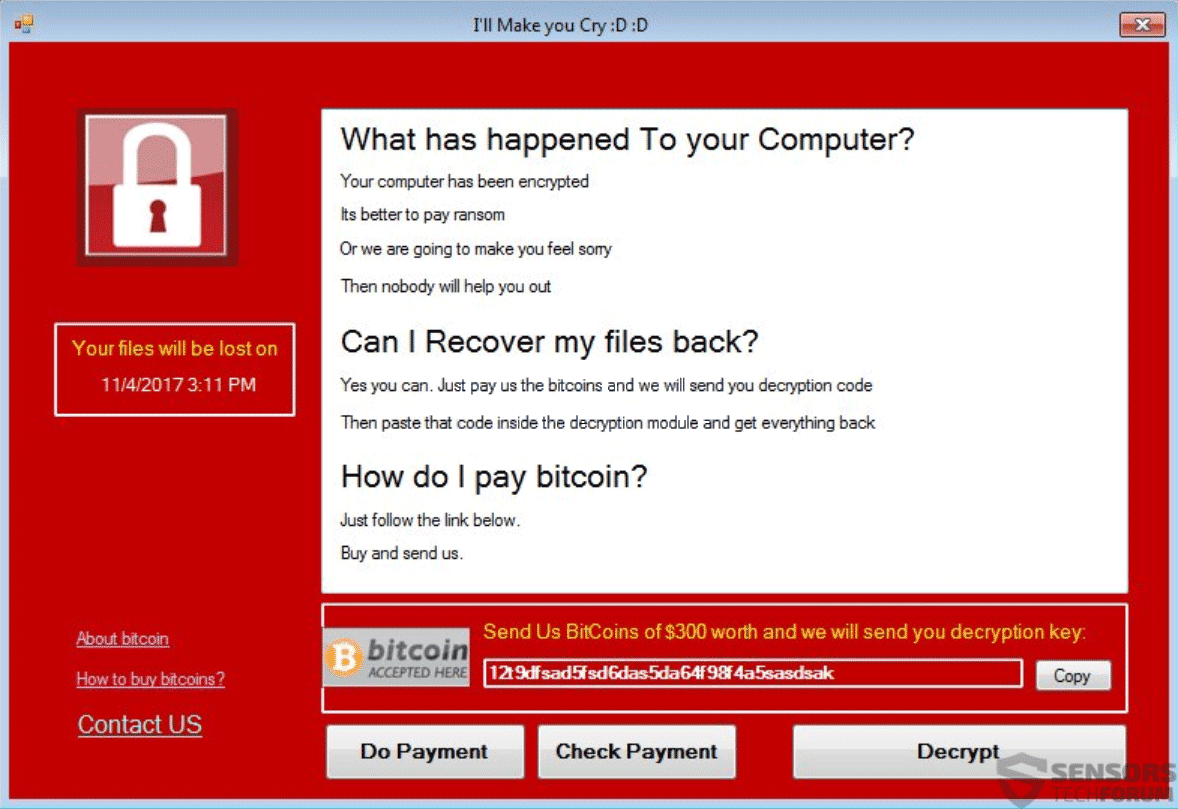
I’ll Make you Cry Virus Removal – Restore Files
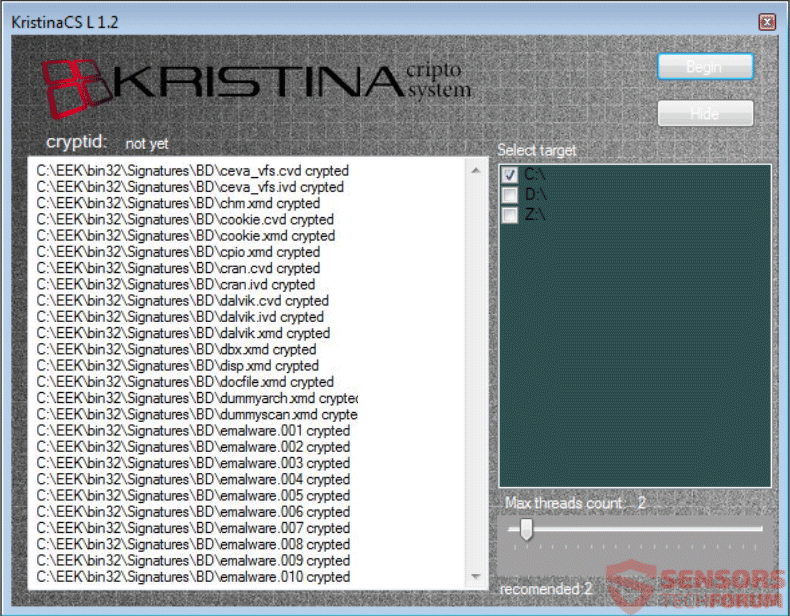
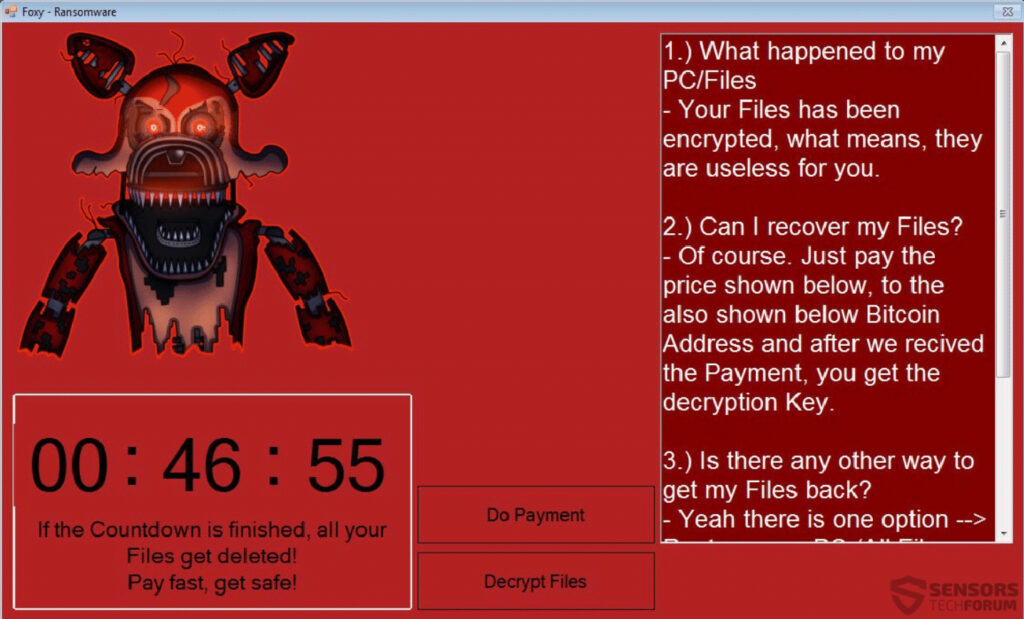
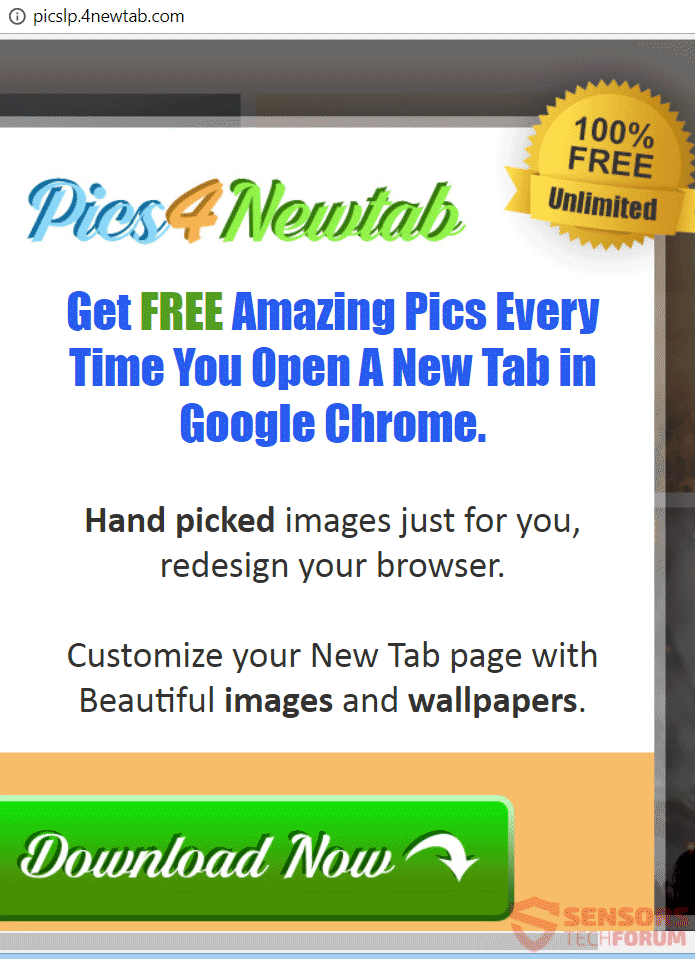
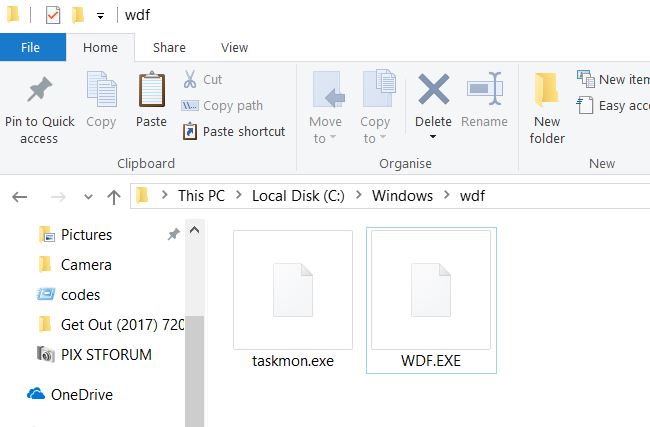
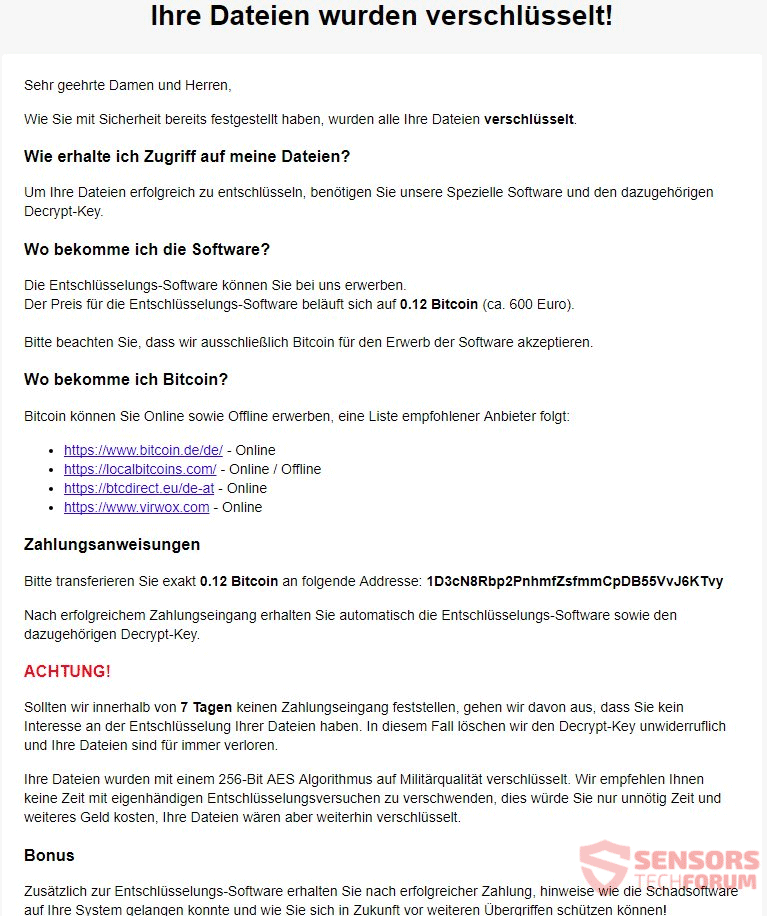
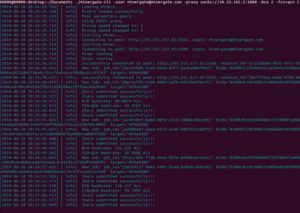
This article will aid you remove I’ll Make you Cry ransomware effectively. Follow the ransomware removal instructions at the end. I’ll Make you Cry is the name of a ransomware cryptovirus that has an interface imitating that of the WannaCry…