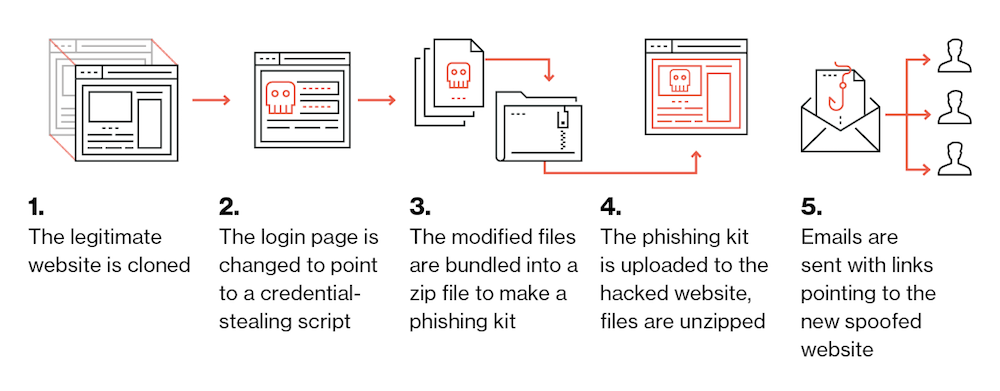
Phishing campaigns drive most of the malicious attacks in the wild, and as it turns out, cybercriminals have found an efficient way to optimize their effect. A new study reveals that attackers often re-use phishing websites across multiple hosts by bundling the site resources into a phishing kit.
The kits are then uploaded to a usually compromised host. The files in the kit are extracted, and phishing emails are sent leading to the new phishing site. What’s intriguing is that there are cases where the phishers leave these kits behind, allowing security researchers to download and examine them.
Researchers Analyze 66,000 URLs and 7,800 Phishing Kits
In the report, Duo security researchers have examined 66,000 URLs and more than 7,800 phishing kits. This is how they found two kits which were used on more than 30 hosts.
Other discoveries include:
– Many phishing kits were designed to bypass detection through the use of .htacess files and PHP scripts used to block connections from threat intelligence companies based on features such as the source IP address ranges, and the HTTP referrer of the user-agent header.
– Individual attackers from various campaigns were tracked by parsing each phishing kit for email addresses. One actor whose email address was found in more than 115 unique phishing kits was discovered.
– Unique phishing kits across multiple hosts were tracked. Plenty of kits seen on 30 different hosts were found, meaning that attackers launched multiple phishing campaigns using the same kit.
– More than 200 instances of backdoored phishing kits were disclosed. What does this mean? The phishing kit authors are selling backdoored kits to other attackers so that they get access to the compromised hosts.
– Phishing kits were mostly situated on compromised WordPress sites, and in 16% of the cases the kits were found on HTTPS sites.
– Shortly said, the re-using of phishing kits improves the ROI of these campaigns, and it also spares cybercriminals the time of recreating various assets for each new campaign.
For further information, jump to the full report.