Adobe Flash Player has been long targeted by hackers. Plenty of vulnerabilities have been uncovered during the years, and plenty of attacks based on Adobe flaws have been crafted.
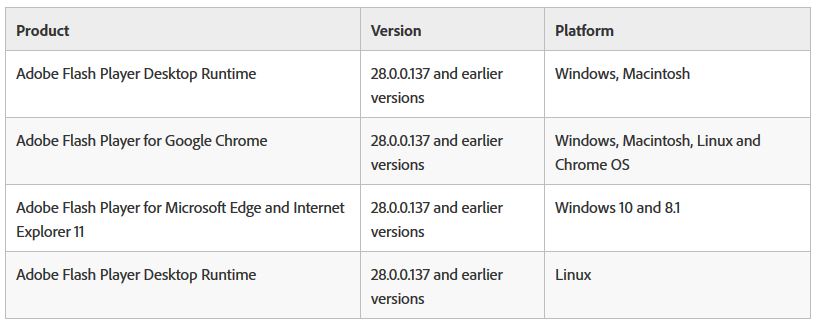
This year also starts off with a critical vulnerability that was confirmed by Adobe itself – CVE-2018-4878. Adobe Flash Player 28.0.0.137 and earlier versions are affected. The flaw exists in Flash Player and allows attackers to gain access to machines running on several platforms, like Windows, Macintosh, Google Chrome and Linux:
A fix is expected to be released in the upcoming days. However, in the meantime users still using the program are urged to check whether they are prone to the exploit and are advised to harden their defenses. Furthermore, CVE-2018-4878 is being exploited in limited, targeted attacks in the wild. Here’s what Adobe has said in a security bulletin:
A critical vulnerability (CVE-2018-4878) exists in Adobe Flash Player 28.0.0.137 and earlier versions. Successful exploitation could potentially allow an attacker to take control of the affected system.
Adobe knows about the report that an exploit for CVE-2018-4878 exists in the wild, and is being leveraged in limited, targeted attacks against Windows. These attacks use Office documents with embedded malicious Flash content spread via email, the company also said.
More about CVE-2018-4878
The vulnerability is a use-after-free type. A use-after-free vulnerability is a memory corruption character and can be exploited by attackers to execute arbitrary code.
Attacks Based on CVE-2018-4878
Cisco researchers’ analysis of the CVE-2018-4878-based attack linked it to the hackers from Group 123.
“Group 123 have now joined some of the criminal elite with this latest payload of ROKRAT. They have used an Adobe Flash 0 day which was outside of their previous capabilities — they did use exploits in previous campaigns but never a net new exploit as they have done now,” Talos researchers Warren Mercer and Paul Rascagneres stated.
The researchers also believe that the target of the attack is high-profile. The fact that a brand new exploit not seen in previous attacks was used means that the group was determined to make the attack work.
FireEye researchers, on the other hand believe that the group behind the CVE-2018-4878 attacks is TEMP.Reaper from North Korea:
We have observed TEMP.Reaper operators directly interacting with their command and control infrastructure from IP addresses assigned to the STAR-KP network in Pyongyang. The STAR-KP network is operated as a joint venture between the North Korean Government’s Post and Telecommunications Corporation and Thailand-based Loxley Pacific.
As already mentioned, Adobe is expected to patch the flaw this week. In the meantime, if you’re running Flash Player, make sure to check whether you are prone to the exploit. How is this done? Access the About Flash Player page, or right-click on the content running in the player. Then select About Adobe Flash Player from the menu. This check should be performed for each browser installed on your system.
In addition, the importance of having an anti-malware program installed on a system should not be overlooked. Such a program will guard against malware attacks and would also remove any existing infections.
SpyHunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter