Remove Thecolorian.com Redirect from Mac
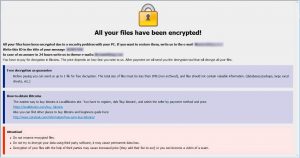
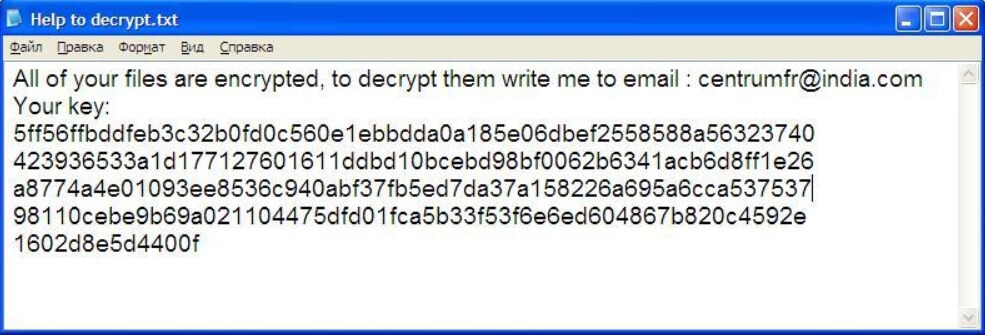
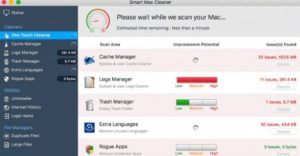
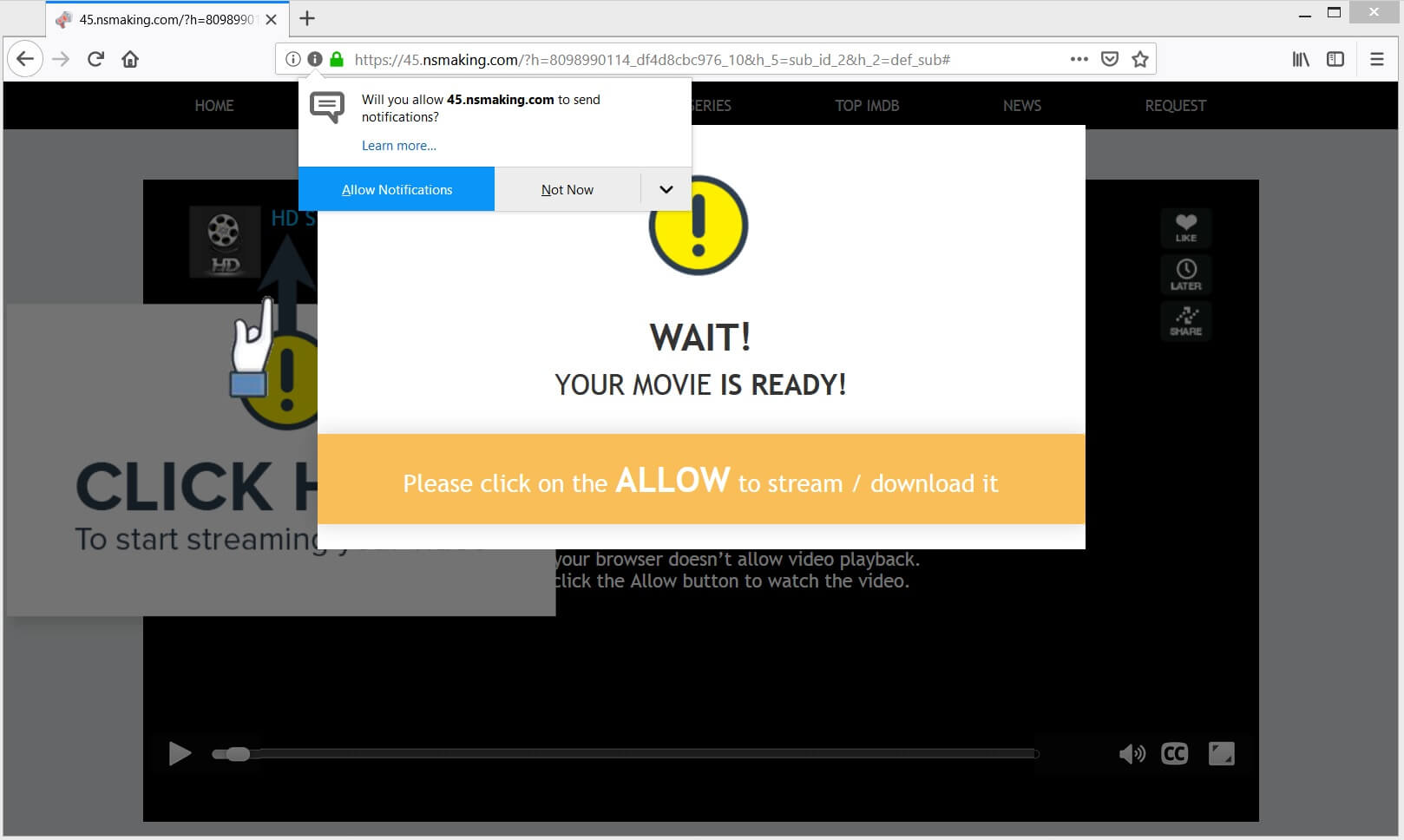
This article will help you to remove Thecolorian.com browser hijacker efficiently. Follow the redirect removal instructions given at the end of the article. Thecolorian.com.com is a browser hijacker redirect. The website will redirect you to its own search engine and…