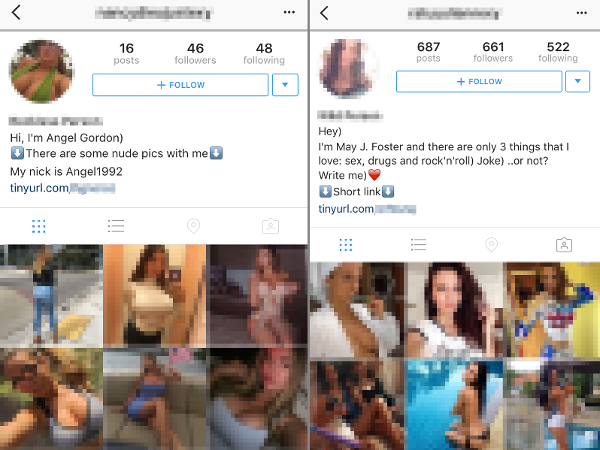
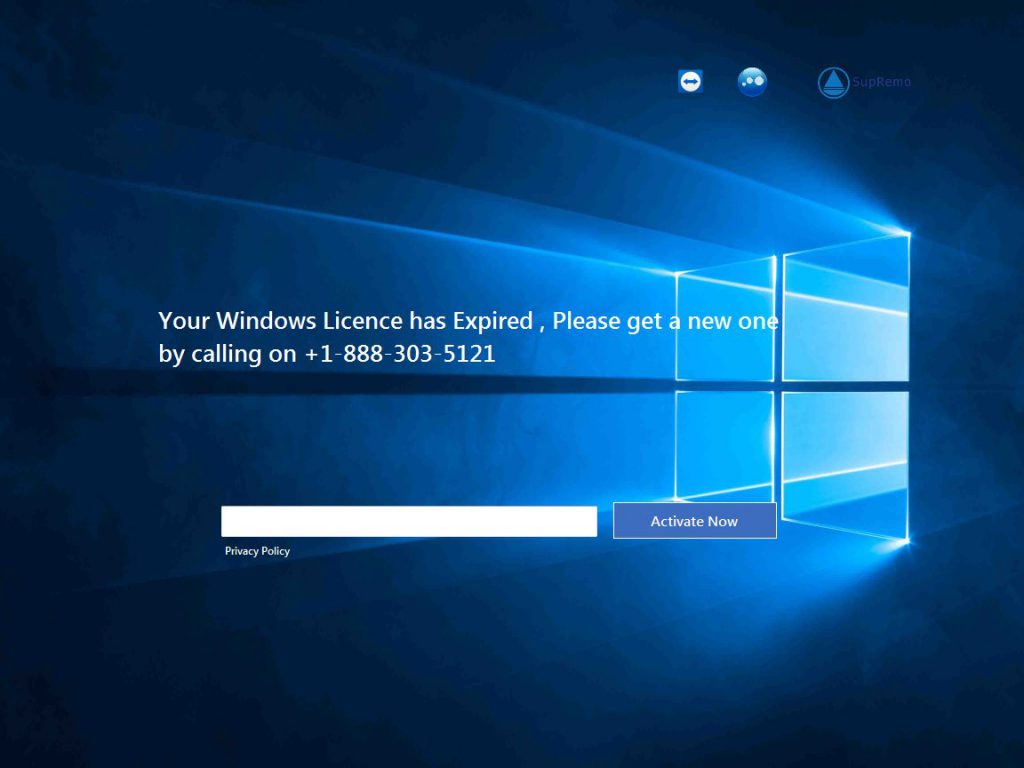
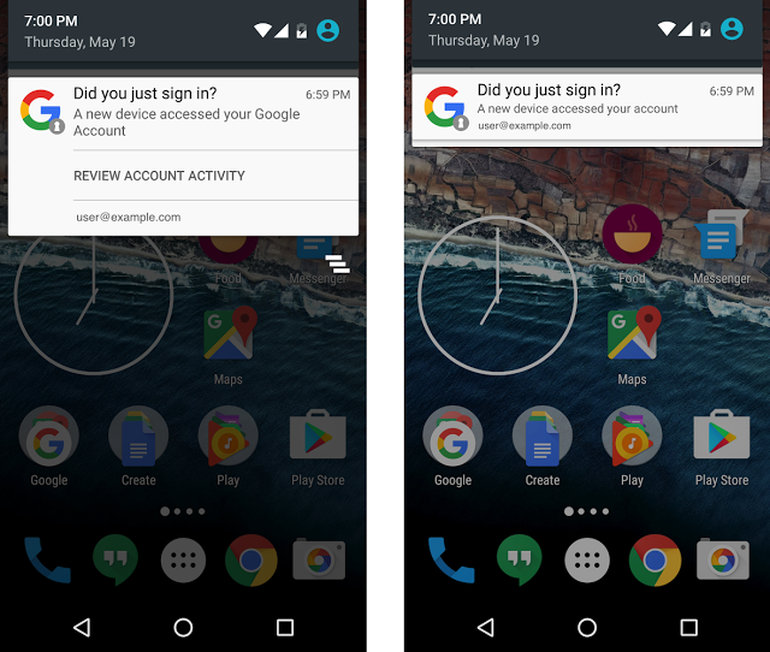
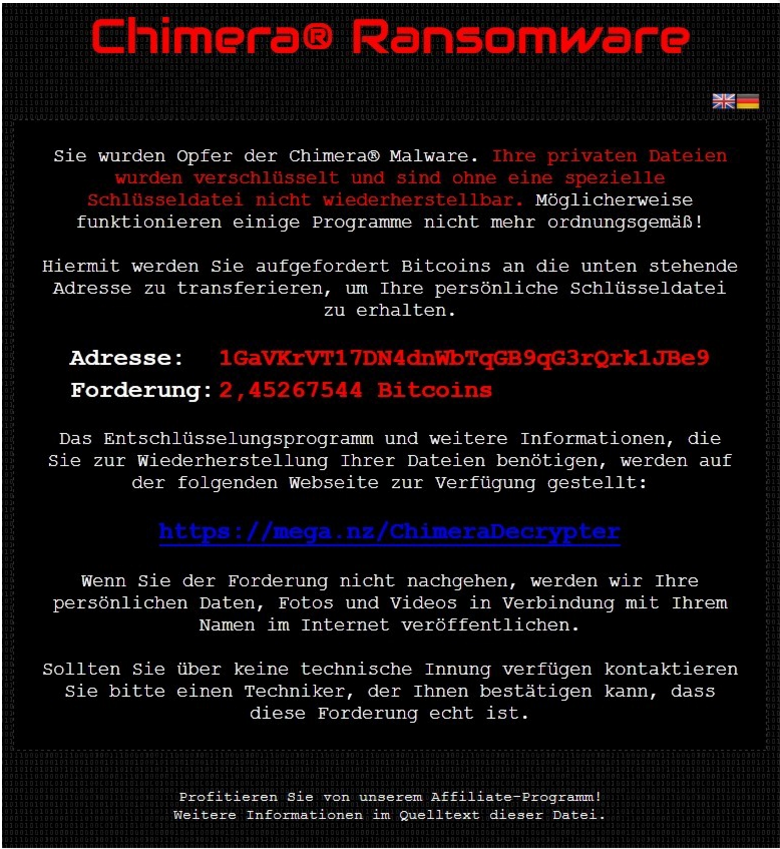
Mr. Robot Season 2 Hacks and Exploits: Master/Slave and Rubber Ducky
Have you been impatiently looking forward to Mr. Robot’s second season? Do you always have questions about the hacks that take place during the show? Are you often pausing to have a closer look at what’s written on that PC…