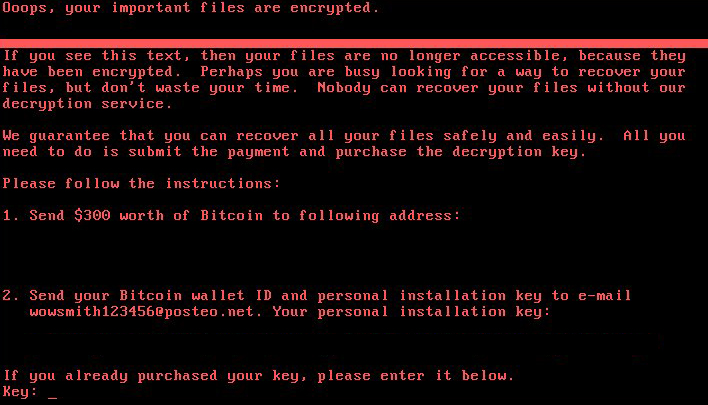
GhostCtrl Android Virus – Spying Users Worldwide
Security engineers identified the GhostCtrl Android virus family that has the ability to spy on the users at all times. The malicious code contains a fully-featured surveillance module that can record and transmit audio, video, screenshots and other sensitive data…