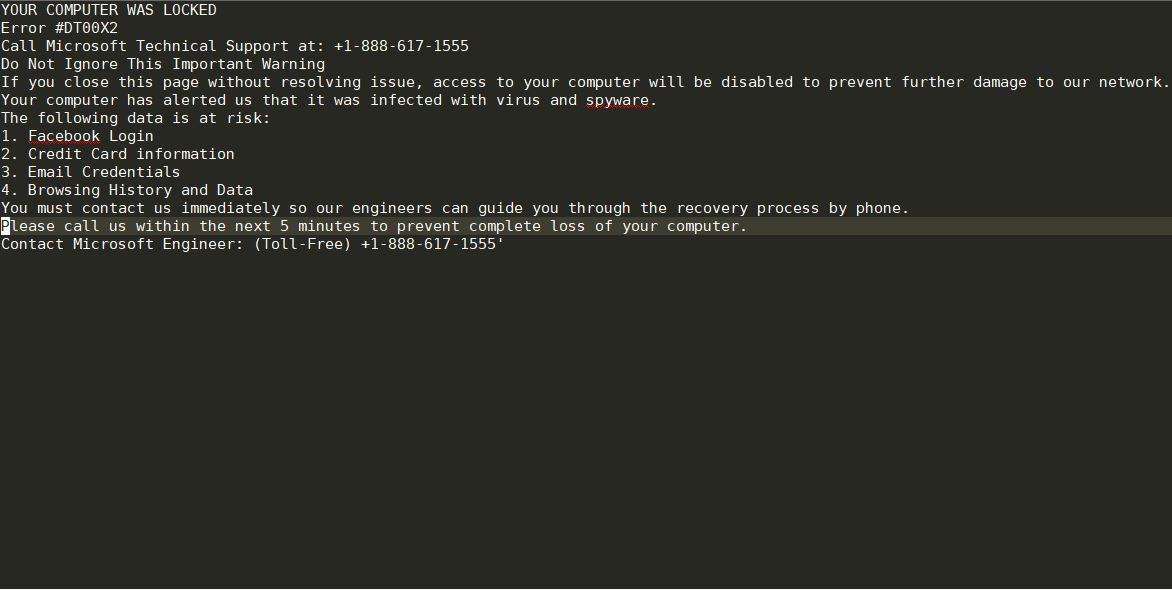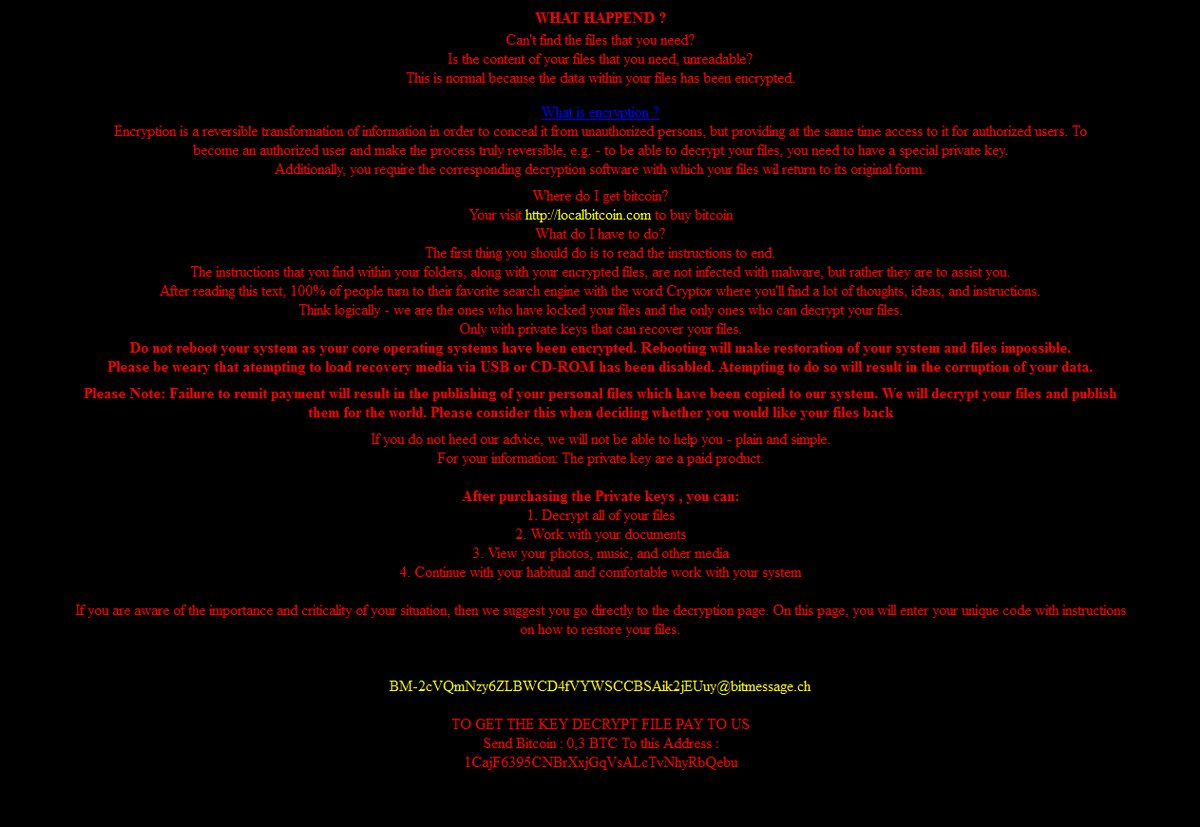
Remove OPdailyallowance Virus (Hidden Tear) and Restore .CRYPTR Files
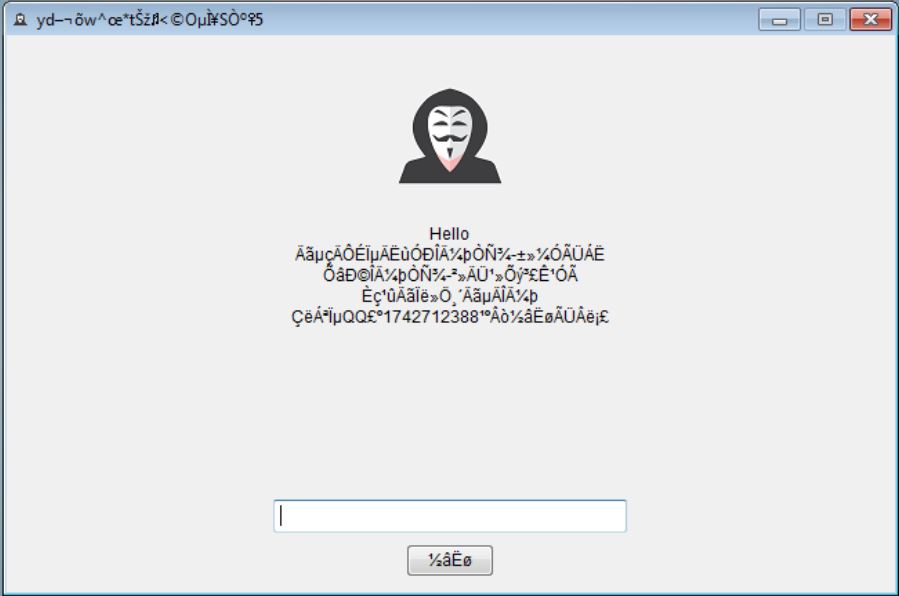
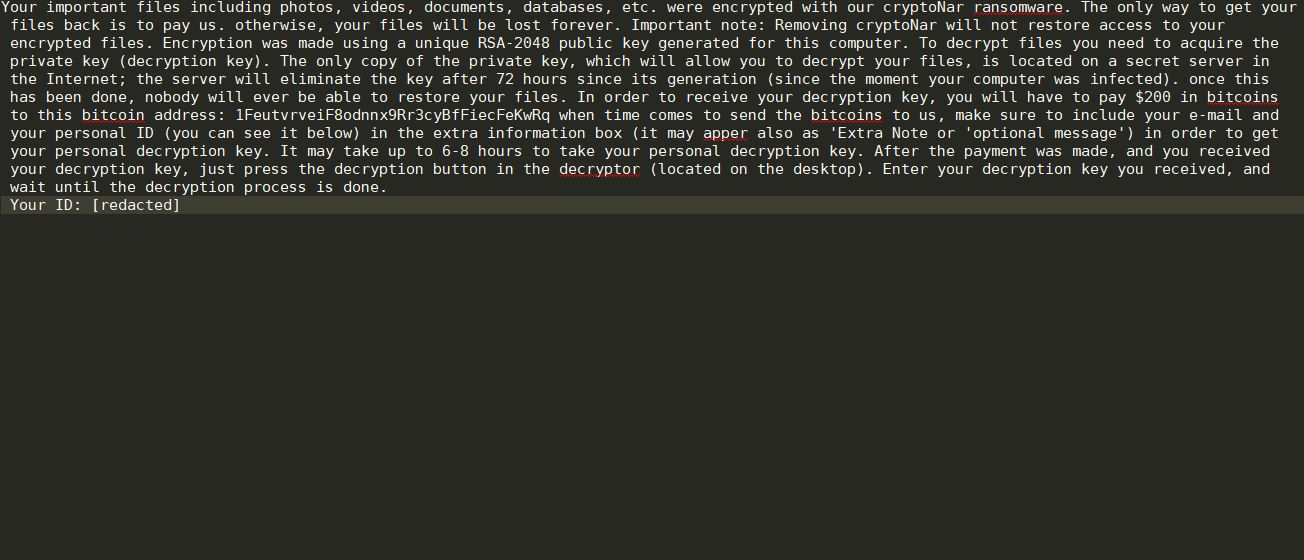
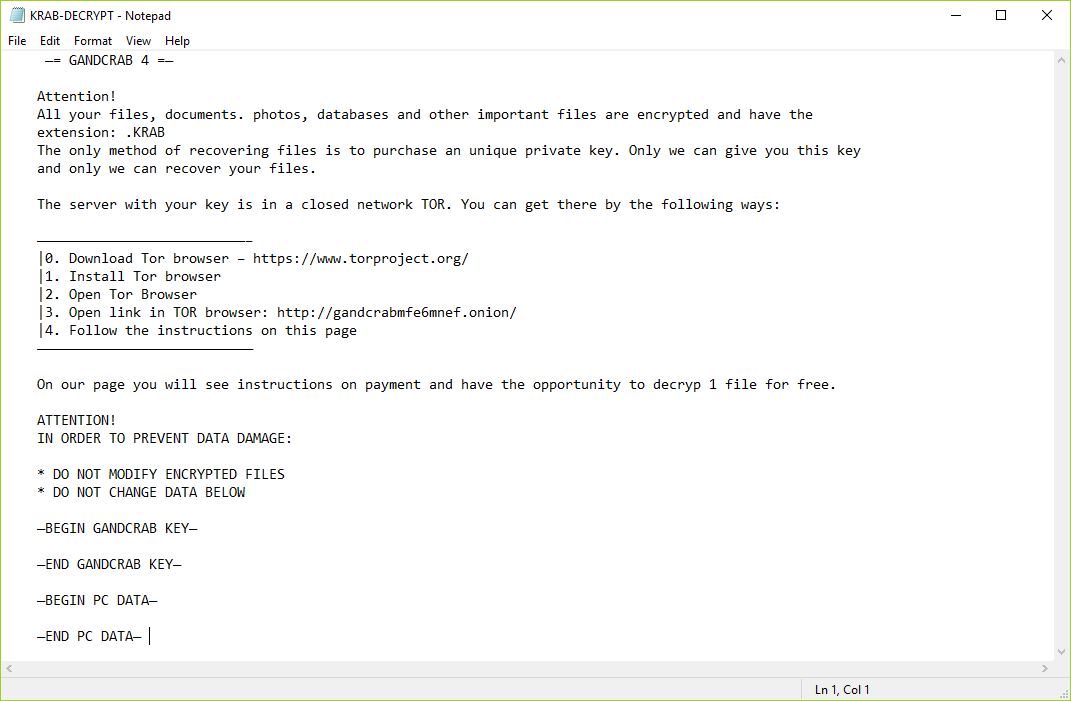
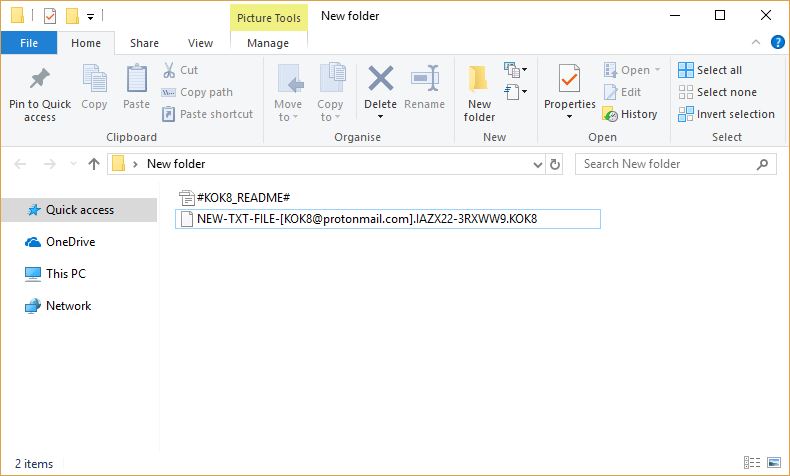
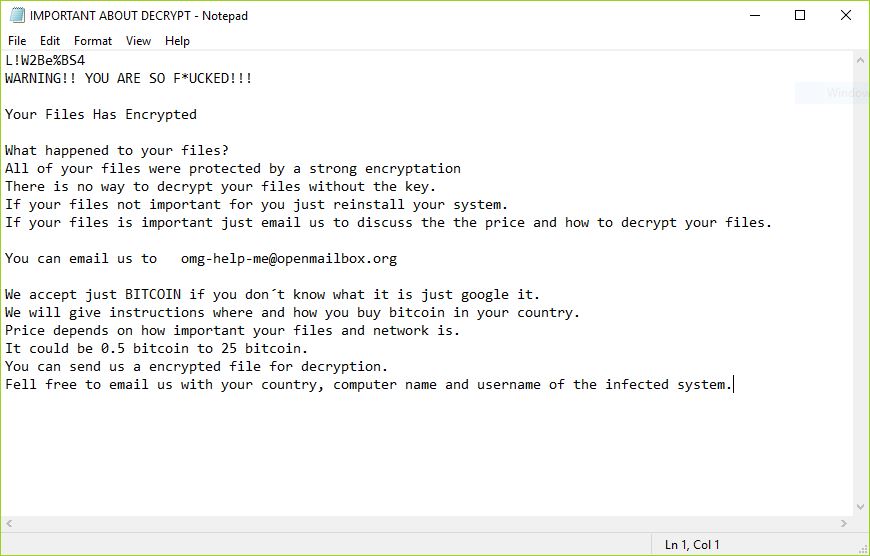
The OPdailyallowance Virus is a ransomware strain of the Hidden Tear family targeting computer users worldwide. The captured samples carry the initial infection commands, we presume that further updates to it may include newer components and additional instructions. Refer to…