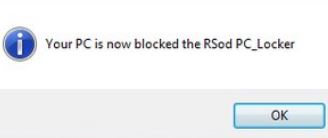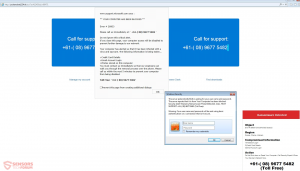
“Microsoft Alert” Pop-up Scam – How to Remove It Fully
This article aims to show you how you can remove the “Microsoft Alert” scam from your computer and how you can restore it back to normal working state. A new scamming message, called “Microsoft Alert” and displayed by a fraudulent…