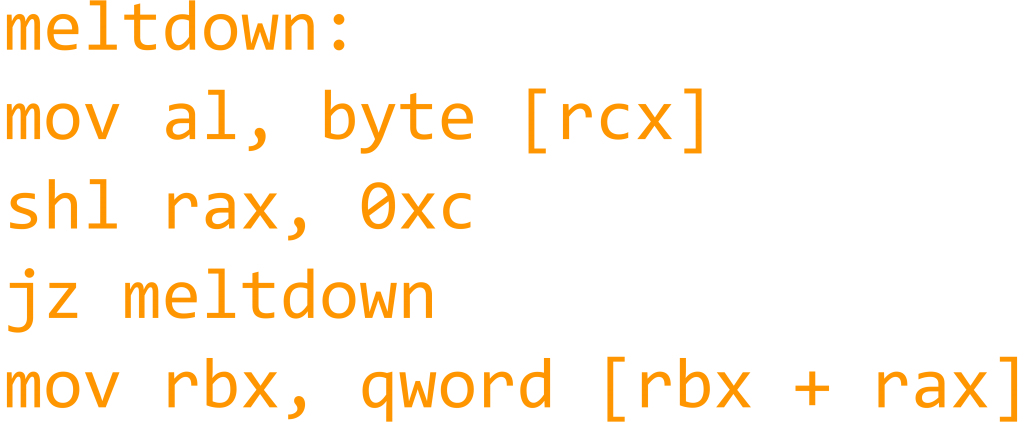KB4056892 – Emergency Windows 10 Update to Address Processor Flaws
The 2018 year started with some pretty major exploit discoveries. Named Meltdown and Spectre, these exploits are perhaps the most dangerous processor flaws that affect almost all modern processors. The security vulnerabilities affect whole generations of computers and devices of…