
Remove “Blackmail Porn” Email Scam
Find out how to remove Blackmail Porn Scams emails, websites, pop-ups and related messages and check for malware causing them to appear. The article will also aid you to recognise some known Blackmail Porn Scams. If you suspect your computer…














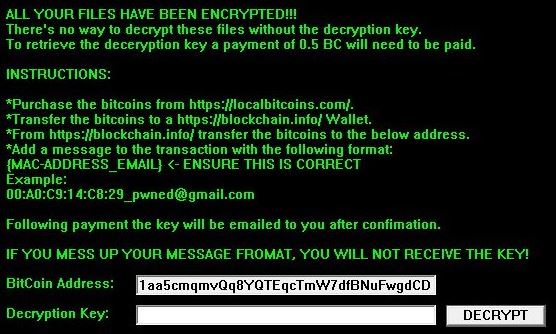








![.[Filesreturn247@gmx.de].lock Files Virus (Scarab) – Remove It and Restore Data](https://cdn.sensorstechforum.com/wp-content/uploads/2018/07/stf-remove-scarab-ransomware-and-restore-Filesreturn247@gmx.de_.lock-encrypted-files-sensorstechforum-com.png)