What Is Ransomware?
Ransomware is a type of malicious software that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. While it can affect individuals, its primary targets often include corporations, government agencies, and other organizations holding sensitive data. This malicious program encrypts files on the infected system, making them inaccessible, and demands ransom, usually in cryptocurrency, to provide the decryption key.
The rise of ransomware over recent years highlights a significant cyber threat, with notorious examples like CryptoLocker, WannaCry, and NotPetya demonstrating its destructive potential.
Ransomware – Details
| File Extension | Depending on the variant |
| Type | Malware, Cryptovirus |
| Short Description | The ransomware encrypts files on your computer system and demands a ransom to be paid to allegedly recover them. In other cases, ransomware operators use double and triple extortion techniques, in which they threaten releasing stolen data to the public. |
| Symptoms | Encrypted data; a ransom note is dropped |
| Distribution Method | Spam Emails, Vulnerability Exploitation |
| Detection Tool |
See If Your Mac Has Been Affected by Ransomware
Download
Malware Removal Tool
|
Ransomware Spread and Distribution
Ransomware typically enters through seemingly innocuous actions, turning ordinary online behavior into a risk. Common entry points include:
- Phishing emails. These are deceptive emails that trick recipients into clicking on malicious links or attachments. They often appear to be from reputable sources, making them highly effective.
- Exploited vulnerabilities. Unpatched software is a prime target for attackers. By exploiting known security holes, they can inject ransomware without any user interaction.
- Brute force attacks. Attackers use automated tools to guess weak passwords, gaining unauthorized access to systems.
Each entry point represents a potential security gap that can be minimized with vigilant digital hygiene practices and the implementation of security measures like multifactor authentication (MFA) and regular software updates.
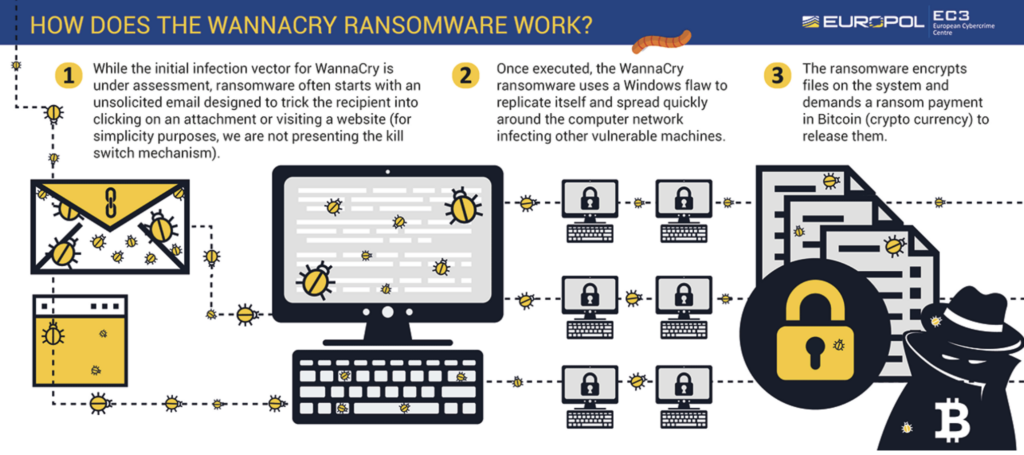
One of the most common ways ransomware spreads is through email attachments, in smartly curated phishing messages. Attackers send phishing emails or malicious emails designed to trick recipients into opening an infected file. These emails often use social engineering techniques, such as impersonating trusted contacts or companies, to increase the likelihood that the target will open the email and download the attachment.
In more sophisticated attacks, spear-phishing is employed, where the email is customized to specific individuals or organizations, making the attack seem more credible.
Inside these email attachments, ransomware often lurks in files that contain a malicious macro. When the victim enables the macro, believing it is a harmless function, the ransomware is executed and begins encrypting files on the system.
Beyond email, exploit kits are another method used to distribute ransomware. These kits take advantage of vulnerabilities in software or operating systems, allowing attackers to deploy ransomware onto systems without requiring the user to interact with an email or file. Malvertisements (malicious advertisements) also play a role in ransomware distribution, often appearing on legitimate websites. When users click on these compromised ads, they are redirected to websites that exploit vulnerabilities and install ransomware.
For cybercriminals who lack the technical expertise to develop ransomware, Ransomware as a Service (RaaS) has emerged. RaaS provides ready-made ransomware kits that criminals can lease, offering a low barrier of entry for would-be attackers to launch their own ransomware campaigns.
To combat these threats, organizations rely on a combination of secure email gateways and secure web gateways. Secure email gateways help filter out malicious and phishing emails, stopping ransomware before it reaches users’ inboxes. Similarly, secure web gateways prevent users from accessing dangerous websites that could deliver ransomware via malvertisements or exploit kits.
In response to the rise in targeted attacks, targeted attack protection solutions have also become critical. These systems offer advanced security layers that defend against highly tailored attacks like spear-phishing, where traditional defenses might fail. By using a multi-layered approach, combining social engineering defenses, phishing detection, and secure gateways, organizations can better protect themselves from the widespread and evolving threat of ransomware.
Impact of Ransomware on Businesses and Individuals
So, why should this concern you? Ransomware doesn’t discriminate, as it can target anyone, from small businesses to large enterprises, as well as individual users. The implications of an attack can be devastating, ranging from irreversible data loss to substantial financial consequences.
Moreover, the sophistication of ransomware attacks is continually evolving, with perpetrators employing methods such as double and triple extortion tactics. These do not only encrypt your data but also threaten its leak, amplifying the potential for reputational damage and compliance issues.
- Financial Impact: Beyond the ransom payment – which might not even result in the recovery of data – the financial toll includes downtime, lost productivity, forensic investigation, data recovery, and, in some cases, legal consequences stemming from compromised personal data.
- Operational Disruption: An attack can halt business operations instantly. The time to recover, depending on the attack’s scale and the backup solutions in place, can vary widely, significantly impacting service delivery and operational continuity.
- Reputational Damage: Trust is hard to earn and easy to lose. An organization’s reputation can be severely tarnished if stakeholders feel their data isn’t adequately guarded, leading to lost business and strained relations.
- Regulatory Consequences: Depending on the nature of the data compromised and the jurisdiction, organizations could face hefty fines and legal action for failing to secure sensitive information adequately.
The emergence of ransomware as a service (RaaS) has further democratized access to this malicious technique, allowing individuals without technical know-how to launch ransom attacks. This trend indicates a rising threat landscape that requires vigilant defense mechanisms. Effective prevention and detection strategies are paramount, including regular backups, comprehensive endpoint protection, user education, and incident response planning. These measures not only help in mitigating the risk but also ensure a quicker recovery should an attack occur.
The Rising Costs of Ransomware Attacks
The financial landscape of cybersecurity has been drastically altered by ransomware attacks, with last year marking a significant surge in both frequency and the financial demands of attackers. The stark increase in ransomware payments, reaching $1.1 billion from the previous $567 million in 2022, showcases the growing boldness and sophistication of cybercriminals.
This escalation is not just about the ransom payments themselves but encompasses the broader economic fallout, including the costs of detection, response, and the long-term impact on brand reputation and operational downtime. For businesses, this upswing signals an urgent need to prioritize robust cybersecurity measures as ransomware morphs from a potential risk to a common occurrence.
Global Statistics
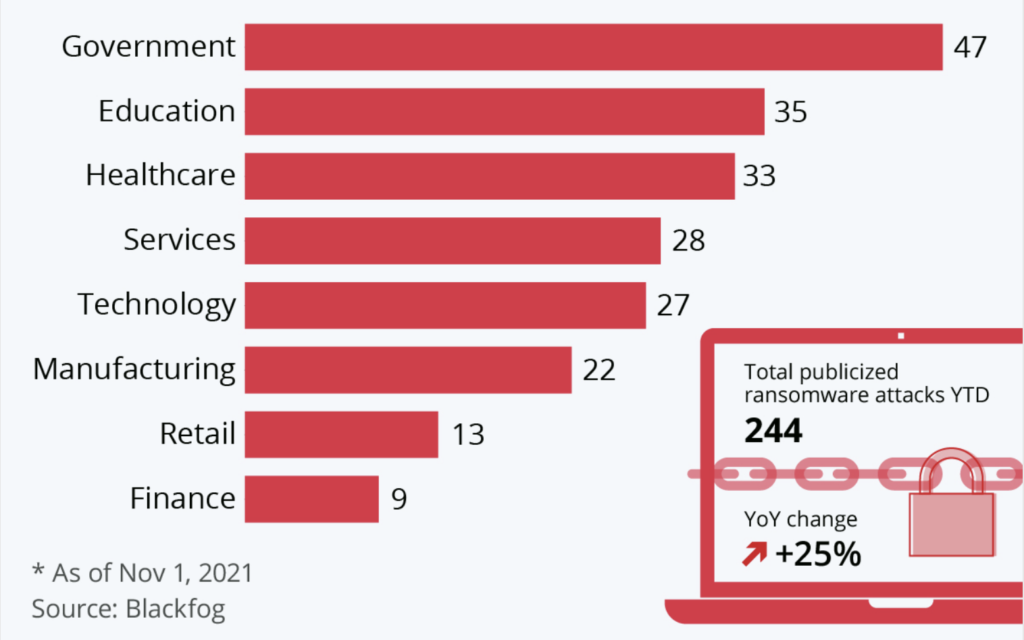
Ransomware has proven to be a global threat, with attackers not discriminating by geography, industry, or company size. In 2023, organizations in the U.S. were hit hardest, amounting to 47 percent of all attacks, yet the wave of ransomware has touched every corner of the world. The financial implications have been staggering, with some incidents demanding as much as $70 million to restore access to encrypted data.
While the immediate focus tends to be on the ransom demanded by attackers, which averaged $2.73 million in 2024, the true economic toll of ransomware lies in its aftermath. Businesses face substantial operational downtime, with the average company experiencing a shutdown of 24 days.
It is noteworthy that ransomware is expected to be a prevalent threat in 2025, with expected sophistication in criminal tactics and proliferation in ransomware-as-a-service endeavors. Furthermore, despite growing awareness, many organizations still lack adequate cybersecurity policy in place, such as regular backups, endpoint protection, and employee training, leaving them vulnerable to attacks.
This downtime, coupled with the costs of remediation, and the potential hit to the company’s reputation, often exceeds the ransom amount itself by five to ten times. Furthermore, the recurrence of attacks against companies that have previously paid ransoms highlights the importance of investing in preventative measures rather than relying on post-attack payouts. This predicament underlines the critical necessity for comprehensive cybersecurity solutions like SpyHunter, which are designed to detect and remove ransomware threats, thereby safeguarding businesses from the immense costs associated with these cyberattacks.
Ransomware Prevention Techniques
In the fight against ransomware, certain best practices have proven to be particularly effective. Here are the top five strategies that businesses and individuals should adopt:
- Regular System Updates: Keep all systems and software up-to-date. Software updates often include patches for security vulnerabilities that ransomware attackers can exploit.
- Strong Authentication Measures: Utilize multi-factor authentication (MFA) and strong, unique passwords for all accounts. This adds an extra layer of security, making it harder for attackers to gain unauthorized access.
- Email Security Awareness: Train employees to recognize phishing attempts and malicious attachments. Human error can often be the weakest link in cybersecurity, so fostering a culture of vigilance is crucial.
- Restrict User Access: Apply the principle of least privilege, giving users access only to the information and resources necessary for their roles. This minimizes the potential impact of an attack.
- Routine Data Backups: Regularly back up data and ensure these backups are stored securely off-site or in the cloud. In case of a ransomware attack, having up-to-date backups is your safety net for recovery.
Strong Cyber Hygiene
Good cyber hygiene practices are central to preventing ransomware attacks. This involves simple, routine actions that each member of your organization can perform to maintain the security of its digital assets. Here are some key steps:
- Software Maintenance: Regularly update and patch all software, operating systems, and firmware to close off vulnerabilities.
- Secure Configuration: Ensure that all systems are configured securely by default, reducing unnecessary exposure to threats.
- Control Network Access: Use firewalls, segment networks, and control who has access to what parts of your network to minimize the risk of an attack spreading.
- Antivirus Protection: Deploy reputable antivirus and anti-malware solutions, like SpyHunter, which can detect and block ransomware and other malware before it compromises your system.
Developing these habits among all users within your organization can dramatically reduce the risk of a ransomware infiltration.
Regular Data Backups
Backing up data regularly is one of the most effective defenses against ransomware. It ensures that, in the event of an attack, you can restore your systems and data without paying a ransom. Here’s why routine backups are vital:
- Rapid Recovery: Quickly regain access to your data following an attack, minimizing downtime and operational impact.
- Data Integrity: Maintain control over the integrity of your data, ensuring that you can recover unaltered versions of your important files.
- Cost Savings: Avoid the financial burden of paying ransoms, which not only encourages further attacks but often doesn’t result in data recovery.
To maximize the effectiveness of your backups, adhere to the 3-2-1 rule: keep three total copies of your data, in two different formats, with one of those copies off-site or in the cloud. Regular testing of your backups is critical to ensure they can be quickly and effectively restored when you need them.
Ransomware Response and Recovery
When a ransomware attack occurs, a swift and organized response is crucial to mitigate damage and recover systems. The first step in any ransomware response is containment. This involves taking immediate action to stop the spread of the ransomware across the network. Network isolation is key here, disconnecting infected systems from the broader network to prevent further infection. Identifying the patient zero, or the first infected system, helps trace the source of the attack and evaluate its impact.
Once the ransomware is contained, it’s important to identify the specific ransomware variant. Knowing which variant is in play helps determine available decryption options. Websites like No More Ransom, a collaboration between cybersecurity companies and law enforcement, offer free decryption tools for certain ransomware variants, potentially avoiding the need for a ransom payment:
At this point, a thorough backup evaluation is essential. Well-maintained backups are one of the most effective ways to recover from a ransomware attack without paying the ransom. If clean, unaffected backups are available, backup restoration can be initiated to restore systems to their pre-attack state. It’s important to ensure that these backups are not infected and are up-to-date to avoid reinfecting the restored systems.
Forensic analysis should also be performed to understand how the ransomware entered the system. This often involves tracking down malicious email links or attachments that were used in phishing attacks. The presence of strong antivirus/antimalware solutions can help detect these initial vectors and prevent future attacks.
Reporting the incident to authorities through law enforcement is crucial, both to comply with regulations and to assist in broader efforts to track and dismantle ransomware groups. Law enforcement agencies may also provide valuable resources and guidance on recovery strategies.
In cases where no decryption tool is available and backups are compromised, some organizations may feel forced to consider ransom payment. However, this should be a last resort, as paying does not guarantee the recovery of data and may encourage further attacks. Comprehensive post-attack assessments should include improving security measures, updating antivirus/antimalware solutions, and re-evaluating backup strategies to ensure the organization is better prepared for future incidents.
Immediate Actions to Take Post-Detection of Ransomware
- Isolate Affected Systems: Immediately disconnect the infected devices from all network connections, both wired and wireless. This step prevents the ransomware from spreading to other devices.
- Power Down or Lock Out: If disconnection is not possible, power down the affected devices or lock out network access to these systems. This approach helps to contain the ransomware to the devices already impacted.
- Analyze the Impact: Quickly identify which systems are infected and classify them based on their criticality to your operations. This will help in prioritizing recovery efforts.
- Secure Your Backups: Verify that your backups are intact and have not been compromised by the attack. Secure backups are essential for recovery, so ensure they are disconnected from the network and unharmed.
- Contact Authorities: Reporting the incident to law enforcement can provide you with additional resources and support, and it may also help in tracking down the attackers.
Engaging a cybersecurity expert during this phase can provide the necessary insight into the attack vector and help in formulating an effective containment strategy. In scenarios where the complexity of ransomware demands specialized expertise, software like SpyHunter can be a valuable ally in identifying and removing malware threats.
Analysis and Recovery
Post-attack analysis and recovery require a structured approach to restore operations and prevent future incidents. A thorough investigation will reveal the extent of the damage, the ransomware’s entry point, and any potential backdoors left by attackers.
- Eradicate the Ransomware: Use reliable malware removal tools to completely eradicate the ransomware from all affected systems. This step is critical before any restoration efforts begin to prevent re-infection.
- Investigate and Learn: Conduct an in-depth analysis to understand how the ransomware entered your system, what vulnerabilities were exploited, and whether any data was exfiltrated.
- Restore from Backups: Once you’re confident that the ransomware has been fully removed, begin restoring data from clean backups. Prioritize systems based on their importance to your business operations.
- Strengthen Your Defenses: Based on the insights gained from the attack, update your security protocols, software, and employee training to defend against future threats.
- Continuously Monitor: Keep a vigilant eye on your systems for any signs of unusual activity or repeated infections, as attackers often attempt to re-infect systems that have been previously compromised.
To ensure efficient recovery and future resilience, turning to trusted cybersecurity solutions such as SpyHunter can provide ongoing protection against a wide array of malware threats, including sophisticated ransomware variants. The post-recovery phase is an opportunity to reinforce your cybersecurity posture with advanced detection, response capabilities, and regular system updates.
Ransomware Removal and System Restoration Techniques
How to Remove Ransomware Safely Without Paying the Ransom
Ridding your system of ransomware without fulfilling ransom demands can be challenging, but it is certainly achievable with the right steps. First and foremost, disconnect the infected device from all networks and external devices to prevent the spread of ransomware. Run a reputable anti-malware tool, like SpyHunter, to thoroughly scan and remove any traces of the ransomware from your system. SpyHunter’s specialized ransomware detection capabilities make it an effective tool for identifying and isolating threats that traditional antivirus software might miss.
Following the removal of the malicious software, it’s vital to assess the damage. Examine your files and system to understand what has been encrypted or affected. This will help you in the next steps of data recovery and system restoration.
How to Restore Your Data
Once you’ve managed to remove the ransomware from your system, the next crucial step is to restore your data. If you’ve maintained regular backups of your data, recovering your files will be significantly more straightforward. Here’s how you can go about it:
- Firstly, ensure that all ransomware has been completely eliminated from your system to prevent re-encryption of your restored data.
- Restore your files from backups. If you’ve used cloud-based storage solutions or physical backup drives (kept disconnected from the network), you can now retrieve your data.
- In cases where backups aren’t available, look into decryptor tools. Organizations like No More Ransom provide decryptors for some ransomware variants, offering a glimmer of hope for affected users to recover their files without payment.
- Lastly, consider professional data recovery services as a last resort. Specialized experts might recover certain data types, though success isn’t guaranteed and can be costly.
Remember, prevention is always better than cure. Investing in comprehensive security software like SpyHunter, maintaining regular data backups, and staying informed about cybersecurity practices can significantly reduce the risk of ransomware attacks and their impact on your systems.
Why Choose SpyHunter for Enhanced Ransomware Protection
In an age where ransomware attacks are on the rise, affecting both individuals and large organizations alike, the need for effective defenses has never been more critical. SpyHunter emerges as a formidable ally in this ongoing battle, offering comprehensive protection tailored to counter the latest ransomware threats. This segment shines a spotlight on why SpyHunter stands out as a preferred choice for enhancing ransomware protection and how it effectively defends users from these malicious threats.
With the digital environment constantly evolving, ensuring the utmost security against ransomware demands a solution that is both dynamic and resilient. SpyHunter answers this call by providing advanced security features that are designed to adapt to the changing tactics of ransomware attackers. Here are key reasons to consider SpyHunter for your ransomware defense needs:
- Real-time Protection: SpyHunter operates on a real-time basis, actively monitoring your computer for any signs of ransomware. Its proactive approach ensures threats are identified and stopped before they can cause damage.
- Comprehensive Malware Detection: Utilizing a combination of signature-based and heuristic detection methods, SpyHunter is capable of identifying both known ransomware variants and new, previously unseen threats.
- User-Friendly Interface: SpyHunter is designed with simplicity in mind, making it accessible for users of all technical levels. Its straightforward interface allows for easy navigation and management of security settings.
- Regular Updates: The threat landscape is always changing, but so is SpyHunter. With regular updates to its malware definition database, SpyHunter stays one step ahead of ransomware attackers.
- Custom Fix Solutions: In the event that a particularly stubborn piece of malware manages to infiltrate, SpyHunter offers custom fixes tailored to the specific threat, ensuring complete removal.
Ransomware Predictions and Future Trends
The next decade is set to witness significant shifts in ransomware strategies, influenced by technological advancements and changing global dynamics. Based on current trends, we can expect an increase in ransomware collaborations among cybercriminals across different countries. This globalization of ransomware operations will likely enhance their effectiveness and evade detection and prosecution more easily. Furthermore, ransomware is projected to become the leading tactic in software supply chain attacks, posing a serious risk to third-party data security.
Adoption of Zero-Trust network access models is anticipated to grow, with projections suggesting that 30 percent of organizations will implement these strategies in the upcoming years. This shift underscores the urgency in adopting more secure and controlled network access to mitigate ransomware risks. Also, by 2025, 60 percent of organizations might consider cybersecurity risks before entering new business ventures, highlighting the escalating importance of cybersecurity in business strategies.
Ransomware’s future also hints at more sophisticated and targeted attacks. Governments’ increasing intervention is expected to impact the ransomware scene, potentially leading to a drop in average ransom payments due to better preparedness and response strategies.
Emerging Technologies and Their Impact on Ransomware Defense
The advancement of technology plays a pivotal role in both the development and defense against ransomware. Edge and Fog computing, enhanced by federated learning, presents a new horizon for ransomware detection and prevention. These technologies promise to decentralize the processing power, enabling real-time threat detection closer to the source of data generation, thus potentially limiting the spread of ransomware.
However, the rise of DeepFake technology introduces new concerns. Ransomware attacks leveraging DeepFakes could coerce individuals into paying ransoms to prevent the release of fabricated, incriminating content. This underscores the need for sophisticated detection mechanisms to differentiate real from manipulated content.
The rise of remote work due to the COVID-19 pandemic has exposed vulnerabilities that ransomware attackers exploit. This makes the development of secure remote working environments a critical focus area for cybersecurity efforts.
Moreover, blockchain technology offers a novel approach to ransomware defense. Its decentralized nature and the use of smart contracts could revolutionize how we prevent ransomware proliferation and respond to attacks, making unauthorized data alterations detectable and reversible.
Lastly, Ransomware-as-a-Service (RaaS) has democratized the tools necessary for carrying out ransomware attacks, leading to a potential surge in attacks by less experienced cybercriminals. This shift highlights the need for continued innovation in cybersecurity defense mechanisms, including the deployment of comprehensive security solutions like SpyHunter, which can offer protection against such diverse ransomware threats.
Conclusion
In conclusion, understanding the evolving landscape of ransomware and the impact of emerging technologies on its defense is crucial. By staying informed and prepared, individuals and organizations can better safeguard themselves against the complex threats posed by ransomware. SpyHunter’s role in this landscape becomes increasingly critical, offering protection tailored to meet these emerging challenges head-on.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for Ransomware with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall Ransomware and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by Ransomware on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Ransomware there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove Ransomware





Step 5: Try to Restore Files Encrypted by Ransomware.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
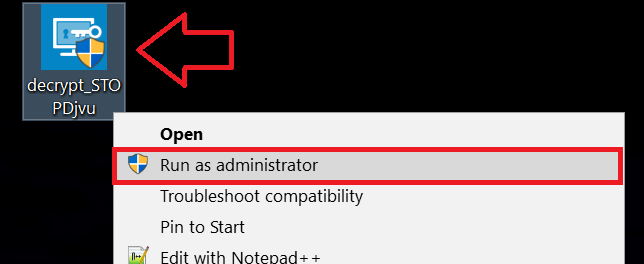
1 Right-click on the decrypter and click on Run as Administrator as shown below:
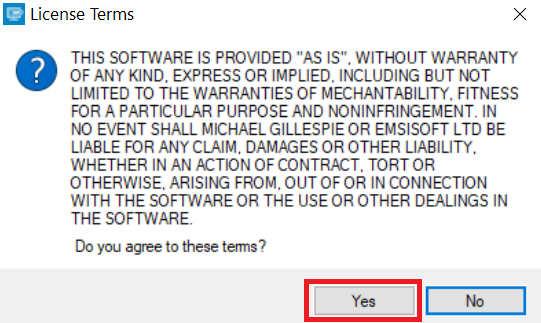
2. Agree with the license terms:
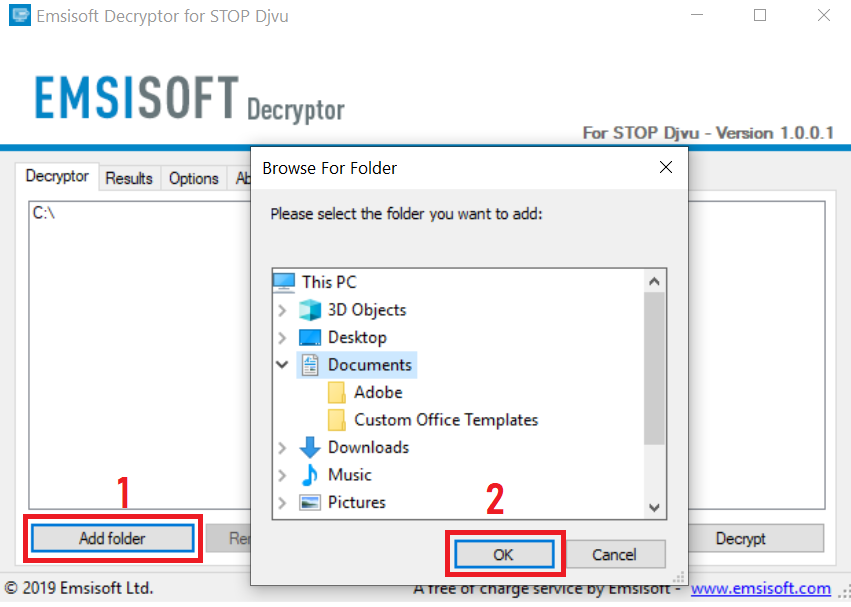
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
4. Click on "Decrypt" and wait for your files to be decoded.
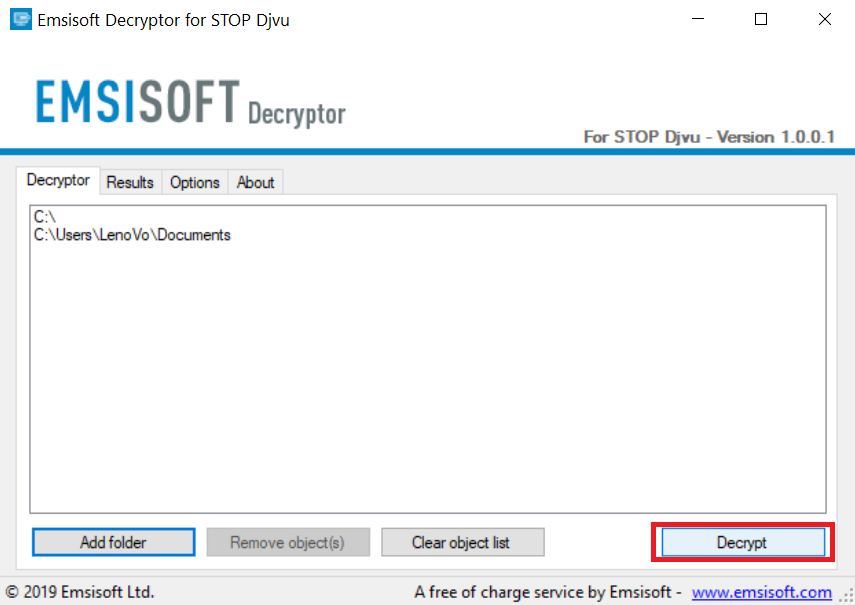
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and Ransomware aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
Ransomware-FAQ
What is Ransomware Ransomware?
Ransomware is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does Ransomware Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does Ransomware Infect?
Via several ways.Ransomware Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of Ransomware is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .Ransomware files?
You can't without a decryptor. At this point, the .Ransomware files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .Ransomware files successfully, then do not despair, because this virus is still new.
Can I Restore ".Ransomware" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .Ransomware files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of Ransomware Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate Ransomware ransomware and then remove it without causing any additional harm to your important .Ransomware files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can Ransomware Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the Ransomware Research
The content we publish on SensorsTechForum.com, this Ransomware how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the Ransomware ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.


