Remove PrivateMacDeal Mac Malware — Restore Instructions
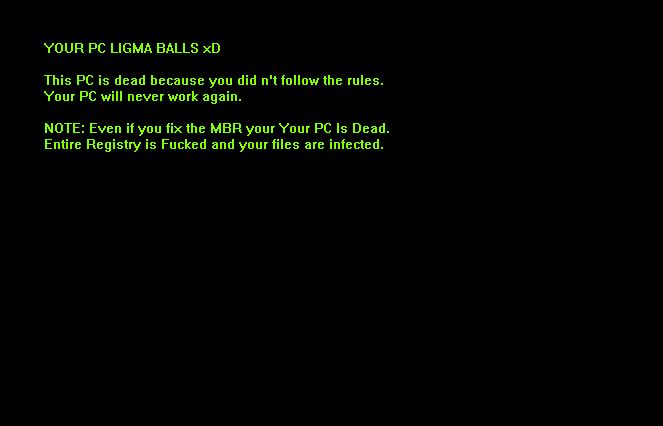
This article has been created in order to give you insight on how to quickly remove the PrivateMacDeal Mac malware from your Mac effectively. PrivateMacDeal Mac malware is a dangerous instance that targets web browsers installed on Mac computers. Infections…