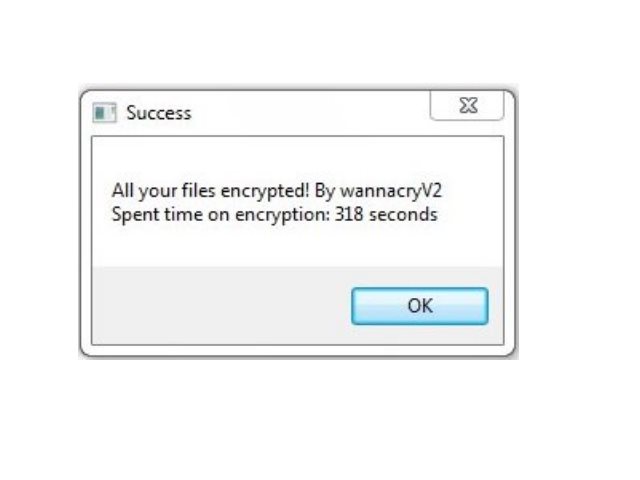
CVE-2017-7150: Mac OS X Warning Prompts Can Be Easily Bypassed
Mac OS X computers have been found vulnerable due to a report indicating that warning prompts can be easily bypassed. A demonstration has shown how this can be used by hackers in virus infections. The vulnerability is classified as a…





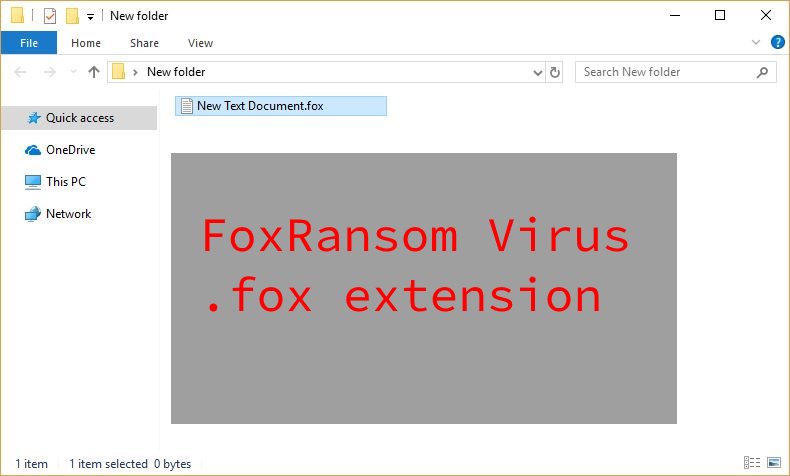
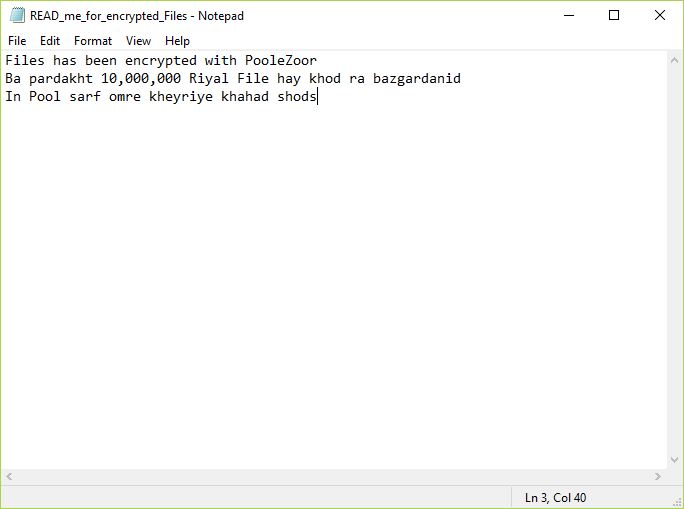
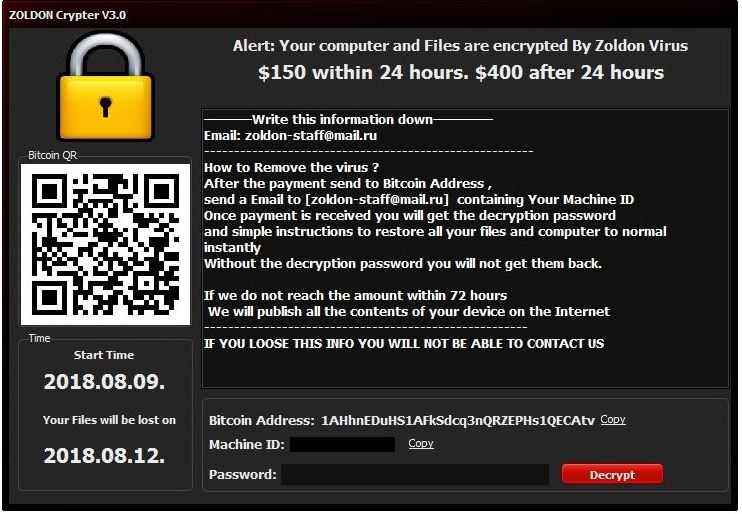
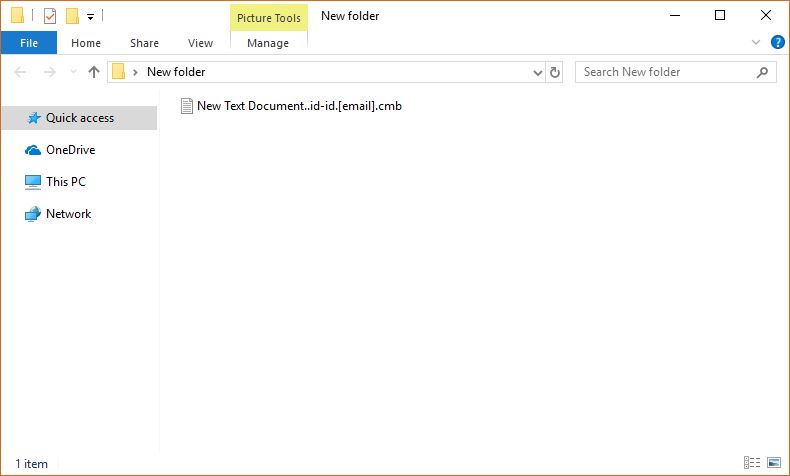



![Remove Yourencrypter@protonmail.ch Virus Infections Yourencrypter@protonmail.ch Virus image ransomware note Yourencrypter@protonmail.ch.[random ext] extension](https://cdn.sensorstechforum.com/wp-content/uploads/2018/08/Yourencrypter@protonmail.ch-virus-image-sensorstechforum-com.jpg)