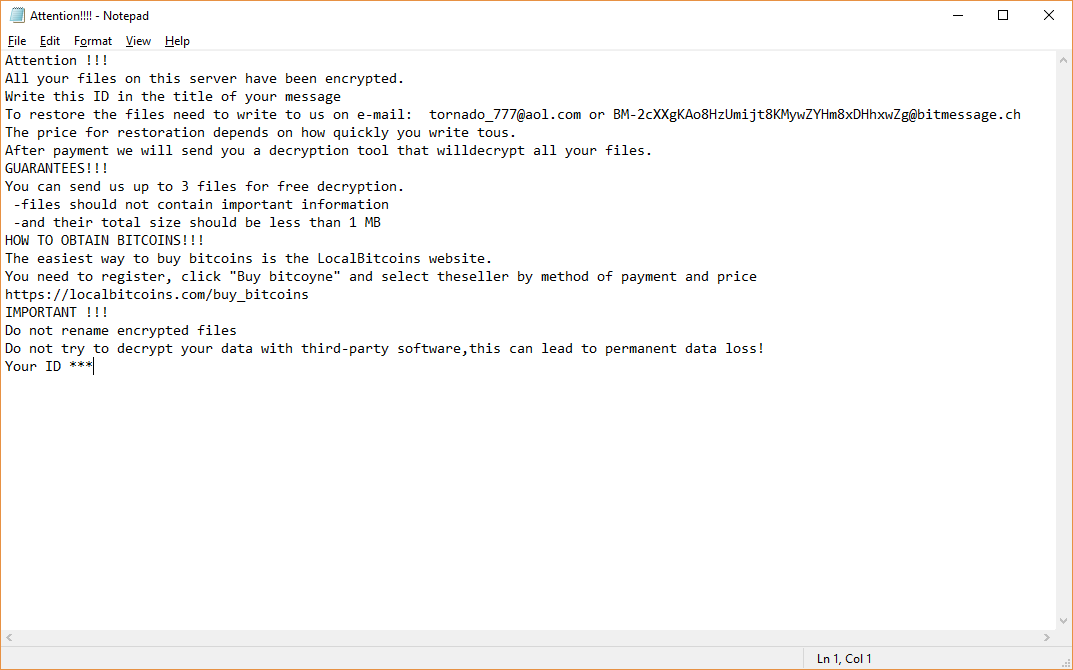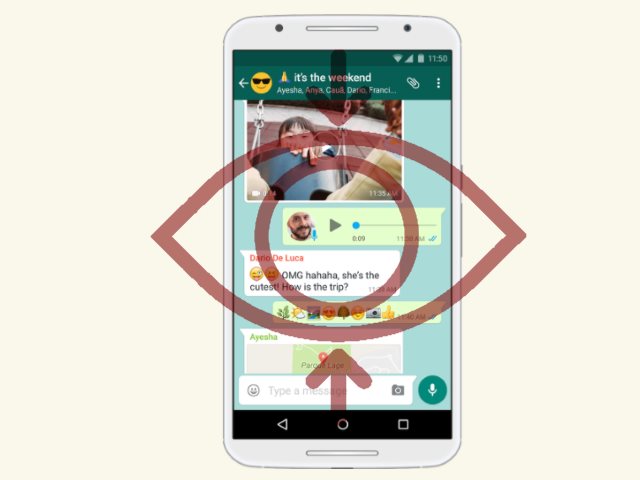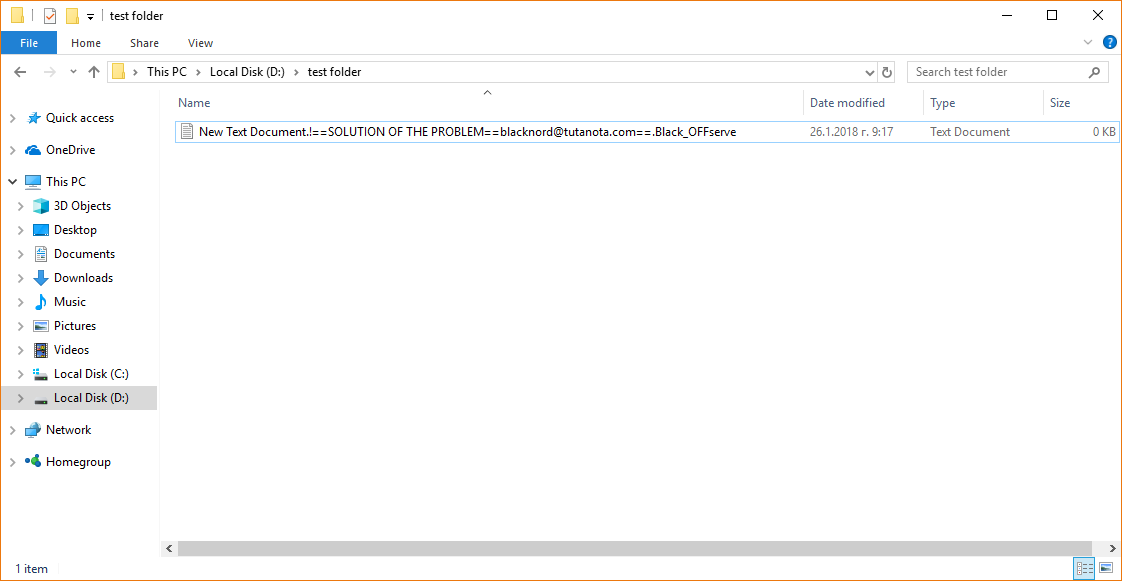
RotorCrypt Ransomware Removal – Restore .Black_OFFserve Files
Our RotorCrypt ransomware removal guide shows how computer users can restore their computers from the dangerous virus. It alters important settings on the system and can lead to further infections. Read our in-depth article to learn more about it. RotorCrypt…