Old malware doesn’t disappear, as evident by recent revivals of old cases. Just yesterday we wrote about the renewed distribution of the well-known Backdoor.Nital and Gh0st RAT. This article is dedicated to another old malware piece of the worm kind – QakBot – which has been around since 2009. Researchers linked recent Microsoft Active Directory lockouts to QakBot.
Active Directory, Microsoft’s directory server, is designed to allow admins to control networks from a single location. It’s not hard to imagine the stress Active Directory lockouts can bring upon admins.

Threat Summary
| Name | QakBot |
| Type | Computer Worm, Banking Trojan, Information Stealer |
| Short Description | A worm spreading through network shares and removable media drives. The worm can download more malware, steal sensitive information, or open a backdoor on the compromised system. It is also a Banking Trojan. |
| Symptoms | In its latest operation, victims are locked out of Active Directory accounts. |
| Distribution Method | Removable media drives, networks |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss QakBot. |

QakBot Technical Overview
Shortly put, QakBot is a worm spreading through network shares and removable media drives. The worm can download more malware, steal sensitive information, or open a backdoor on the compromised system. Few years ago researchers discovered that QakBot even has rootkit capabilities which hide its presence on the system and make it stealthier.
As for the latest damages associated with QakBot – the Active Directory lockouts – they took place last week and are a first for the malware.
According to researchers at IBM’s X-Force, affected users were unable to access endpoints, company servers and networked assets on affected domains.
QakBot Distribution
Just a couple of days ago a post appeared on Reddit indicating about the renewed state of the malware. According to the Reddit user who started the discussion, a school district was “entirely affected” by its latest variant.
The 2017 variant has been spreading with the help of a dropper that waits about 15 minutes to execute. This is done to decrease the chance of detection from sandboxes or anti-virus engines. The dropper then opens an executable, injects a DLL file, overwriting the original file. Finally, the dropper downloads QakBot.
As already mentioned, the malware has always had worm-like capabilities depicted by its capacity to self-replicate via shared drives and removable media. In its latest campaigns the malware is using networks to propagate, locking users out of their accounts. The propagation is based on cycling through user and domain credentials, researchers say.
To do so, the malware pairs logins with various password guessing techniques such as guessing passwords by using words in a dictionary. “Under certain domain configurations, the malware’s dictionary attack for accessing the target machines can result in multiple failed authentication attempts, which eventually trigger an account lockout,” the researchers explained in a blog post.
QakBot – a Worm and a Banking Trojan
QakBot is also known to target businesses. What makes it a real nightmare is that it is part worm, part banking Trojan:
QakBot is modular, multithread malware whose various components implement online banking credential theft, a backdoor feature, SOCKS proxy, extensive anti-research capabilities and the ability to subvert antivirus (AV) tools. Aside from its evasion techniques, given admin privileges, QakBot’s current variant can disable security software running on the endpoint.
On top of everything else, QakBot continues to be able to evade detection and is very persistent. System reboots don’t work as well as removal attempts with Registry runkey and scheduled tasks. The malware will still load after each system reboot. As for the scheduled task in schtasks.exe – it will make the malware run on timed intervals.
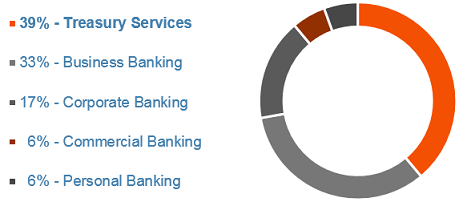
To sum it up, QakBot is a worm, a banking Trojan and an information stealer. Interestingly, it is “also the first Trojan that was designed to exclusively target the business banking sector, a vocation to which it has kept true throughout the past eight years”. These are the sectors affected by the dangerous malware:

QakBot Mitigation and Protection
Since QakBot primarily targets banks and businesses, potential victims should use adaptive malware detection solutions with real-time capabilities. The very first thing, however, is cybersecurity awareness, researchers say. “Users can protect themselves and their organizations by practicing browsing hygiene, disabling online ads, filtering macro execution in files that come via email and observing other security best practices”.
To mitigate QakBot activity on the network, users should reassure domain accounts are configured with the least privilege needed to perform job tasks
Organizations are advised to create a random domain admin account for safety purposes and then make sure it reports directly to the security information and event management system (SIEM) when there’s an attempt to use it.
And finally, organizations should prevent workstation-to-workstation communications wherever possible “possible to force malware out of the trenches and into areas where central detection systems will pick it up quickly”, researchers conclude.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter