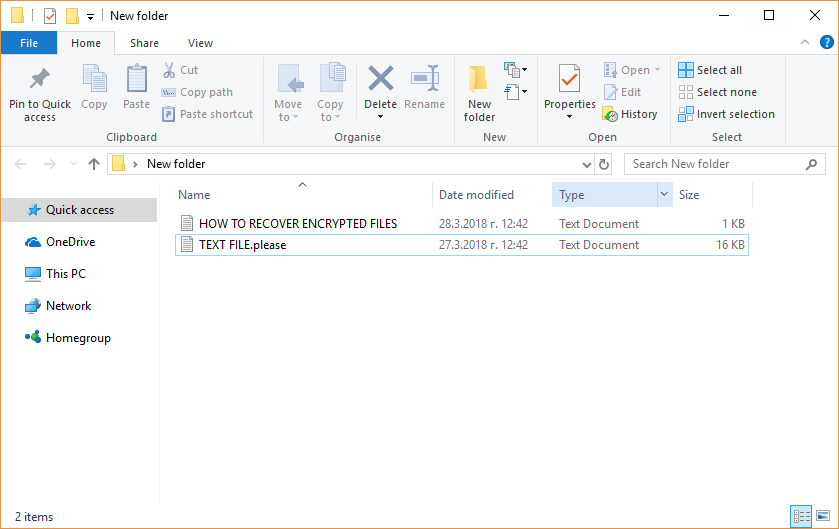
Scarab-please Virus (Scarab Ransomware) – Remove and Restore .please Files
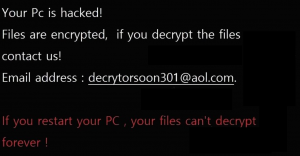
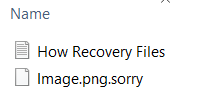
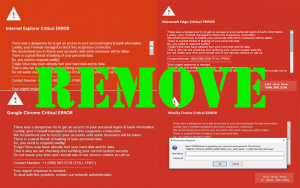
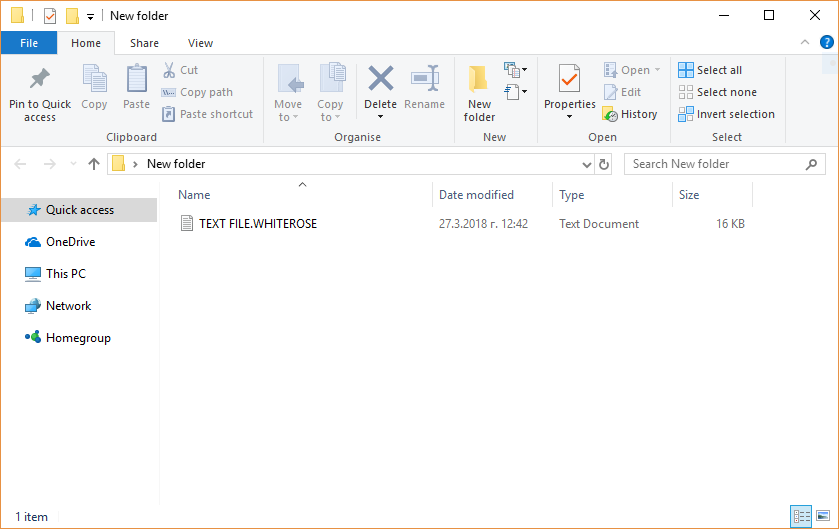
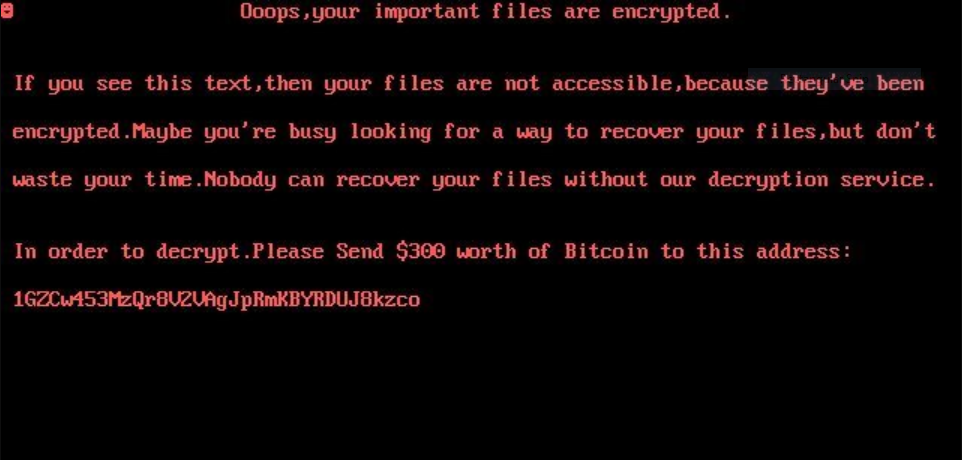
A new iteration of the Scarab malware family has been identified — the Scarab-virus. It is a classic example of a ransomware that has the ability to encrypt target data and extort the victims for a payment. Scarab-Please Virus –…