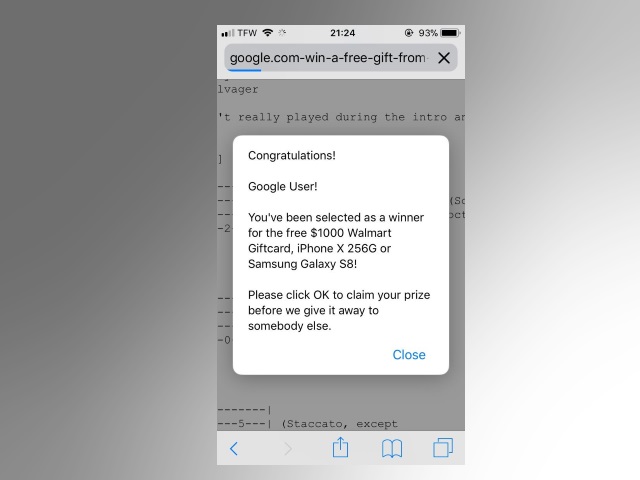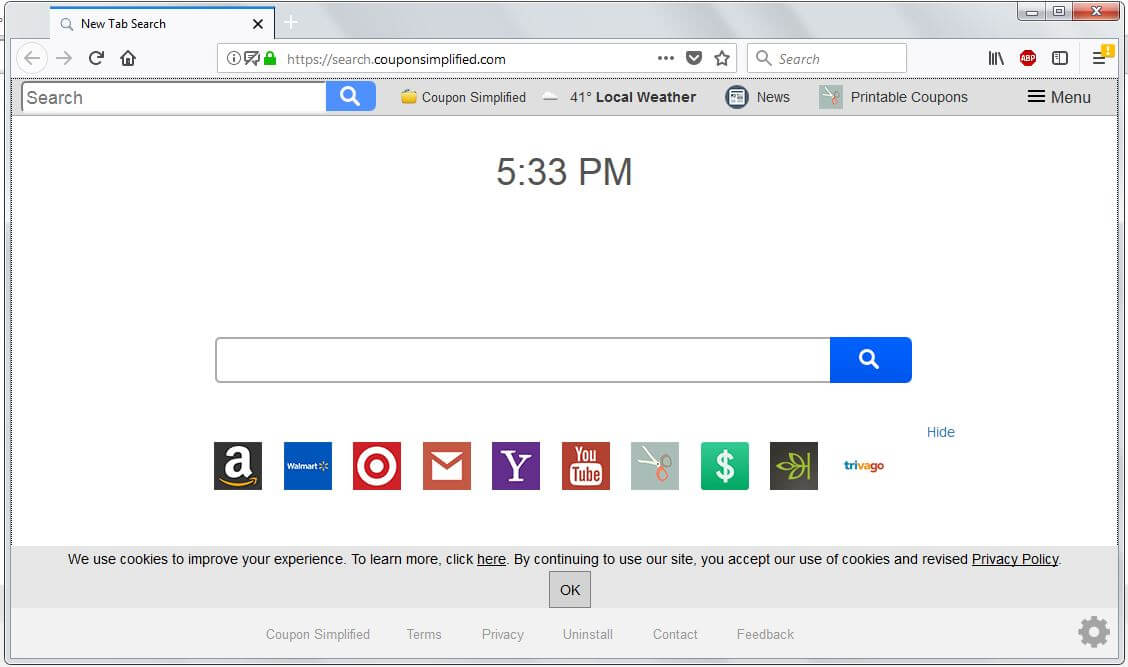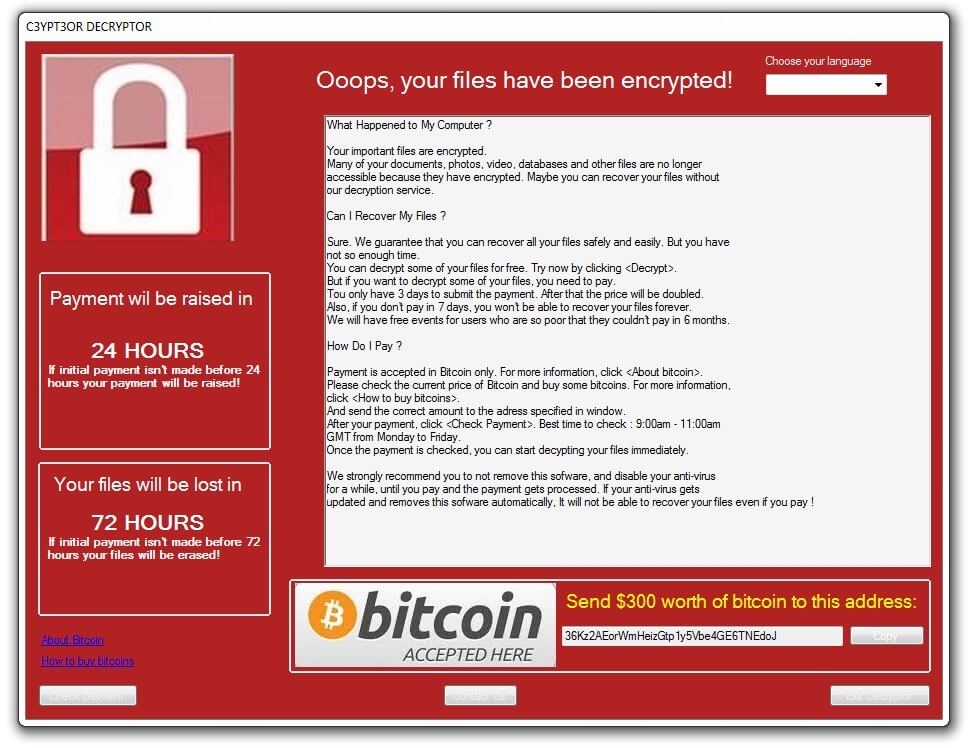
“Your Mac is Heavily Damaged” Scam Page – Remove It
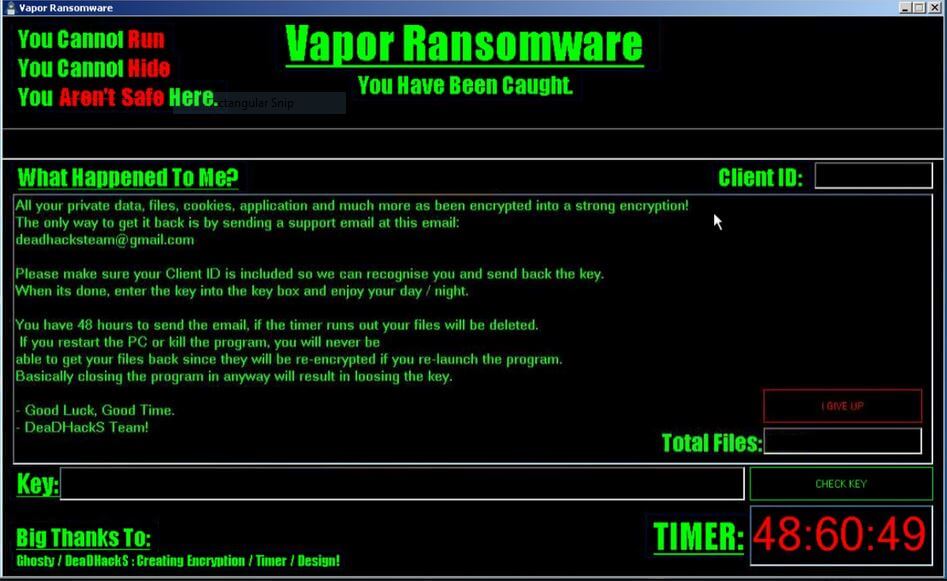
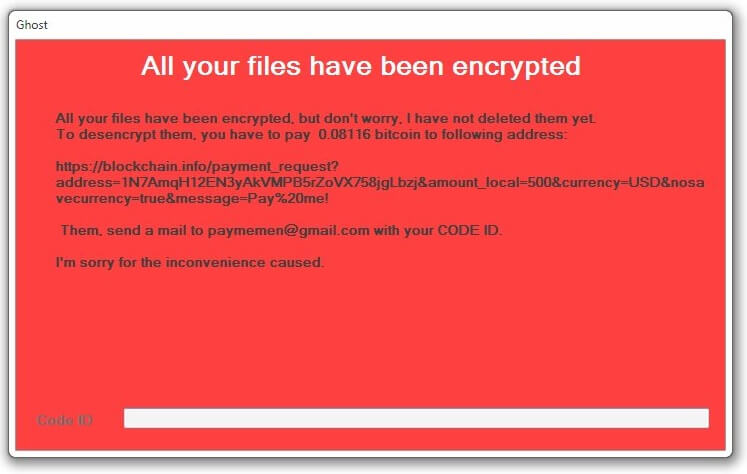
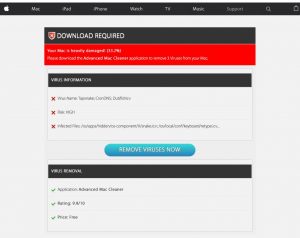
This article has been created with the main goal to explain what is the “Your Mac is Heavily Damaged” (Download Required) scam page, advertising Advanced Mac Cleaner and how you can remove this unwanted program from your Mac. A scam…