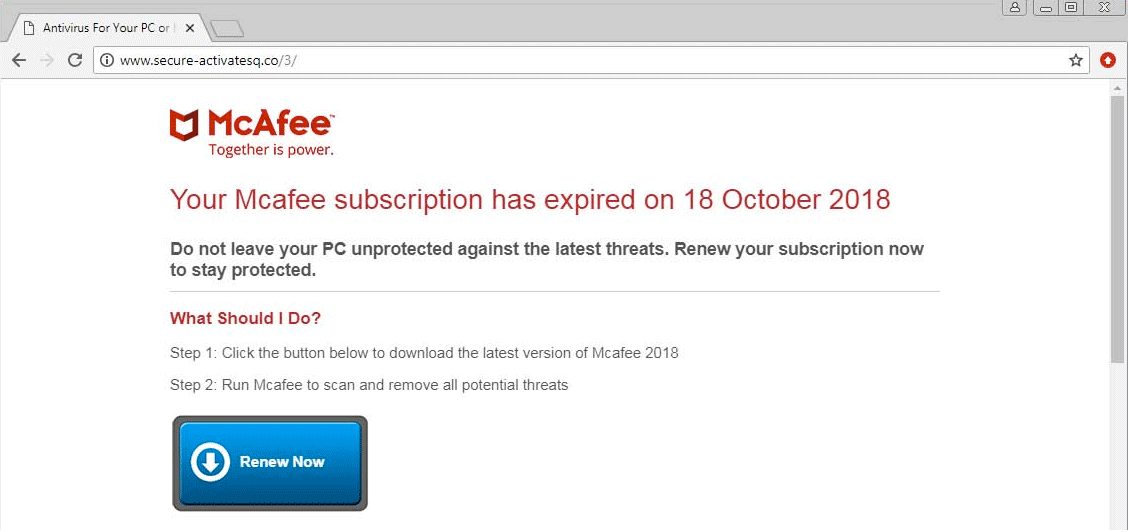
Self-Encrypting SSDs Contain Multiple Vulnerabilities, Researchers Find
Security researchers have just discovered several vulnerabilities in some SSDs that could allow a threat actor to bypass the disk encryption feature and access local data. To do that, the attacker doesn’t need to know the user’s disk encryption password.…