Remove BokBot Trojan From Your PC
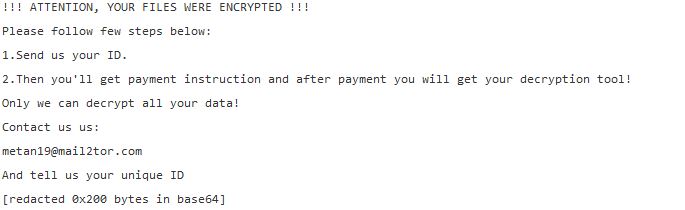
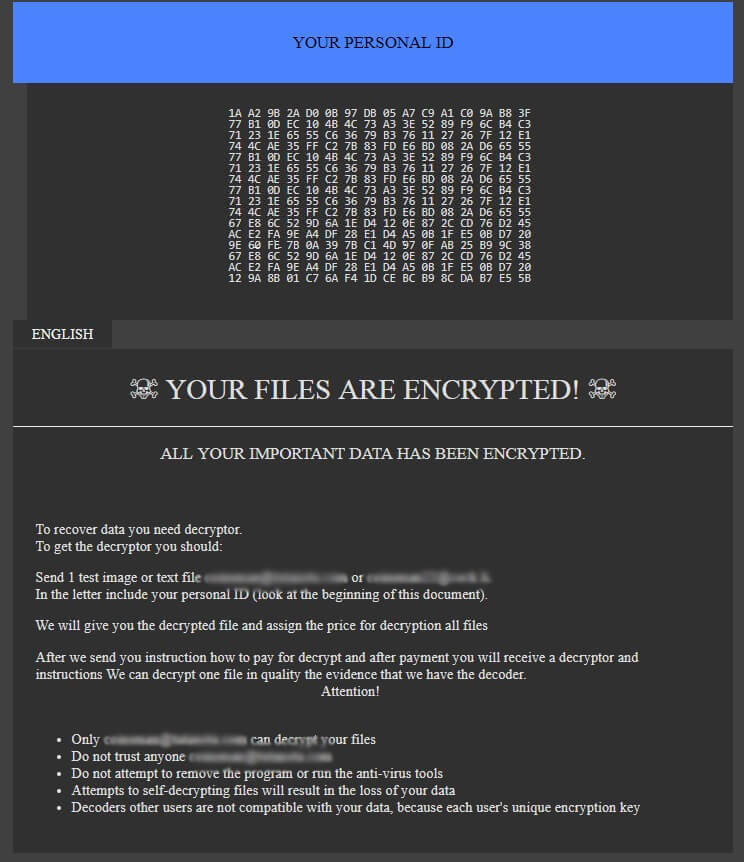
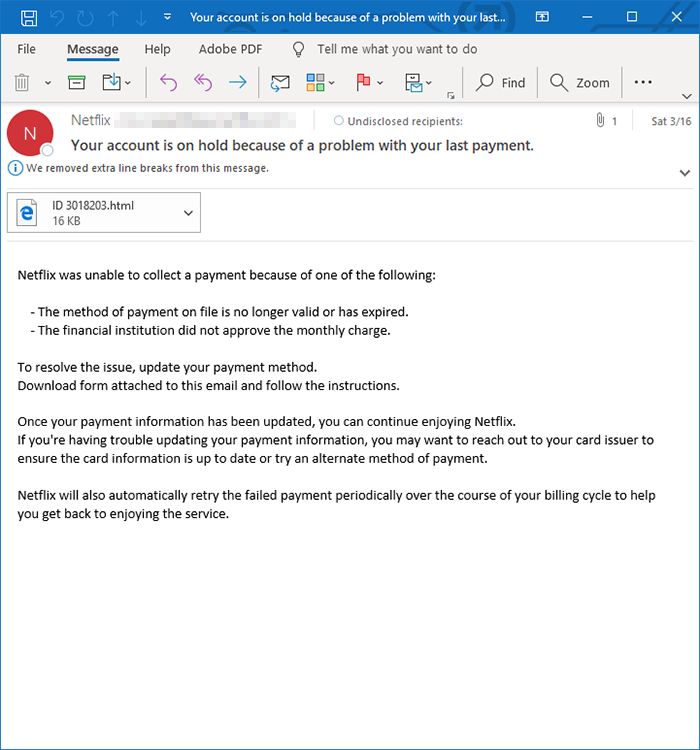
The BokBot Trojan is a dangerous weapon used against computer users worldwide. It infects via vulnerabilities and other common methods. Our article gives an overview of its behavior according to the collected samples and available reports, also it may be…













![[mrpeterson@cock.li].GFS Files (GEFEST Ransomware) – How to Remove](https://cdn.sensorstechforum.com/wp-content/uploads/2019/03/gefest-ransomware-how-to-remove-it-and-restore-gfs-encrypted-files-300x242.jpg)