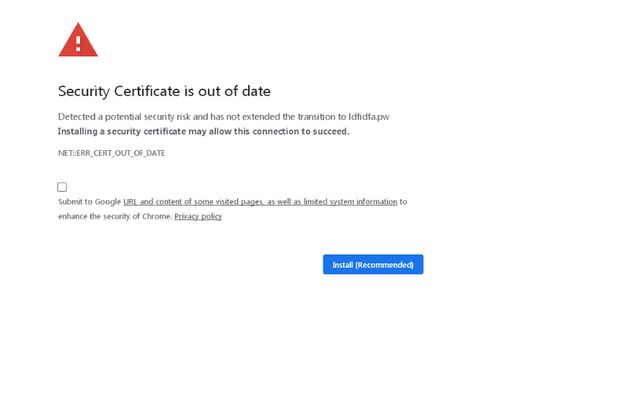
How to Block Facebook Web Trackers at the Firewall
Facebook is an American social media and social networking service that has become a household name around the world. With so many people surrendering their personal information to sign up to Facebook, it’s no wonder this social media giant now…