Researchers from CISA, ACSC, NCSC, and the FBI compiled a list of the most exploited vulnerabilities throughout 2020. Apparently, cybercriminals leveraged recently disclosed security flaws to get into vulnerable systems.
According to details available the U.S. government, most of the flaws utilized in 2020 were disclosed in the course of the past couple of years. “Cyber actor exploitation of more recently disclosed software flaws in 2020 probably stems, in part, from the expansion of remote work options amid the COVID-19 pandemic,” the researchers said. Remote work software, such as VPNs and cloud-based environments, created “additional burden” for companies to sustain a regular patching routine.
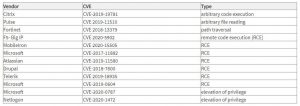
What vulnerabilities were mostly exploited in 2020?
Four of the most utilized flaws last year affected remote work software, VPNs, and cloud-based tools. “Many VPN gateway devices remained unpatched during 2020, with the growth of remote work options challenging the ability of organization to conduct rigorous patch management,” the report revealed.
One of the top most exploited vulnerabilities is Citrix’s CVE-2019-19781. The flaw resided in Citrix Gateway (NetScaler Gateway), and the Citrix Application Delivery Controller (NetScaler ADC) could expose 80,000 companies to hacks.
It is worth mentioning that, as soon as CVE-2019-19781 was brought to the public’s attention, some 80,000 predominantly North American companies (with many companies across 158 countries) were running vulnerable installations. The at-risk companies were predominantly located in the Netherlands, Australia, United Kingdom, Germany, and the United States.
The Pulse VPN CVE 2019-11510 is another vulnerability cybercriminals used a lot during 2020. The CVE-2019-11510 vulnerability was used in real-time attacks against VPN providers. The flaw was classified as an “authentication by-pass vulnerability” that could allow non-authenticated users to access files on the service’s gateway. On affected systems, this would trigger remote code execution.
CVE-2018-13379 in the FortiOS SSL VPN web portal could potentially allow an unauthenticated attacker to download files through specially crafted HTTP resource requests. It is also on the top exploited list of 2020. It is worth mentioning that the Fortinet bug was used in combination with CVE-2020-1472, an elevation of privilege flaw triggered by an attacker who establishes a vulnerable Netlogon secure channel connection to a domain controller.
The CVE 2020-5902 security vulnerability was identified in the first week of July 2020 and was identified as a critical, remote code execution issue found in the BIG-IP network implementation. The weakness is part of the management interface of the suite – apparently, a mitigation rule in the Apache web server configuration file could allow remote attackers to exploit the service. This is done by inserting a semicolon request via the URL, where the web server would interpret this as a command finished toggle. In other words, by using a simple URL manipulation, hackers could issue commands to the remote host.
Another example of a widely adopted flaw is CVE-2017-11882. The exploit allowed attackers to automatically run malicious code without the need of any user interaction. According to its official description, Microsoft Office 2007 Service Pack 3, Microsoft Office 2010 Service Pack 2, Microsoft Office 2013 Service Pack 1, and Microsoft Office 2016 could allow an attacker to run arbitrary code in the context of the current user by failing to properly handle objects in.
We remind you how crucial it is to apply all security patches as soon as they are made available by the specific vendor.