Android is once again found to be vulnerable to a serious piece of malware, and this time the scale of the infection is larger than one could imagine. Security researchers came across a massive, unceasing campaign that has infected about 5 million mobile devices on a global scale. The malware has been dubbed RottenSys.
Attackers have concealed it as a System Wi-Fi Service app that was pre-installed on millions of new devices by widely-spread brands like Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung, and GIONEE. The devices have been shipped through Tian Pai, a Hangzhou-based mobile phone distributor, but it is not known whether the company has anything to do with the malicious campaign.
More about the RottenSys Android Malware Campaign
Researchers from the Check Point Mobile Security Team discovered a new widespread malware family targeting nearly 5 million users for fraudulent ad revenues. Apparently, this is an advanced malware designed to take over Android permissions to initiate its pernicious operations.
According to the findings, the malware began distributing in September 2016. By March this year, it has infected 4,964,460 devices, making it one of the largest Android malware campaigns.
How Is RottenSys Bypassing Detection?
The malicious actors behind the operation obviously know what they are doing as the fake System Wi-Fi service app doesn’t have malicious components at first. It also doesn’t initiate any suspicious activities and stays quiet for a while. Instead of an aggressive behavior, the malware is communicating with its command and control server to obtain the list of the components actually containing malicious code.
Then, the RottenSys malware continues with downloading the malicious components silently, via the DOWNLOAD_WITHOUT_NOTIFICATION permission which does not require any user interaction. Typically, the malware downloads three additional components.
Once all the needed components are downloaded, RottenSys deploys an open-sourced Android application virtualization framework called ‘Small’ (github.com/wequick/small). The framework enables all the components to run simultaneously to achieve the combined malicious functionality of an extensive rough ad network that displays advertisements on the device’s home screen in the form of either pop-up windows or full screen ads, the researchers explained.
To avoid having its operation shut down by the Android system, RottenSys uses another open source framework called MarsDaemon (github.com/Marswin/MarsDaemon). While MarsDaemon keeps processes alive, it also hinders the device’s performance and drains the battery.
It is also worth noting that RottenSys is adapted to employ the Guang Dian Tong (Tencent ads platform) and Baidu ad exchange for its ad fraud operation. Furthermore, the researchers say that the malware has quite a few variants of the payloads (the dropper and the additional components), and each variant is tailored for different campaign, device type, advertisement platform, and spread channel.
The researchers identified two parallel C&C servers which were used by RottenSys for its operation. They “also managed to analyze the attacks and define separate channels in which the attackers operate and even ascertain the volume of infected devices and fraudulent ads displayed to users”.
The bottom line is that the RottenSys operation is an extremely aggressive ad network:
In the past 10 days alone, it popped aggressive ads 13,250,756 times, and 548,822 of which were translated into ad clicks. As an example for the possible revenue stream attackers enjoy from this malware, we [the researchers] calculated the revenue from these impressions and clicks according to the conservative estimation of 20 cents for each click and 40 cents for each thousand impressions. According to these calculations, the attackers earned over $115k from their malicious operation in the last ten days alone!
What Can Be Done to Mitigate RottenSys?
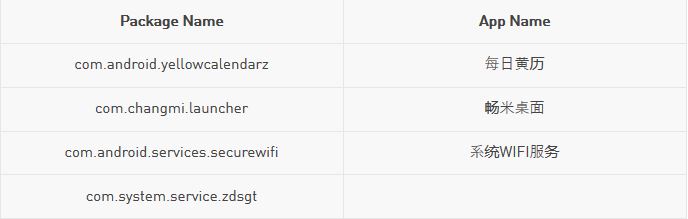
Users should uninstall the RottenSys dropper. However, the exact package name should be known so that it is removed completely. If you are experiencing unknown ads on the home screen of your brand new phone, go to Android system settings, then to app manager, and locate the following possible malware package names. Then uninstall them: