Here’s Why Microsoft Leaves Some Vulnerabilities Unpatched
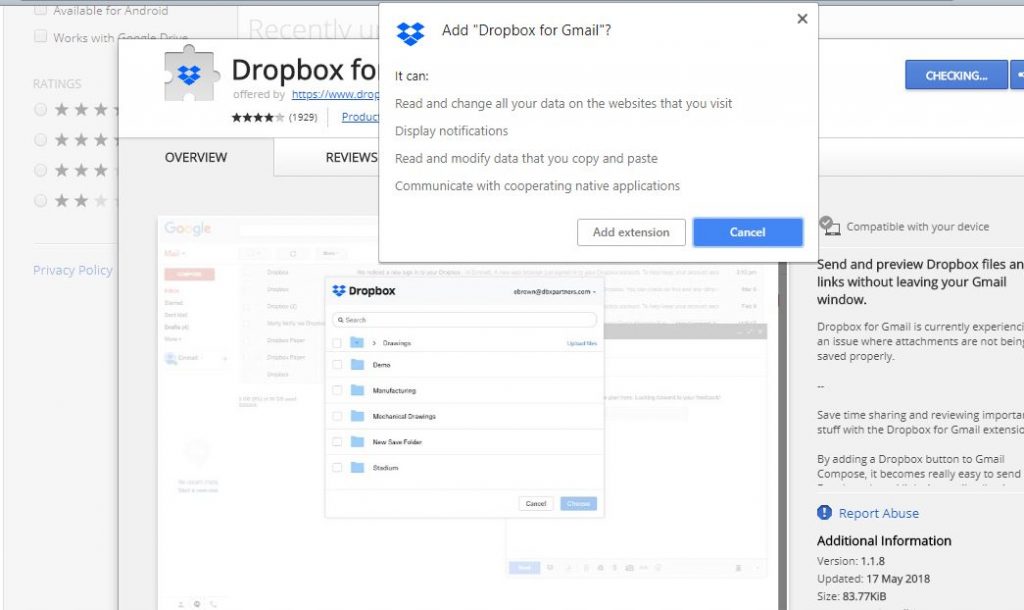
Microsoft has revealed their plans for patching exploits and how they are being handled by their security team. The details are outlined in a draft that reveals how the Microsoft Security Response Center will react according to the different severity…