Phishing emails have been successfully fooling employers, tricking them into clicking on the provided links and thus initiating various malicious campaigns. To counter the success of phishing, many companies have started various employee trainings to help them recognize fraudulent attempts via email, social media and on the phone.
However, employees often change work places and roles, which could make these training insufficient. And on top of that, awareness and definite knowledge are two different things, as researchers point out. According to Wombat Security,“just knowing a threat exists isn’t the same as knowing how to recognize and respond to a threat when it presents itself.” In-depth education about phishing prevention is needed to create lasting behavior change, the researchers added.
What Do the Phishing Statistics Say?
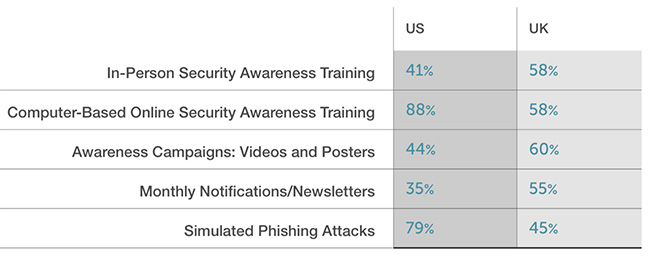
These are not just empty claims, but conclusions based on statistics from the Wombat’s latest annual report titled State of the Phish. As it turns out, in the US most organizations rely on computer-based online security awareness training where phishing attacks are simulated with the idea to train employees. In the UK, on the other hand, organizations rely on more passive approaches for training. Here are the numbers:
Apparently, US organizations are more efficient in their efforts to combat phishing as 46 percent use adequate tools twice in the week/month, whereas UK companies use these solutions in only 21 percent of the cases, the report revealed. These numbers simply mean that US companies are more adept in handling phishing.
Researchers Analyzed Data from Numerous Simulated Phishing Attacks
In their analysis, Wombat researchers used data from tens of millions simulated phishing attacks to draw some quite interesting conclusions:
- Personalized and non-personalized phishing tests are equally effective;
- Phishing emails themed with online shopping security updates, corporate voicemail from unknown callers and corporate email improvements are most tempting to employees.
- Two simulated phishing emails had the biggest click rate, almost 100 percent. One of them announced about a database password reset alert, and the other one said to contain an updated building evacuation plan.
Another interesting finding concerns the types of organizations mostly endangered by phishing attempts. As it turns out, organizations in the telecommunications, retail, consumer goods, hospitality and governments have the worst click rate of 15-13 percent. Organizations in the energy, finance, transportation and defense fields have the best click rate (8-3 percent).
The researchers also surveyed professionals in the infosec field to find out that:
- Approximately 53 percent of infosec people reported spear phishing attempts last year;
- 95 percent of organizations are training employees on phishing prevention;
- 45 percent of organizations said that there are various consequences for end users who continue to click on simulated phishing attacks.
How to Stay Protected Against Phishing
Protection against phishing attacks is basically protection against suspicious web links, malware and harmful software. Your protection comes down to the combination of security methods you apply.
To minimize the risk of phishing scams, end users should consider implementing a powerful anti-malware solution on their systems. The tips listed below also serve as great precautionary methods against phishing and malware:
- Make sure to use additional firewall protection. Downloading a second firewall is an excellent solution for any potential intrusions.
- Make sure that your programs have less administrative power over what they read and write on your computer. Make them prompt you admin access before starting.
- Use stronger passwords. Stronger passwords (preferably ones that are not words) are harder to crack by several methods, including brute forcing since it includes pass lists with relevant words.
- Turn off AutoPlay. This protects your computer from malicious executable files on USB sticks or other external memory carriers that are immediately inserted into it.
- Disable File Sharing – recommended if you need file sharing between your computer to password protect it to restrict the threat only to yourself if infected.
- Switch off any remote services – this can be devastating for business networks since it can cause a lot of damage on a massive scale.
- If you see a service or a process that is external and not Windows critical and is being exploited by hackers (Like Flash Player) disable it until there is an update that fixes the exploit.
- Make sure to download and install the critical security patches for your software and OS.
- Configure your mail server to block out and delete suspicious file attachment containing emails.
- If you have a compromised computer in your network, make sure to isolate immediately it by powering it off and disconnecting it by hand from the network.
- Turn off Infrared ports or Bluetooth – hackers love to use them to exploit devices. In case you use Bluetooth, make sure that you monitor all of the unauthorized devices that prompt you to pair with them and decline and investigate any suspicious ones.
- Employ a powerful anti-malware solution to protect yourself from any future threats automatically.
SpyHunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter