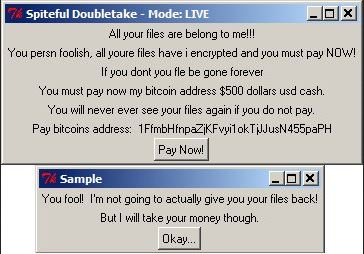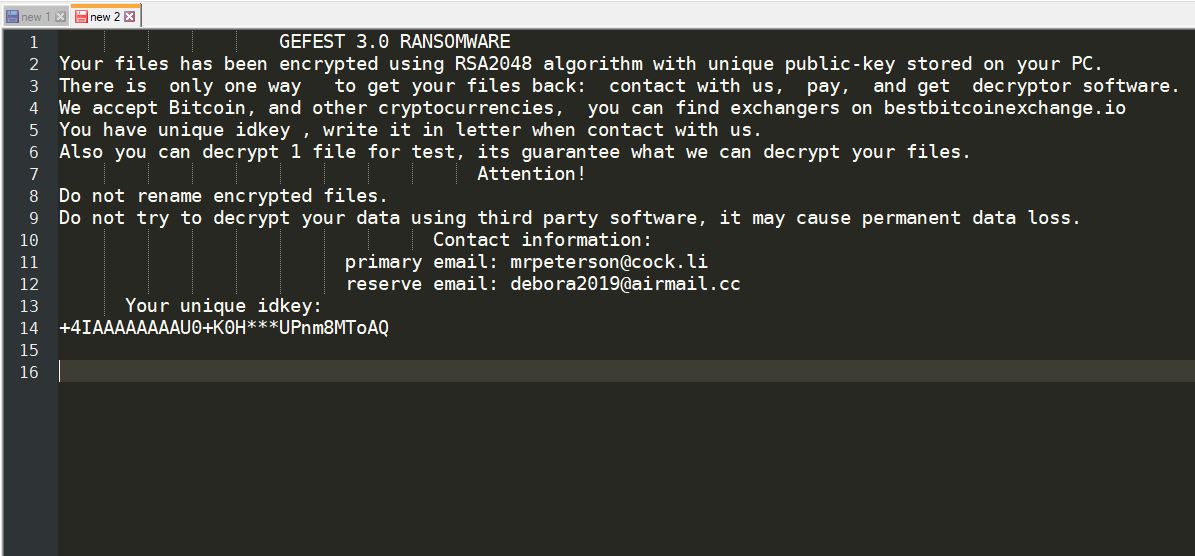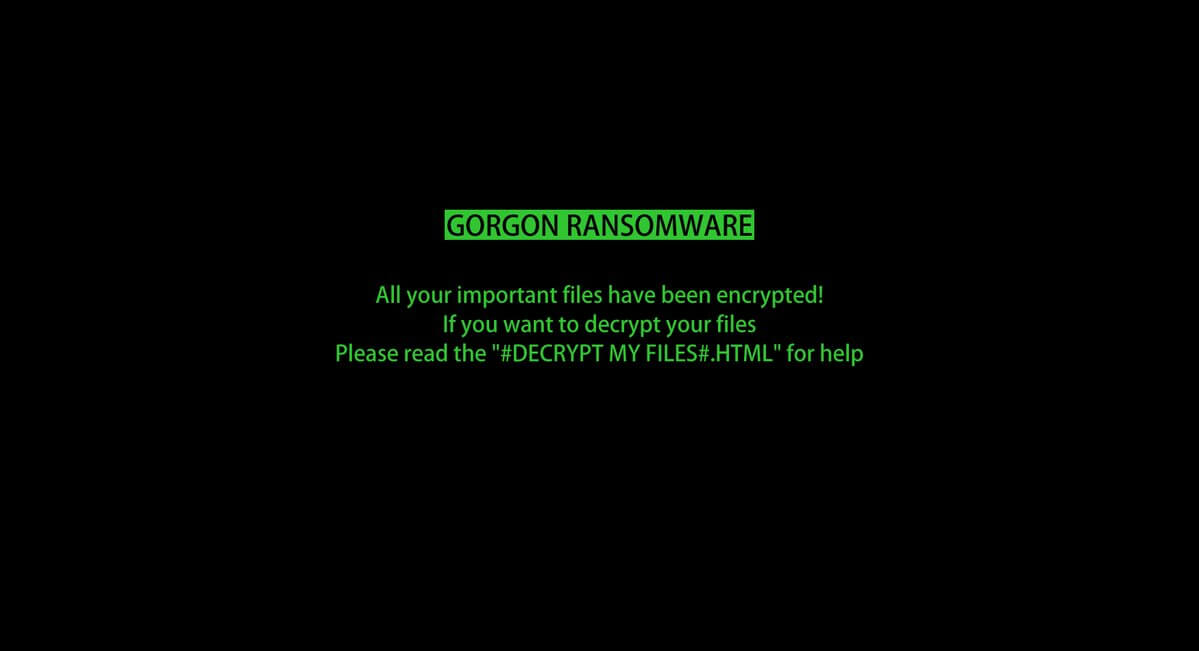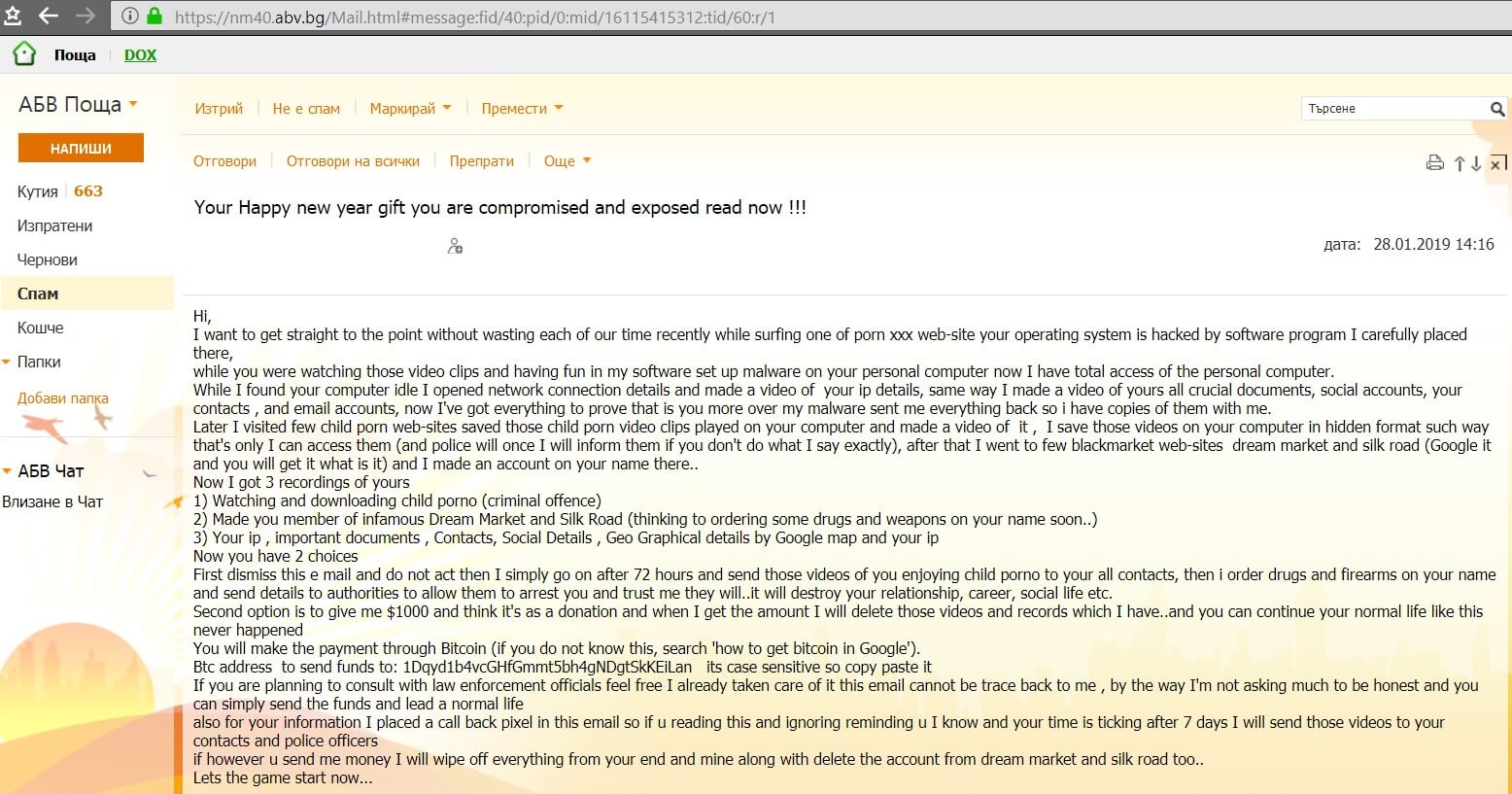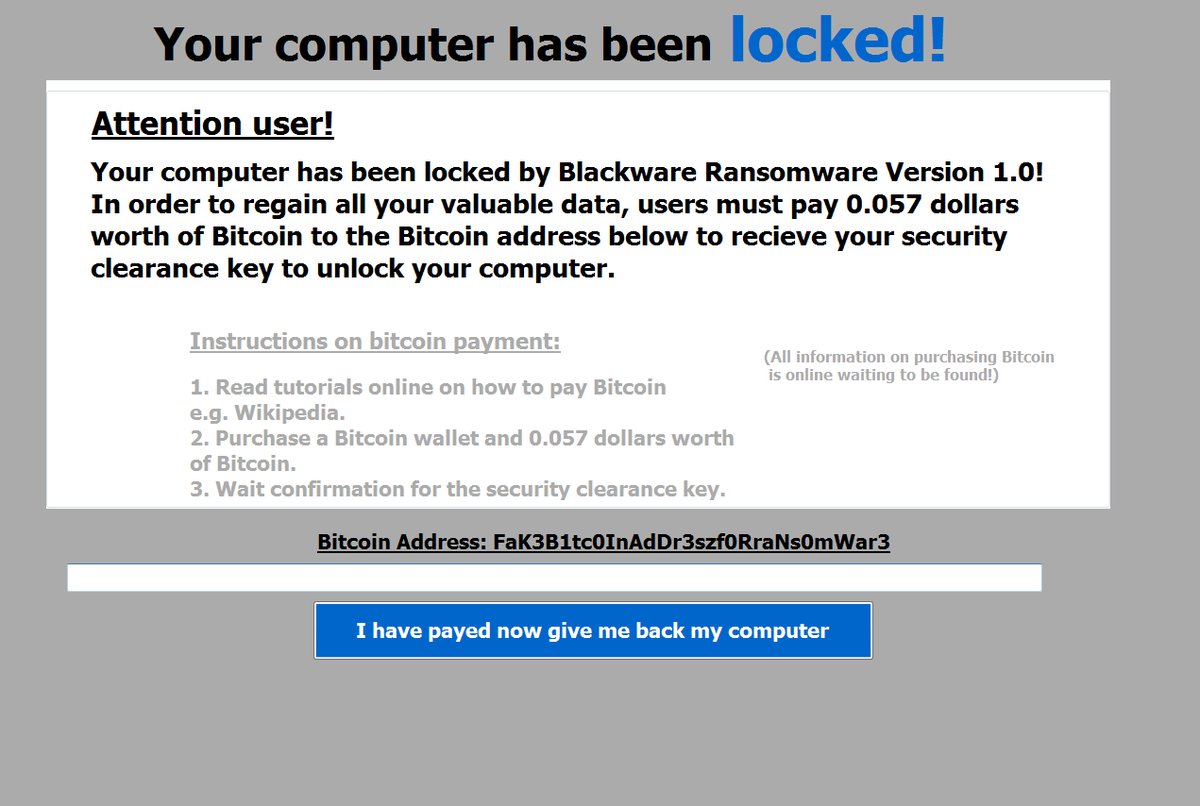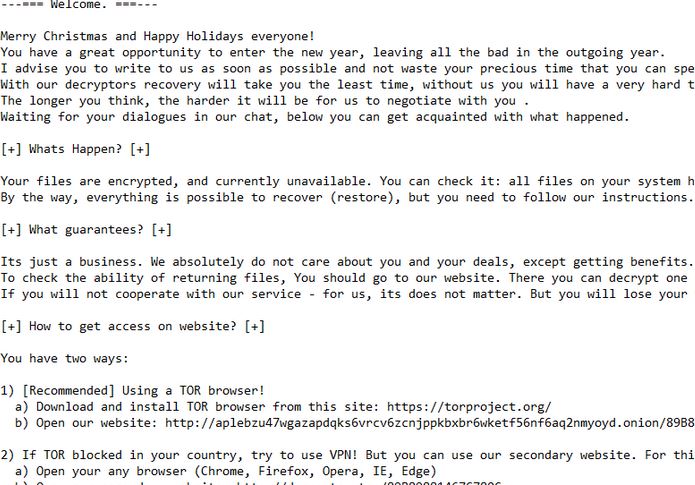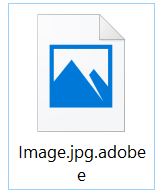
.adobee Files Ransomware (STOP) – Remove It
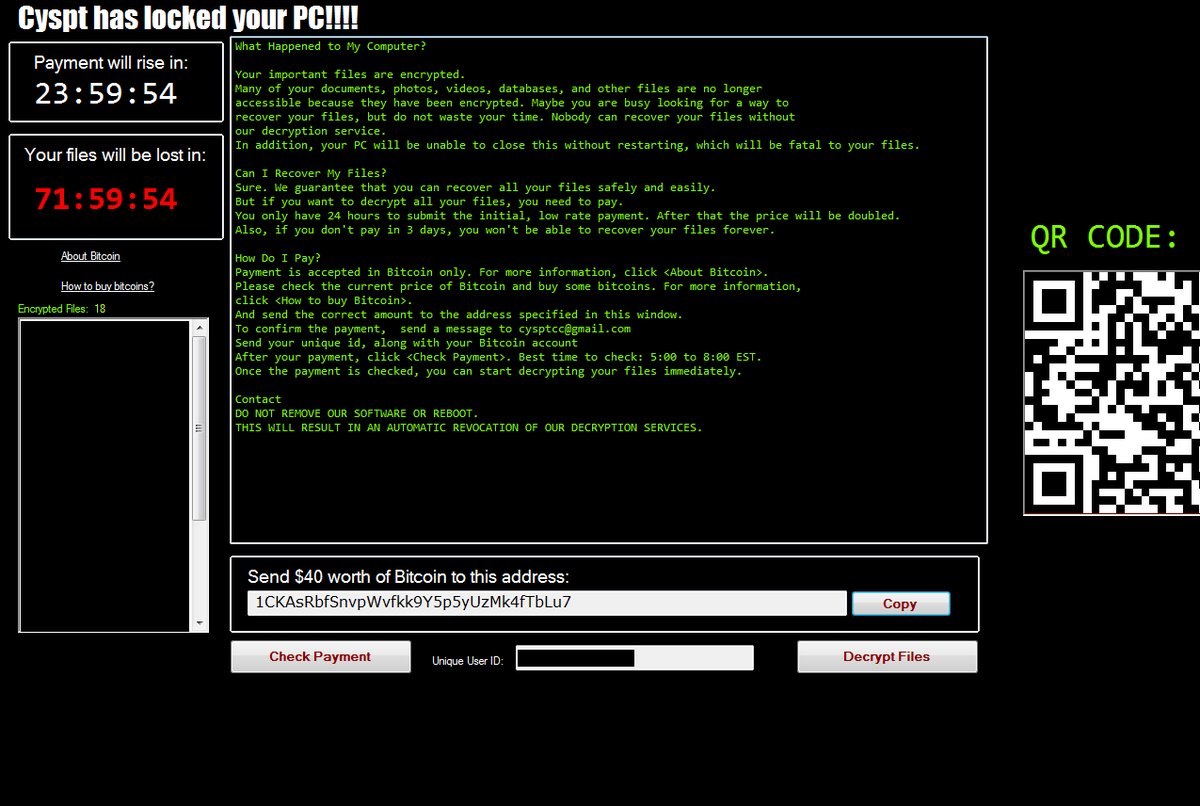
This article has been created in order to better explain to you what exactly is the .adobee files virus and how you can remove this version of the STOP ransomware and show you ways via which you can try and…