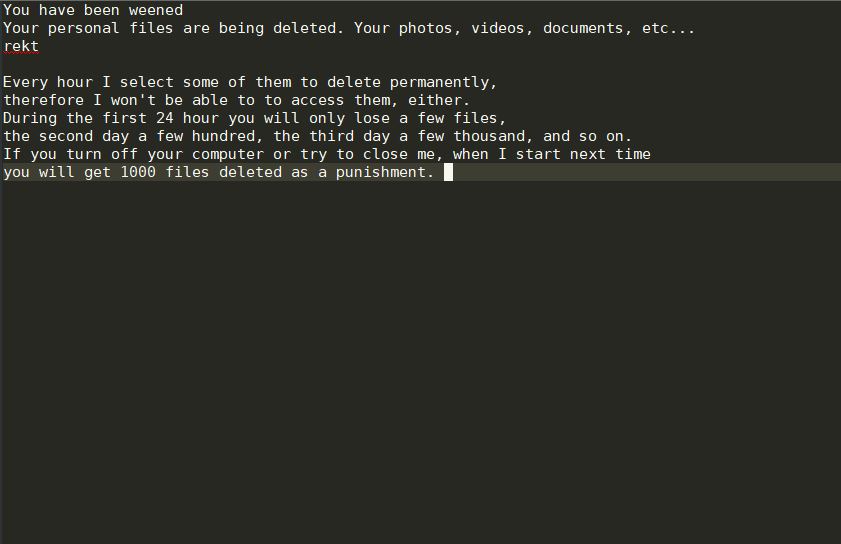
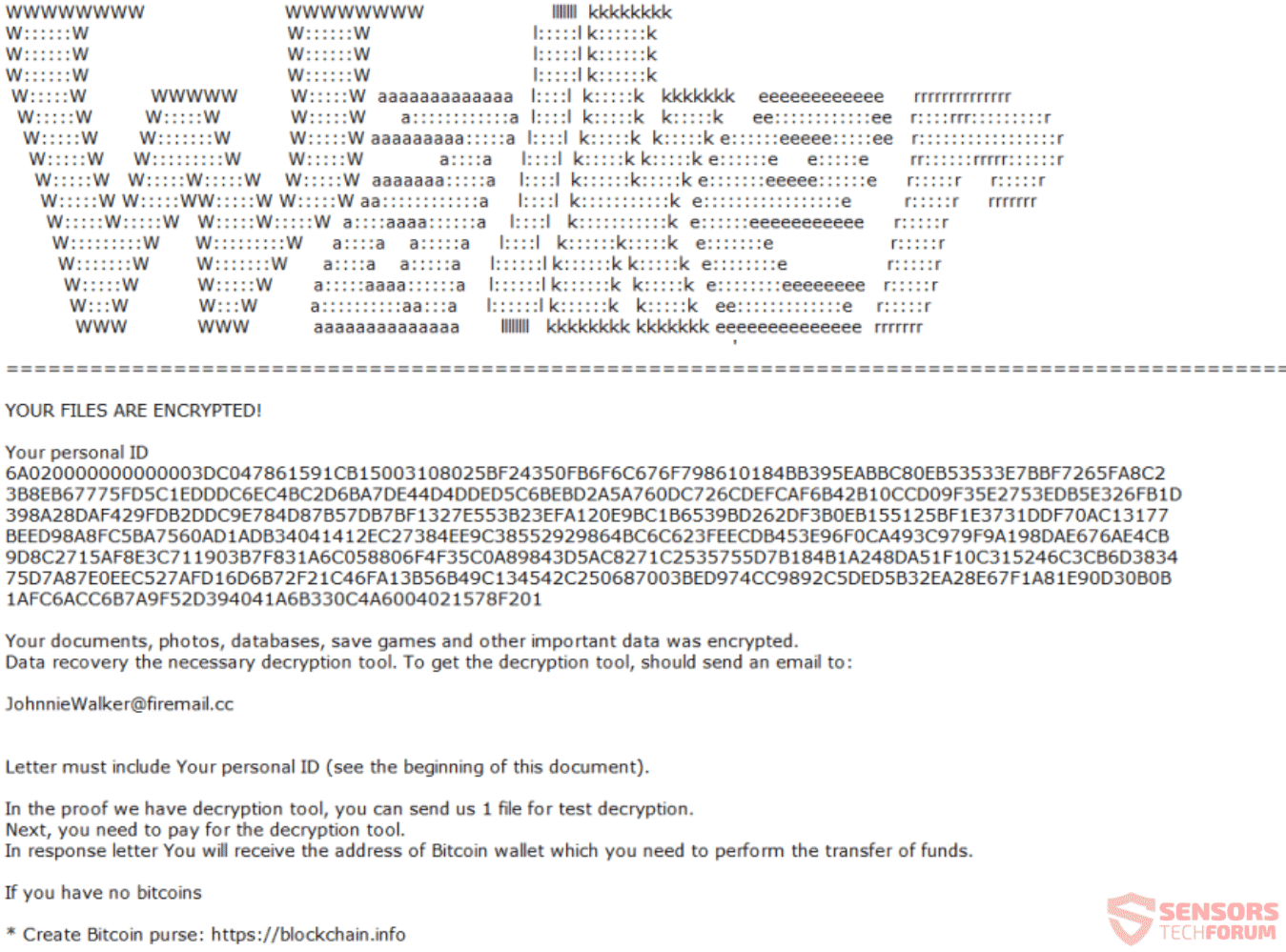
Horsuke Ransomware – Remove It and Restore .HORSE Files
This is an article that provides specific details on Horsuke ransomware infection as well as a step-by-step removal followed by alternative data recovery approaches. Horsuke is a new strain of Scarab ransomware that is now being actively distributed via different…