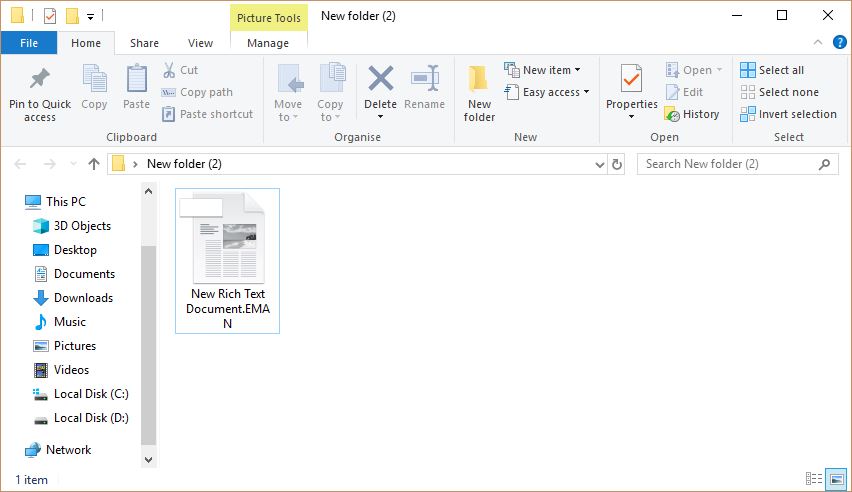
Remove Matrix Ransomware and Restore .EMAN Files
This article will aid you remove Matrix Ransomware effectively. Follow the removal instructions at the end. The .EMAN Matrix Ransomware is the newest strain associated with the Matrix family of malware. Like previous versions it has an extensive list of…