Shellshock Attacks Increase Fast
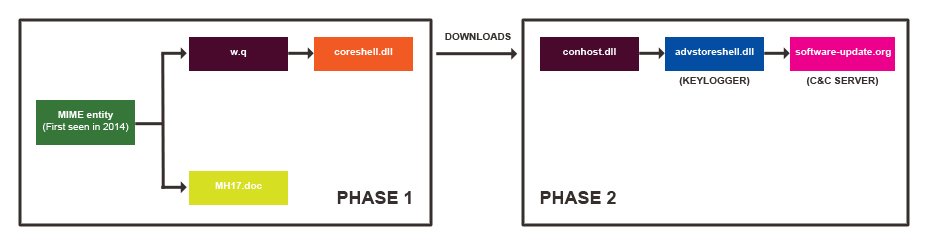
Companies cannot manage to patch up their processes in the wake of Bash vulnerability. Security experts have issued two warnings regarding new malicious attacks associated with Shellshock, as they observe a rapidly growing number of cybercriminals who take advantage of…