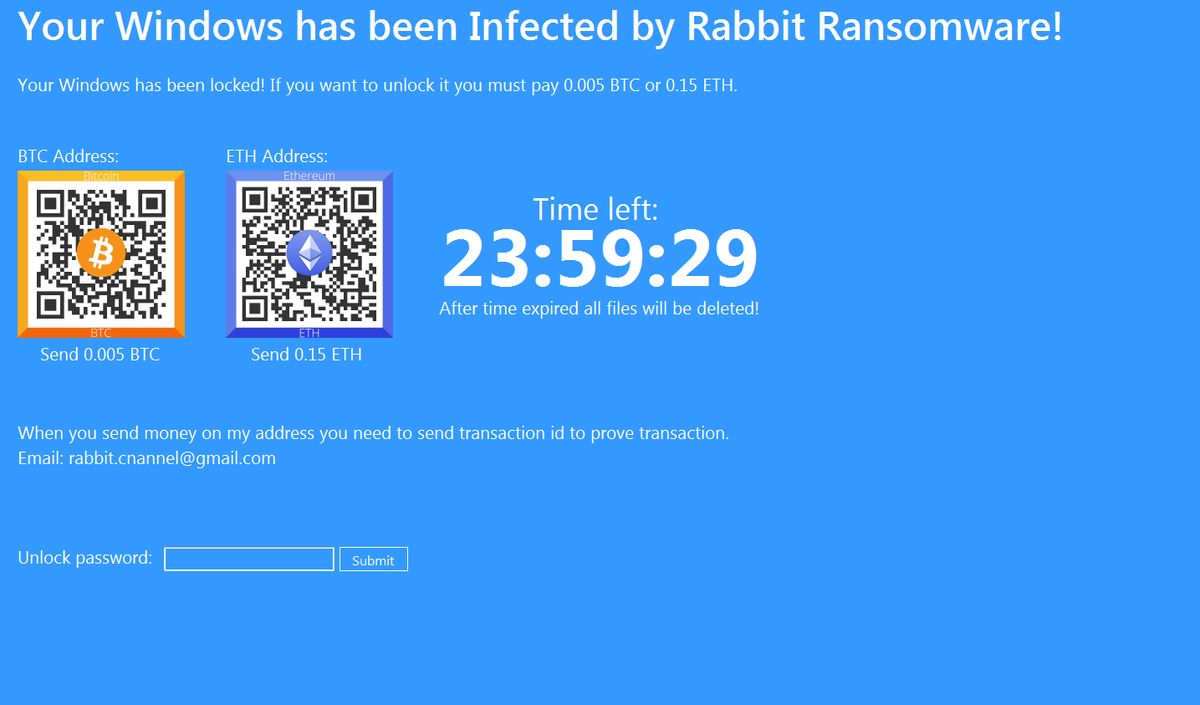
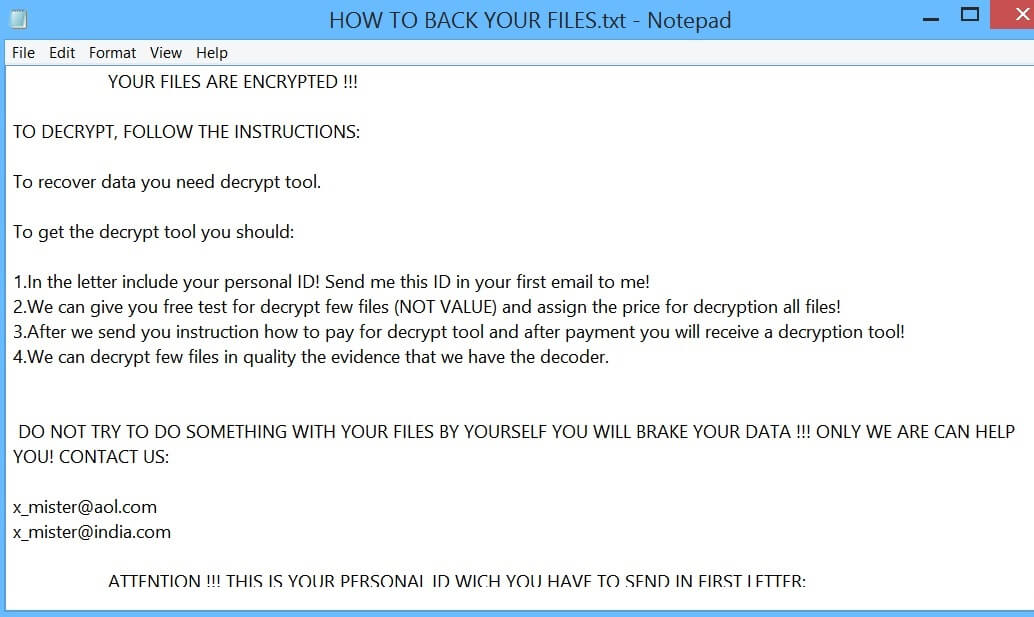
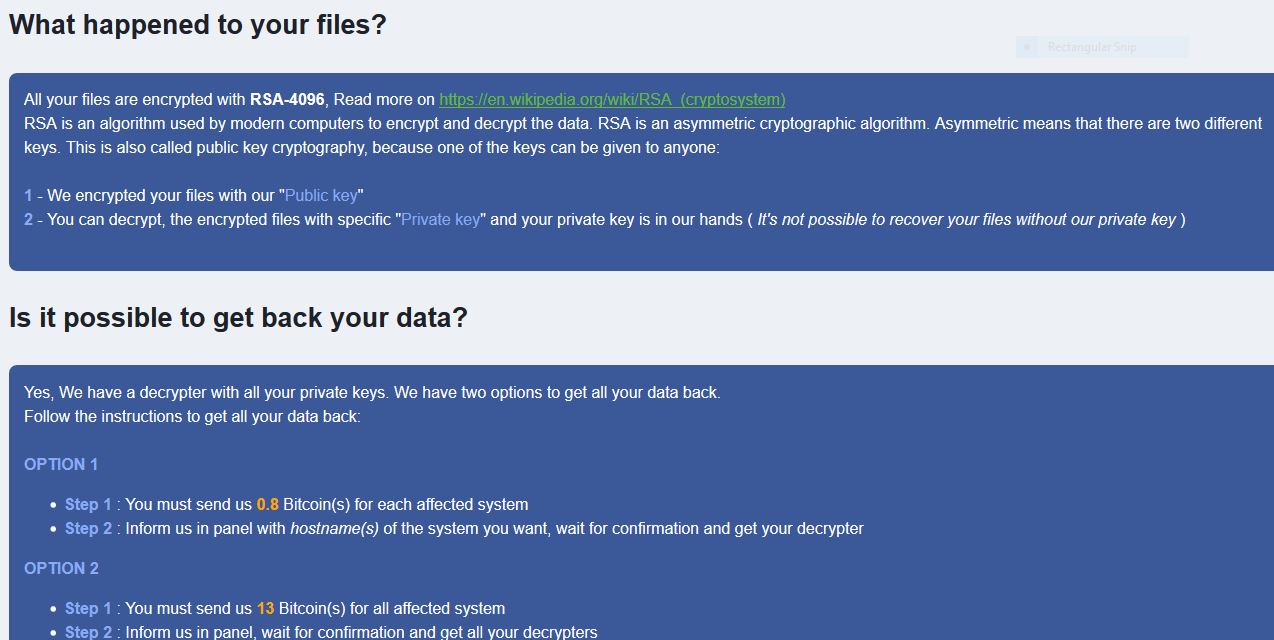
.chech Files Virus (STOP Ransomware) – How to Remove It
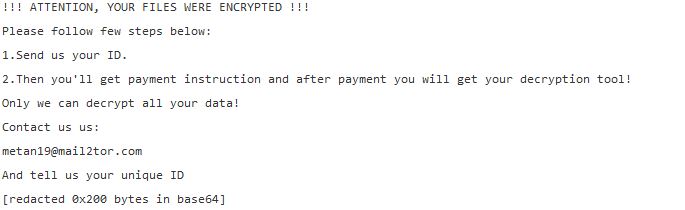
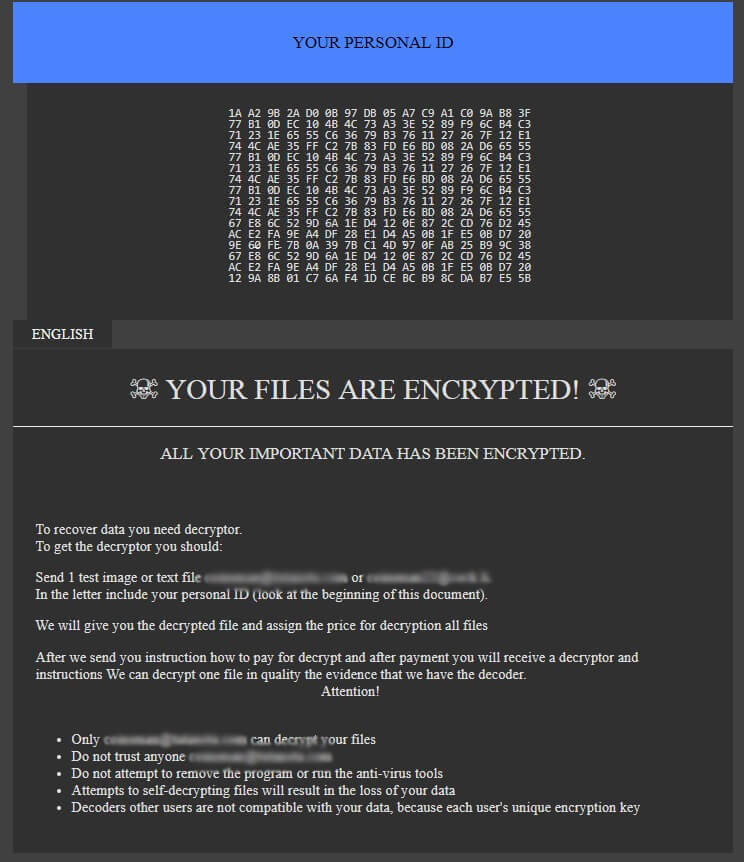
This is an article, created to explain what are .chech files and how to remove STOP ransomware virus and try to restore the .chech files, encrypted by it on your computer. Another variant of STOP ransomware has been recently detected.…





![[mrpeterson@cock.li].GFS Files (GEFEST Ransomware) – How to Remove](https://cdn.sensorstechforum.com/wp-content/uploads/2019/03/gefest-ransomware-how-to-remove-it-and-restore-gfs-encrypted-files-300x242.jpg)