iMovie Start Redirect — How to Remove it
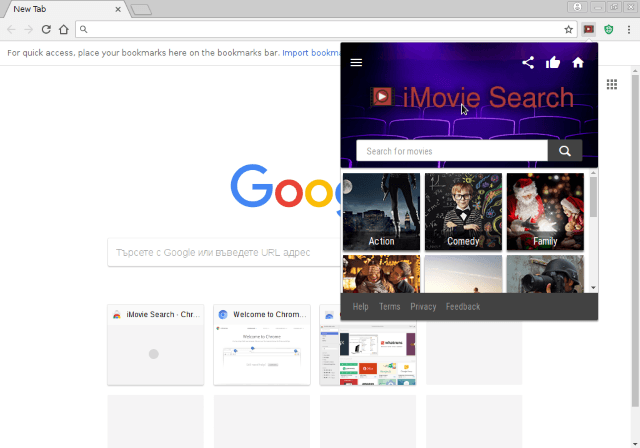
This article aims to help you with the removal of iMovie Start redirect from the affected PC and browsers. The iMovie Start redirect is a dangerous browser extension that is compatible with the most popular web browsers. It is classified…