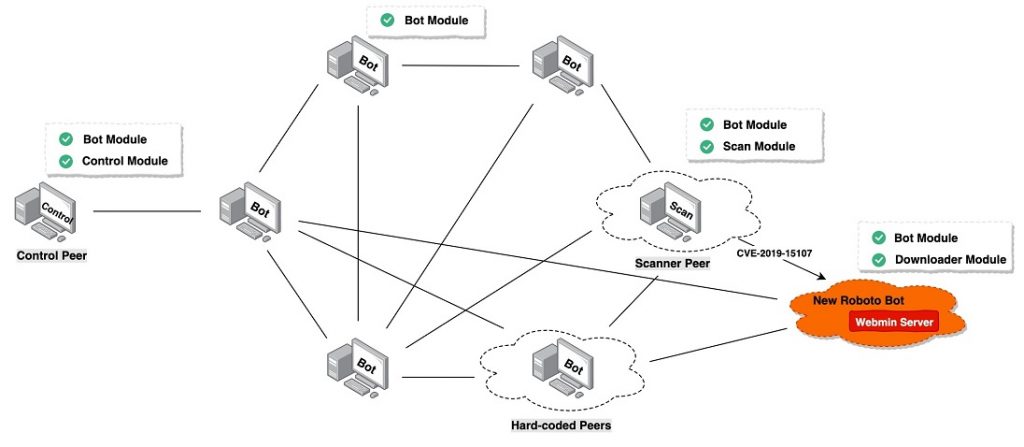
Deepfake Tech – How to Deal with This Growing Threat
Who would’ve thought that the face swap app we all have been enjoying on social media could be a tool that messes another person’s entire life or even a whole nation? Not everything we see is real – these lines…