Fuchsia – the New OS by Google Expected to Replace Android
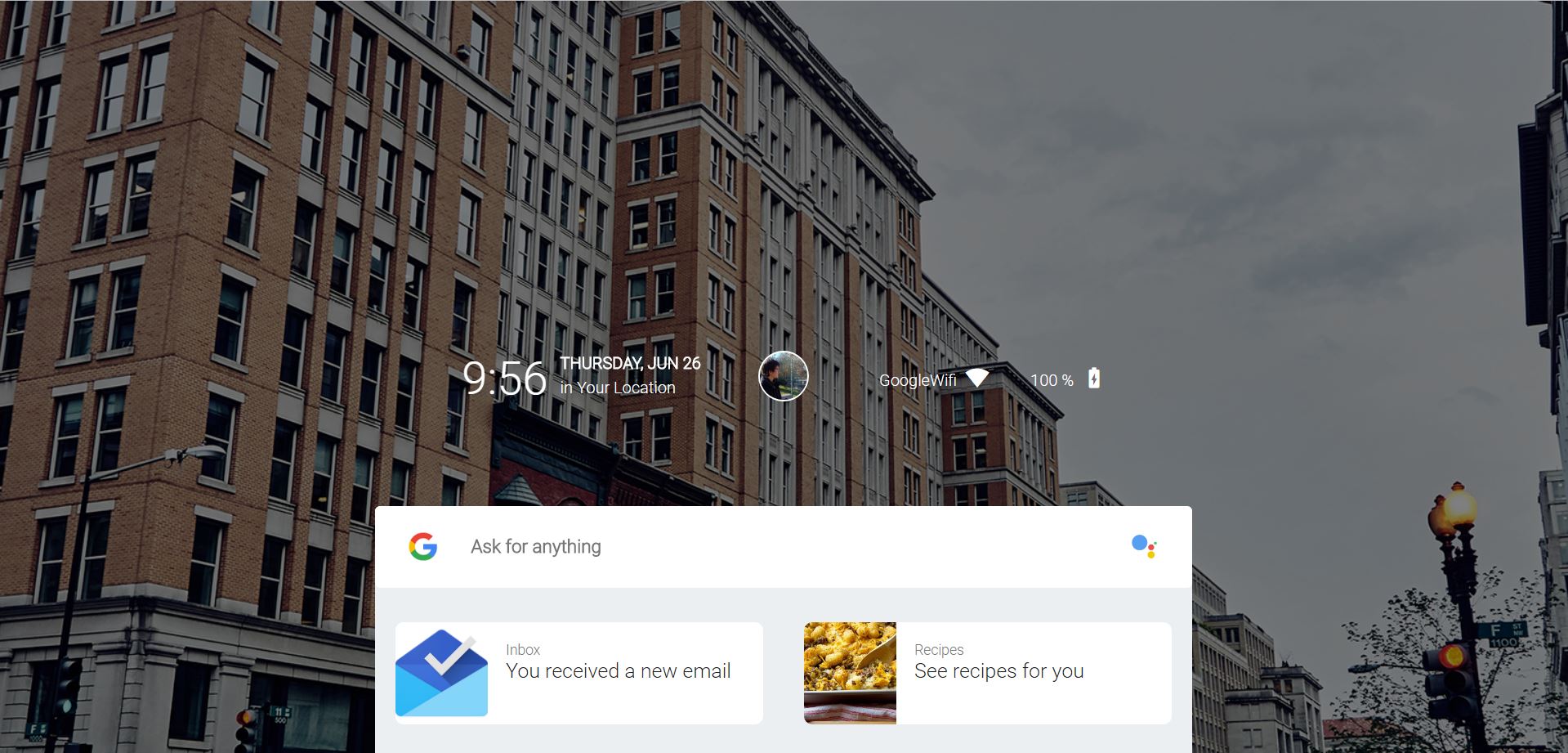
It’s been two years from now since Google uploaded Fuchsia online and made it public. Fuchsia is a new operating system created from scratch. It is intended to overcome some of the Android limitations. Engineers behind the project believe that…