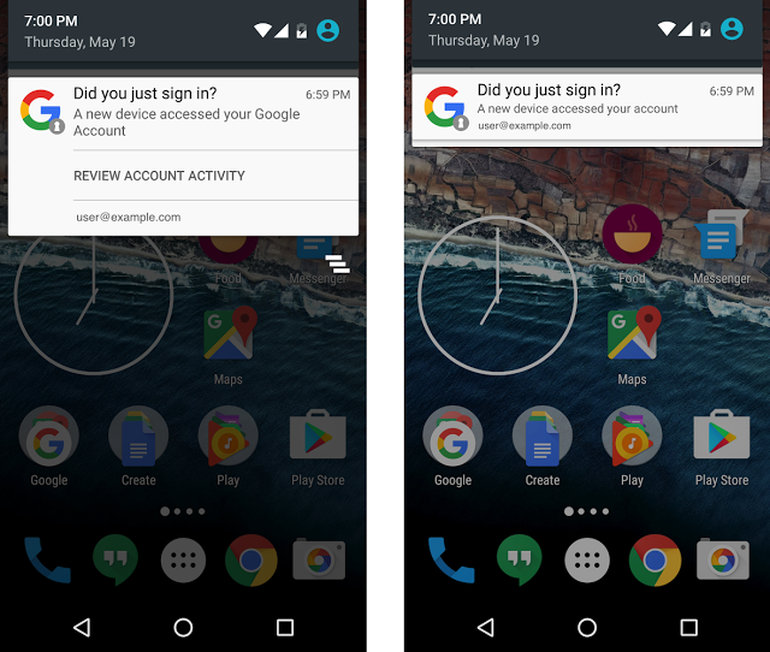
Battery Status API Employed for Online Tracking Reasons
Tracking is one of the serious privacy issues users are facing on a daily basis. If a party wants to get your personal information, it may get quite creative in the ways to obtain it. One of the most recent…