This article will aid you to remove the Ursnif Trojan (Purolator phishing scam) completely. Follow the Trojan horse removal instructions given at the end of the article.
Ursnif Trojan is a banking Trojan horse that is recently being spread via a Purolator phishing scam with a message stating that you have a package. one of the most spread messages, says: Purolator have a package for you. Pop-ups that show constantly can also lock your browser on that page. E-mail campaigns are also spreading the phishing scam. You might experience redirects. The browser can be shut down without any negative impact, but in other cases your system and browser could get affected with the Ursnif Trojan. Most variants of this scam feature a background image that aims to utilize the brand and logo of Purolator shipping company.

Threat Summary
| Name | Ursnif Trojan horse |
| Type | Trojan horse, Phishing Scam |
| Short Description | Phishing scam which is trying to take you (with click-bait and social engineering tactics) to a Purolator Phishing page that spreads the Ursnif Trojan or other viruses. |
| Symptoms | Pop-up boxes, messages, and redirects appear in your browser or such are send in your email. It is not excluded for there to be a lockscreen function among these that keeps prompting you to click a link. |
| Distribution Method | Suspicious Sites, Redirects, Email Phishing Links |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join Our Forum to Discuss Ursnif Trojan horse. |

Ursnif Trojan (Purolator Phishing) Scam — Update October 2019
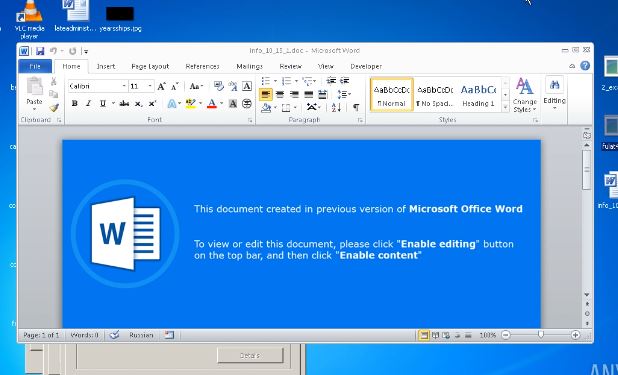
A recently discovered campaign distributing the Ursnif Trojan has been detected by computer specialists. This discovery shows that this malware is still being used actively by computer hacking groups, showing the possibility that it is available on the underground hacker portals and further customized by criminals. It appears that the active ongoing campaign targets primarily Italy and Canada using phishing strategies focusing on sending out email messages that will include malware files. The data in question is macro-infected documents which are either attached to the messages or embedded in the emails. The emails themselves are designed to appear as legitimate notifications or service announcements and the users are manipulated into clicking on them. The documents can be of all popular file formats, including presentations, databases, text files and spreadsheets. As soon as they are opened a prompt will appear asking the users to enable the built-in code in order to correctly vie the contents.
The execution o the macros can deliver the malware file which wll self-execute itself. An alternative is to send out double extension files which when run will start a .zip archive that includes a built-in executable. When started the infection will start a dangerous sequence which will run the following modules:
- Web Browser Interaction — The main engine associated with the Trojan can interact with the installed web browsers by accessing the contained within data and it can also modify the settings by always redirecting to a certain hacker-controlled web page.
- System Reconfiguration — The Ursnif Trojan is capable of editing out the configuration files of the operating system or any of the installed user software.
- Additional Malware Delivery — The Ursnif Trojan can be a very effective tool for deploying other viruses onto the already compromised computers.

Ursnif Trojan (Purolator Phishing) Scam – Distribution Techniques
Browsing the Web can be dangerous, especially when you reach new and unknown websites by causally browsing and they turn out to be malicious. Clicking on advertisements or targeted content could have hidden links that redirect you to dubious online places. Other websites could be filled with advertisements and redirect links and you could land on a page such as the Ursnif Trojan (Purolator Phishing) one.
Email campaigns that spread malicious links, ads, attachments and link to phishing landing pages are connected with the spread of the Purolator Phishing Scam which loads the Ursnif Trojan horse to your system. The attachments can be Microsoft Word documents with embedded VBS Macros that are malicious. The said macros run a PowerShell script, which downloads Ursnif to a compromised PC. In the above two pictures (above this paragraph and in the very beginning of the article) you can see exactly how one such email message is presented to potential victims in terms of content, which is:
Your parcel is registered with the branch of Canada Post.
You may get track number immediately with our online Track instrument PRESS HERE or digit it in your web browser https://canadacpost(.)tk/treck21413252.zip
Our tracking system is refreshed every 24 hours to provide you with the most current information available about the geographic position and status of your item.
That is one of the messages that spread via email and is seen above the last paragraph in this section of the article. If you have downloaded a .zip file that you are suspicious of, you can always check its contents for malware with ZipeZip Online Scanner. However, do not be tempted to open any links from emails especially if they look like the one discussed above or if they are sent from an unknown (unverified) source.

Ursnif Trojan (Purolator Phishing) Scam – In Greater Depth
Ursnif Trojan is being pushed by a number of Purolator phishing scam messages. The scam has a few, different landing pages, which use the brand, logo, design and fonts of Purolator, including their official site’s text and element placement. All of this is done to try to convince you into clicking somewhere and entering your credential details on a phishing page. Thus your account and profile data can get stolen and hijacked or just spoofed so they can be sold somewhere.
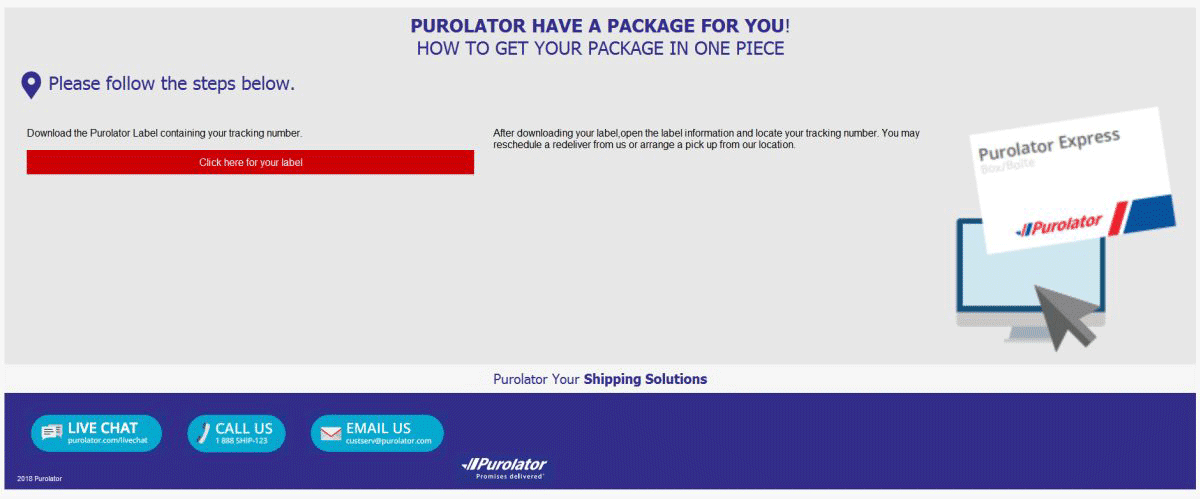
In the screenshot image below, you can see one of the scam pages that have a convincing message using the Purolator brand that require you to click somewhere on the page:
If you indeed click on the spot which cybercriminals wish you to click, you could get redirected to a phishing page and/or get your computer system infected with the Ursnif Trojan (Purolator Phishing) threat.
The message in the above snapshot of the current Ursnif Trojan (Purolator Phishing) scam states the following:
PUROLATOR HAVE A PACKAGE FOR YOU!
[Click here for your label]
HOW TO GET YOUR PACKAGE IN ONE PIECE
Please follow the steps below.
Download the Purolator Label containing your tracking number.After downloading your label,open the label information and locate your tracking number. You may reschedule a redeliver from us or arrange a pick up from our location.
Purolator Your Shipping Solutions
All of these Ursnif Trojan (Purolator Phishing) scams could also be displayed with pop-ups as alerts around websites, applications, emails and other means. Ursnif v3 Banking Trojan has been spotted to have sophisticated targeting techniques in the past so it is no wonder that it has decided to use a phishing scam for one of Canada’s most known shipping services.
In case there is a telephone number present somewhere on the site, know that the criminals standing on the other end of the telephone line will try to trick you in giving them information related to Purolator or that is even more personal. Do not believe if they present themselves as employees in Purolator or another notable company. However, know that the Ursnif Trojan might use a silence dropper technique that could trigger by just opening the Purolator Phishing scam page.
Browsers you have installed or your computer screen can become locked and may seem like your whole screen is blocked and totally inaccessible. In such a situation, you could try clicking the “Windows” button and combinations such as “Ctrl+Alt+Del” or even the “Close” button to check if you still can interact with your computer device.
You could also get prompted to download and install a tool which might be the Ursnif Trojan or some other malware. Keep in mind that it is all part of the scam and you shouldn’t follow any instructions given on your computer screen.
If you see any similar messages, know that they aren’t coming from Purolator. Also, no matter how many pop-ups, alerts and message boxes are shown, try to remember that this is a sophisticated scam that wants to harm your computer or steal credentials, banking data or other information from you.

Ursnif Trojan (Purolator Phishing) Scam – How to Avoid?
In this section, you will find out a simple set of rules and guidelines to follow in order to prevent yourself from falling in a trap related to Ursnif Trojan (Purolator phishing) scam and other related threats. So, if you are reading this article, you should now know that there is a multitude of scams involving a Purolator shipment or parcel notifications. Below you will see what you should do.
Purolator’s official warning alert should be enough of a hint to you that there are such scams pushed time and time again. For further reference, the web address for the official Purolator website is https://www.purolator.com/en/home.page and its main page is displayed below:
As you now know about the existence of the emails involving the Ursnif Trojan (Purolator phishing) scam and the official Purolator site page, refer to the following guidelines on how to avoid most scams linked to using the shipping brand for their schemes:
- Never pay before your goods get delivered
- Do not provide any details about you, your addresses or similar information via email or unknown Websites
- Do not open email attachments, as Purolator does not send such, neither it requests users to open such
- Always use Purolator’s official website to refer to pages in connection with the service
- Avoid messages with grammatical or typographical errors
- Avoid emails that are not addressed to you by name
- Avoid messages sent by a service you don’t expect to hear from
- Avoid messages that do not include a tracking number or specific details about your order or address
- Avoid clicking on links to provide your email address for verification
- Avoid payments to someone whose identity you can’t confirm
The guideline rules listed above were constructed by the SensorsTechForum team, via a research done on the matter. These rules are based on common sense and depending on the various scams related to Purolator.

Remove Ursnif Trojan (Purolator Phishing) Scam
To remove the Ursnif Trojan (Purolator Phishing) scam and its related Trojan horse files manually from your PC, follow the step-by-step removal instructions provided below. If the manual removal guide does not get rid of the scam and its redirects completely, you should search for and remove any leftover items with an advanced anti-malware tool. Software like that will keep your system secure in the future.
Preparation before removing Ursnif Trojan horse.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
- Scan for Malware
- Fix Registries
- Remove Virus Files
Step 1: Scan for Ursnif Trojan horse with SpyHunter Anti-Malware Tool



Step 2: Clean any registries, created by Ursnif Trojan horse on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Ursnif Trojan horse there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.Step 3: Find virus files created by Ursnif Trojan horse on your PC.
1.For Windows 8, 8.1 and 10.
For Newer Windows Operating Systems
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.

2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.

3: Navigate to the search box in the top-right of your PC's screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be "fileextension:exe". After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.For Windows XP, Vista, and 7.
For Older Windows Operating Systems
In older Windows OS's the conventional approach should be the effective one:
1: Click on the Start Menu icon (usually on your bottom-left) and then choose the Search preference.

2: After the search window appears, choose More Advanced Options from the search assistant box. Another way is by clicking on All Files and Folders.

3: After that type the name of the file you are looking for and click on the Search button. This might take some time after which results will appear. If you have found the malicious file, you may copy or open its location by right-clicking on it.
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software.
Ursnif Trojan horse FAQ
What Does Ursnif Trojan horse Trojan Do?
The Ursnif Trojan horse Trojan is a malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system.
It can be used to steal sensitive data, gain control over a system, or launch other malicious activities.
Can Trojans Steal Passwords?
Yes, Trojans, like Ursnif Trojan horse, can steal passwords. These malicious programs are designed to gain access to a user's computer, spy on victims and steal sensitive information such as banking details and passwords.
Can Ursnif Trojan horse Trojan Hide Itself?
Yes, it can. A Trojan can use various techniques to mask itself, including rootkits, encryption, and obfuscation, to hide from security scanners and evade detection.
Can a Trojan be Removed by Factory Reset?
Yes, a Trojan can be removed by factory resetting your device. This is because it will restore the device to its original state, eliminating any malicious software that may have been installed. Bear in mind, that there are more sophisticated Trojans, that leave backdoors and reinfect even after factory reset.
Can Ursnif Trojan horse Trojan Infect WiFi?
Yes, it is possible for a Trojan to infect WiFi networks. When a user connects to the infected network, the Trojan can spread to other connected devices and can access sensitive information on the network.
Can Trojans Be Deleted?
Yes, Trojans can be deleted. This is typically done by running a powerful anti-virus or anti-malware program that is designed to detect and remove malicious files. In some cases, manual deletion of the Trojan may also be necessary.
Can Trojans Steal Files?
Yes, Trojans can steal files if they are installed on a computer. This is done by allowing the malware author or user to gain access to the computer and then steal the files stored on it.
Which Anti-Malware Can Remove Trojans?
Anti-malware programs such as SpyHunter are capable of scanning for and removing Trojans from your computer. It is important to keep your anti-malware up to date and regularly scan your system for any malicious software.
Can Trojans Infect USB?
Yes, Trojans can infect USB devices. USB Trojans typically spread through malicious files downloaded from the internet or shared via email, allowing the hacker to gain access to a user's confidential data.
About the Ursnif Trojan horse Research
The content we publish on SensorsTechForum.com, this Ursnif Trojan horse how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific trojan problem.
How did we conduct the research on Ursnif Trojan horse?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of trojans (backdoor, downloader, infostealer, ransom, etc.)
Furthermore, the research behind the Ursnif Trojan horse threat is backed with VirusTotal.
To better understand the threat posed by trojans, please refer to the following articles which provide knowledgeable details.