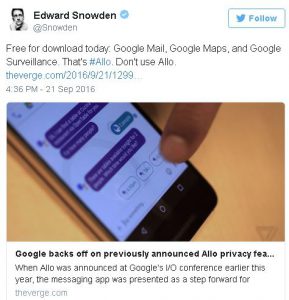
Security Concerns Emerge Over Apple’s Latest iOS 10
As with any other software which is coded by humans, there are also vulnerabilities in Apple’s latest operating system which is now available for an upgrade on the iPhone 7, iPhone 7 plus, iPhone 6, iPhone 6s, iPhone SE and…