Thermanator Attack Uses Thermal Residue from Keyboards to Steal Your Passwords
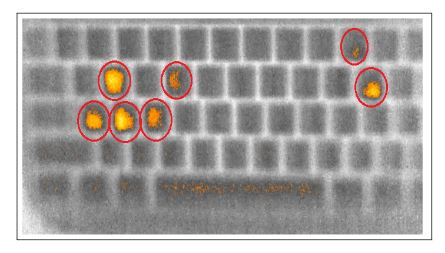
A new type of attack could allow a malicious actor with a mid-range thermal camera to capture keys pressed on a standard keyboard. The discovery has been made by three University of California professors. In other words, our fingers’ thermal…